TLS-Attacker v5.3 released: Java-based framework for analyzing TLS libraries
TLS Attacker
TLS-Attacker is a Java-based framework for analyzing TLS libraries. It is able to send arbitrary protocol messages in an arbitrary order to the TLS peer, and define their modifications using a provided interface. This gives the developer an opportunity to easily define a custom TLS protocol flow and test it against his TLS library.
Please note: TLS-Attacker is a research tool intended for TLS developers and pentesters. There is no GUI and no green/red lights. It is the first version and can contain some bugs.
Code Structure
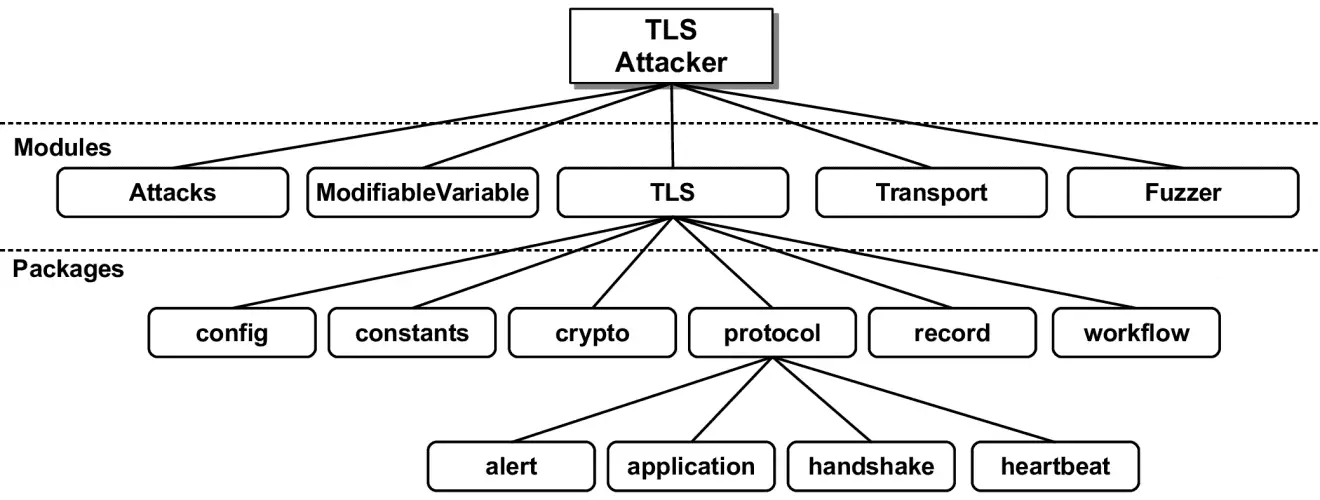
TLS-Attacker consists of several (maven) projects:
- Transport: Transport utilities for TCP and UDP.
- ModifiableVariable: Contains modifiable variables that allow one to execute (specific as well as random) variable modifications during the protocol flow. ModifiableVariables are used in the protocol messages.
- TLS: Protocol implementation, currently (D)TLS1.2 compatible.
- Attacks: Implementation of some well-known attacks and tests for these attacks.
- Fuzzer: Fuzzing framework implemented on top of the TLS-Attacker functionality.
You can find more information about these modules in the Wiki.
Features
Currently, the following features are supported:
- SSL 3, TLS versions 1.0 (RFC-2246), 1.1 (RFC-4346), 1.2 (RFC-5246), and 1.3 (RFC-8446)
- SSL 2 (Partially supported)
- (EC)DH(E), RSA, PSK, SRP, GOST and ANON key exchange algorithms
- CBC, AEAD and Streamciphers (AES, CAMELLIA, DES, 3DES, IDEA, RC2, ARIA, GOST_28147_CNT_IMIT, RC4, SEED, NULL)
- ~300 Cipher suites, ~30 Extensions
- Client and Server
- HTTPS
- Workflows with more than two parties
- Lots of extensions
- Tokenbinding (EC) and Tokenbinding over HTTP
- Sockets
- TLS 1.3 0-RTT
- STARTTLS
- …
Protocol-Attacker/Layer System
Originally designed to attack the TLS protocol, TLS-Attacker is capable of supporting arbitrary protocols. To this end, TLS-Attacker assigns a layer stack to each connection. This layer stack consists of the different protocol layers the user wants to utilize. With the layer stack, the user can add layers like DTLS, or HTTP (more are WIP) in an arbitrary order.
To send and receive arbitrary messages using a layer stack, the user can define configurations for each layer. These configurations specifiy which messages to send or receive. This also allows the user to specify the layer specific messages/data containers for each layer. For example, one could specify the TLS messages and records TLS-Attacker should send. TLS-Attacker would encapsulate the given TLS messages into the records automatically.
Changelog v5.3
- Added support for chinese SM cipher suites in TLS 1.3
- Fixed encryption issue when using client authentication in TLS 1.3
- Fixed a bug for reexecuted WorkflowTraces caused by manipulated LayerConfiguration
- Fixed a bug which caused only the first pre-defined DTLS fragment to be used by the DtlsFragmentLayer
Compiling and Running
In order to compile and use TLS-Attacker, you need to have Java installed. Run the maven command from the TLS-Attacker directory:
$ git clone https://github.com/RUB-NDS/TLS-Attacker.git
$ cd TLS-Attacker
$ ./mvnw clean package
Alternatively, if you are in a hurry, you can skip the tests by using:
$ mvn clean install -DskipTests=true
Source: https://github.com/RUB-NDS/