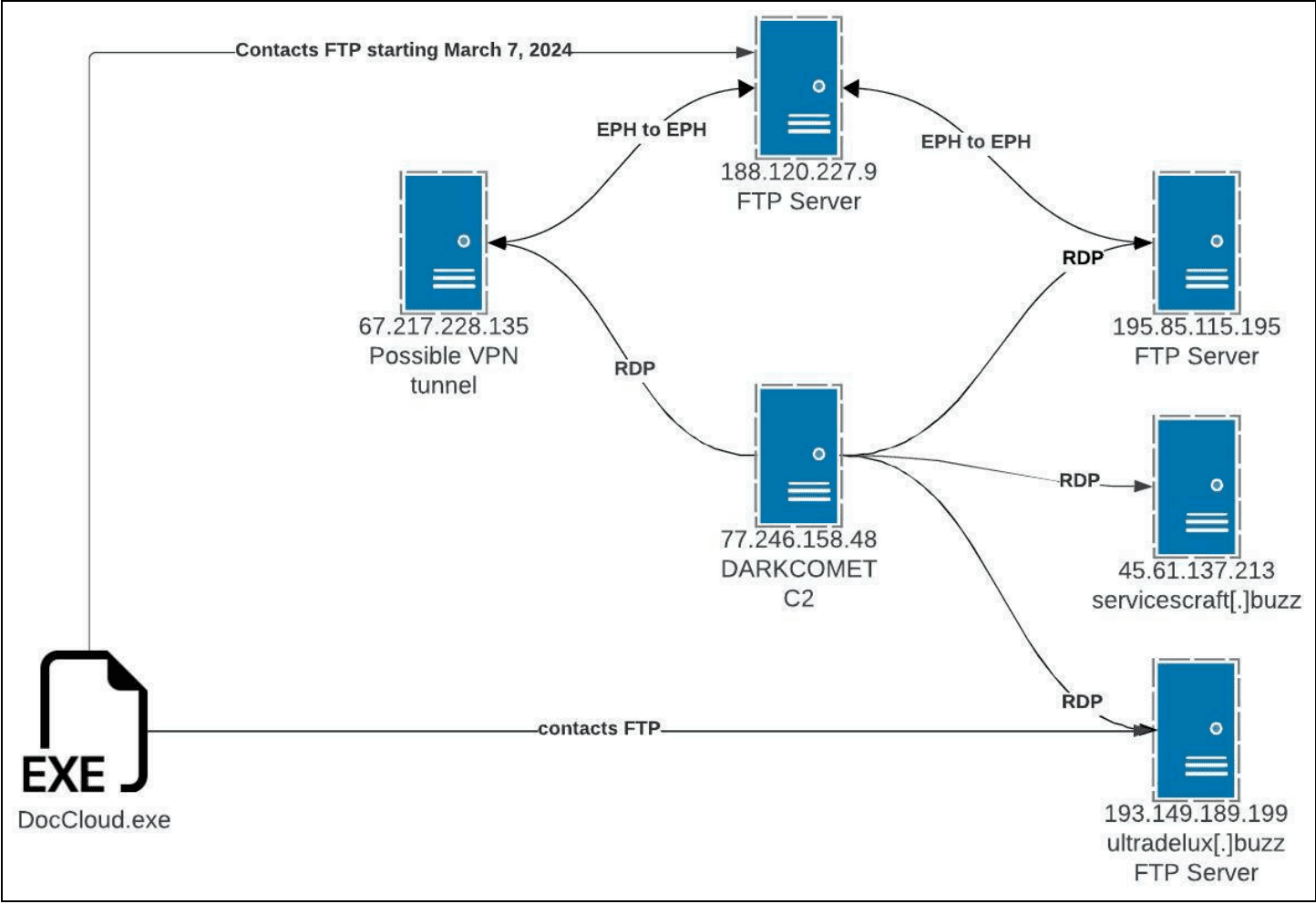
Graphical interpretation of the threat actor’s network infrastructure (Source: Recorded Future)
Recorded Future’s Insikt Group has uncovered a significant cyber threat campaign attributed to Russian-speaking threat actors, likely based in the Commonwealth of Independent States (CIS). The campaign exploits GitHub, a legitimate platform for software development, to distribute various malware families. This report details how the threat actors use GitHub to impersonate popular software like 1Password, Bartender 5, and Pixelmator Pro, thereby infecting victims with information-stealing malware such as AMOS, Vidar, Lumma, and Octo. The shared command-and-control (C2) infrastructure among these malware variants suggests a highly coordinated attack strategy aimed at maximizing impact across different platforms.

The threat actors create GitHub profiles to host and distribute malware-laced versions of popular software. Once a user downloads and installs these tainted applications, their device becomes infected with dangerous malware capable of stealing personal data and performing unauthorized actions. The campaign shows the attackers’ adaptability and the extensive use of shared command-and-control (C2) systems, suggesting a well-organized and centrally controlled cyber attack operation.
Insikt Group’s detailed analysis led to the discovery of multiple malware families within this campaign, including:
- Atomic macOS Stealer (AMOS): Targets macOS users by impersonating commonly used applications.
- Vidar and Lumma: Information stealers that target Windows devices.
- Octo: A banking trojan specifically targeting Android devices.
All these malware types show how the attackers use GitHub to manage their malicious tools effectively and strike a wide range of targets across different operating systems.
The campaign involves intricate tactics like domain spoofing, where users are redirected from seemingly benign websites to malicious GitHub repositories. The malware often prompts a download under the guise of necessary software updates or additional required software, tricking the user into initiating the download themselves.
Insikt Group also uncovered the backend infrastructure used in this campaign, including multiple C2 servers and the use of public file-sharing services like Dropbox and Pixeldrain to spread additional payloads. The usage of FileZilla servers for managing and disseminating malware variants highlights the campaign’s sophistication.
Insikt Group recommends several mitigation strategies, including:
- Verify the authenticity of the download sources and maintain updated antivirus and anti-malware solutions.
- Employ tools like GitGuardian and GitHub Advanced Security to scan for potentially malicious code.
- Implement an organization-wide code review process for any externally obtained code before its integration into production environments.