PIF event flow | Image: hunt.io
Cyber espionage continues to intertwine with global strategy as the ToneShell backdoor, linked to the notorious Mustang Panda group, reemerges. In a recent report from Hunt.io, cybersecurity researchers discovered the malware targeting attendees of the 2024 International Institute for Strategic Studies (IISS) Defence Summit in Prague.
Mustang Panda, also known as Stately Taurus and Earth Preta, is a well-known advanced persistent threat (APT) group with a history of targeting government organizations across Southeast and East Asia. Their weapon of choice, the ToneShell backdoor, allows attackers to stealthily infiltrate networks, exfiltrate data, and execute malicious payloads. In this latest operation, ToneShell backdoor has been deployed against attendees of the IISS Defence Summit, a major gathering of global defense and security leaders.
The IISS Defence Summit, scheduled for November 8-10, 2024, is set to become a crucial forum for discussing defense strategies and security concerns within the Euro-Atlantic region. Attendees include senior political leaders, defense ministers, and policymakers from Europe, the U.S., and allied nations. The sensitive nature of these discussions—covering topics such as military cooperation, geopolitical tensions, and defense capacity-building—makes the summit an attractive target for cyber espionage.
Gaining access to these conversations offers adversaries a significant advantage, revealing defense strategies and the positions of key global players. The involvement of high-level officials further increases the potential intelligence value of the operation.
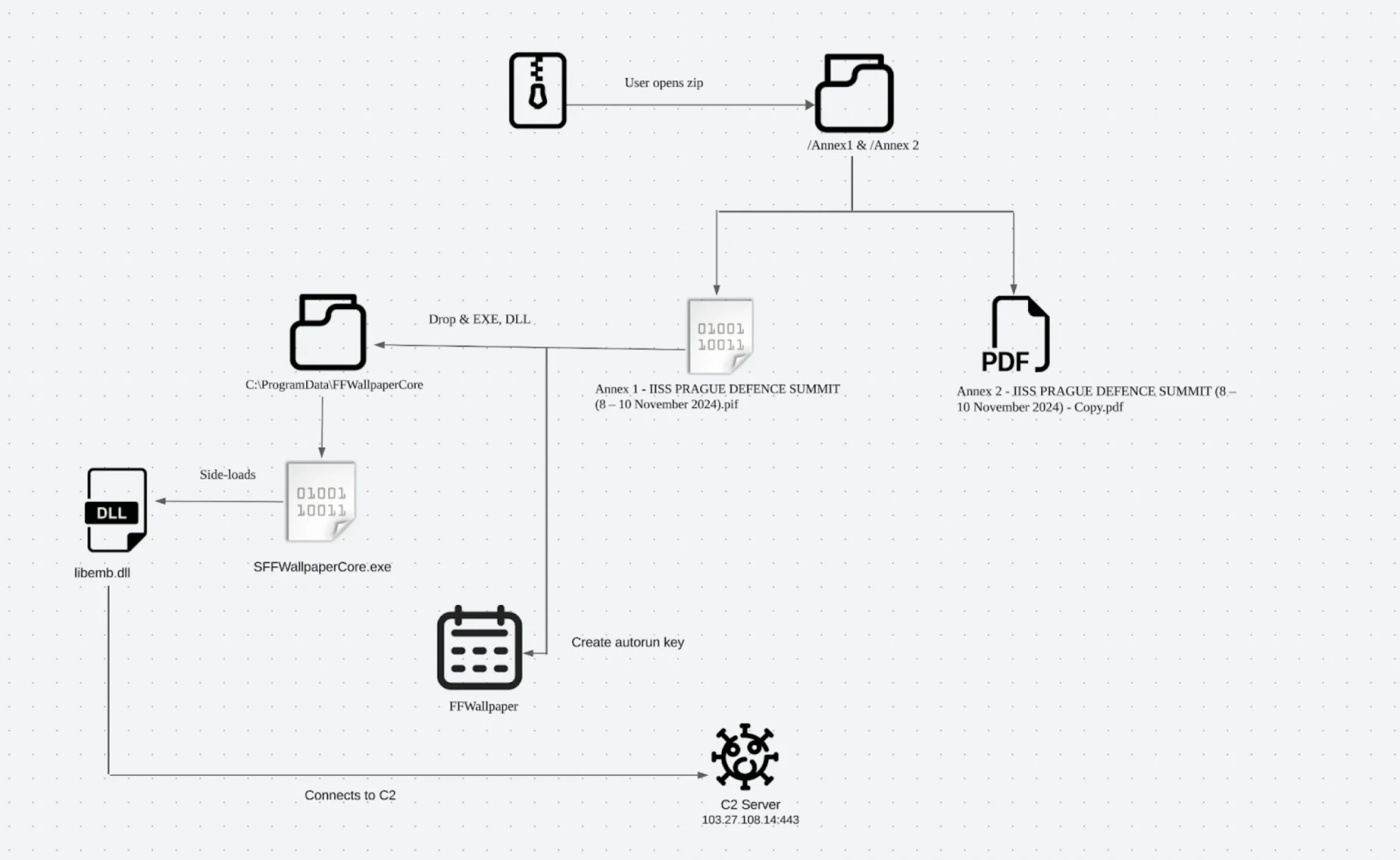
During routine analysis on the Hatching Triage platform, researchers uncovered an executable file, “IISS PRAGUE DEFENCE SUMMIT (8 – 10 November 2024 ).exe,” uploaded in August. Upon further investigation, it became evident that the file was linked to ToneShell activity. The malware communicated with a command-and-control (C2) server using familiar markers, such as the magic bytes “17 03 03,” often associated with ToneShell and PubLoad malware.
