
Since September 2023, security researchers from Cisco Talos have observed a sharp increase in malicious emails designed to infect victims with banking trojans. Of particular concern is the exploitation of Google Cloud Run for payload delivery. These campaigns focus heavily on Latin America, notably targeting victims with the notorious Astaroth, Mekotio, and Ousaban trojans. However, victims in Europe and North America are being impacted as well, suggesting a potential broadening of attack targets.
Google Cloud Run, a haven for developers seeking to deploy web services swiftly, has been hijacked as a launchpad for these malicious campaigns. Offering $300 in free credits and two million web requests per month, it’s a bargain bin for cybercriminals to establish their distribution infrastructure, with the added advantage of evading internal security barriers within many organizations. The administrative dashboards, detailed metrics, and an API for rapid deployment become double-edged swords, facilitating a quick change of tactics as soon as their malicious applications are flagged and removed.
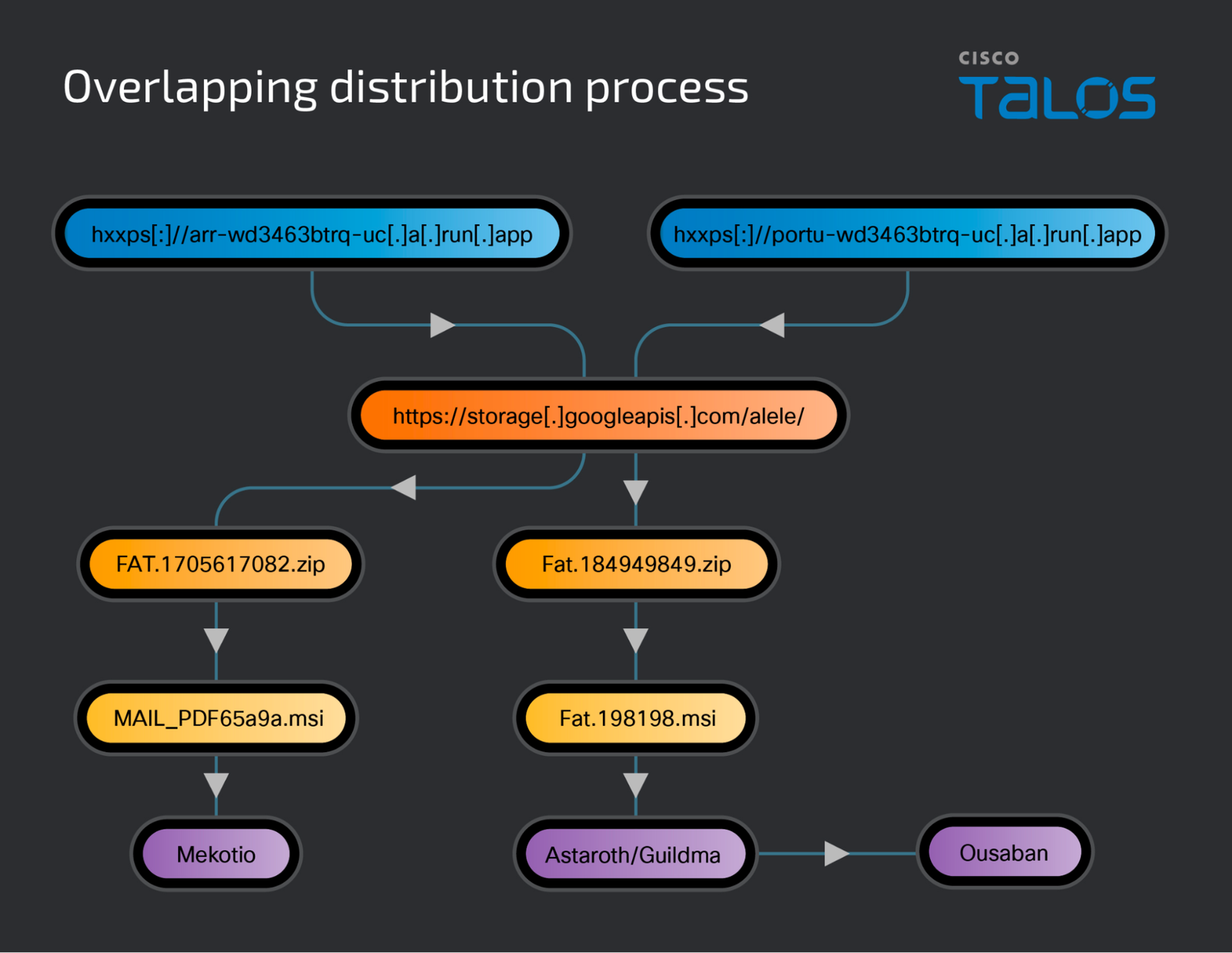
Phishing emails remain the primary vector. Impersonating trusted financial institutions, government tax agencies, or other recognized entities, these emails contain carefully crafted language designed to instill urgency and prompt action. Links within the emails often leverage Google’s “run[.]app” top-level domain to add a veneer of legitimacy.
An unsuspecting click on the link redirects the victim to a Google Cloud Run site or Google Cloud Storage, deploying a carefully obfuscated malicious package. Microsoft Installer (MSI) files and compressed archives have emerged as favored attack vehicles.

Sophisticated campaigns combine cloaking and filtering techniques. Geofencing (geolocation checks) restricts attacks to specific regions. Browser and device fingerprinting help tailor infections and hinder analysis efforts.
Cloud Run campaigns have aggressively deployed an arsenal of banking trojans:
- Astaroth: A Latin American menace. Its hyperfocus on targeting over 300 financial institutions across 15 countries demonstrates the regional appeal of this trojan. Astaroth combines potent screen-capture functions tailored to defeat virtual keyboard defenses with targeted keylogging.
- Mekotio: Like Astaroth, Mekotio has established a strong foothold in Latin America. Before an infection, it diligently checks the victim’s geographic location to ensure it aligns with its goals.
- Ousaban: A rising threat recently observed in tandem with Astaroth infections. This suggests potential shared infrastructure or coordination between different threat groups.
The simultaneous delivery of these trojans from a single Google Cloud bucket, coupled with overlapping tactics, suggests a sinister possibility of collaboration or at least a shared platform among the threat actors. This revelation hinted at in a VirusBulletin paper, adds a layer of complexity to the already intricate web of cyber threats.
The escalation of banking trojan attacks and their weaponization of trusted cloud services reinforces the ever-changing threat landscape. Vigilance, knowledge-sharing, and a commitment to best practices will help defend against the relentless assaults that seek to undermine financial security.