The attackers used a decoy document—an exact replica of an official agenda from the IISS website—designed to lure victims into believing the file was legitimate. While the decoy document loaded, the malware silently operated in the background, establishing persistence and setting up communication with its C2 server.
The malware’s dropper, disguised as a PIF file (Program Information File), executed malicious code upon being opened. This technique is commonly used by threat actors to bypass detection systems. Upon execution, the malware established persistence through the creation of a registry run key and a scheduled task, ensuring it would continue to operate after system reboots.
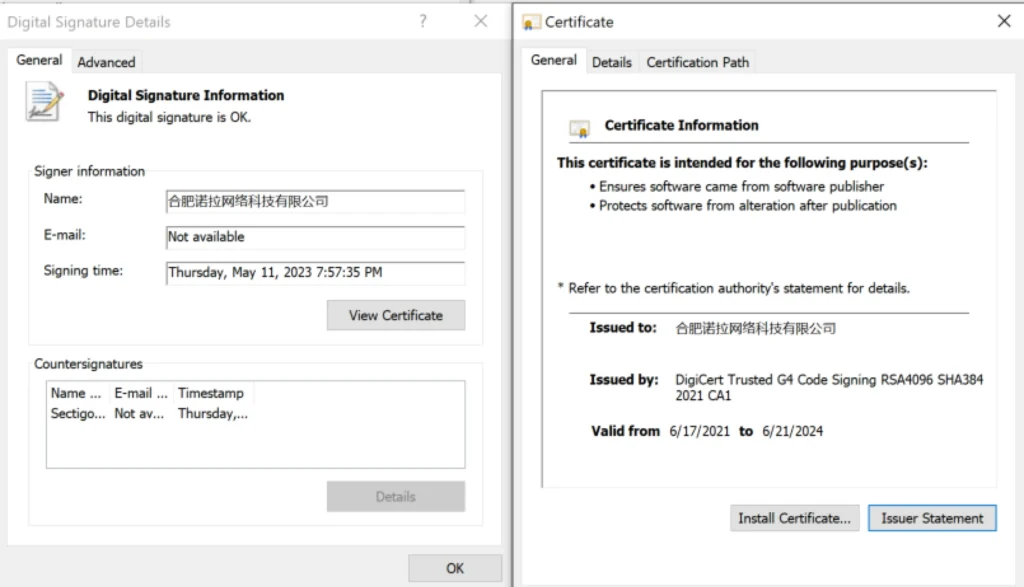
The malware dropped a secondary executable, SFFWallpaperCore.exe, and a dynamic-link library (DLL) file, libemb.dll, to further its objectives. The DLL, signed by a suspicious Chinese company, featured unique debug strings that have become a hallmark of Mustang Panda’s attacks.
Network traffic analysis revealed that the malware communicated with its C2 server via port 443 using raw TCP, mimicking TLS to evade detection. This tactic has been consistently observed in previous Mustang Panda campaigns.
The C2 server, hosted by Topway Global Limited’s ASN in Hong Kong, had ports 80, 443, and 3389 accessible. Notably, the C2 server briefly presented a self-signed Remote Desktop Protocol (RDP) certificate, a known indicator of Mustang Panda infrastructure. Further investigation uncovered seven additional servers sharing similar characteristics, suggesting a coordinated effort by the same threat actor.
While the C2 IP address had not yet been flagged as malicious on VirusTotal, its proximity to other suspicious IPs and infrastructure hosted in Hong Kong strengthens the link to Mustang Panda.
Related Posts:
- China-Linked Mustang Panda Targets Vietnamese Entities in Cyber Espionage Campaign
- Windows Endpoint Security Summit: Microsoft and CrowdStrike Unite to Protect Critical Infrastructure
- Beyond Firewalls: NCSC Explores Cyber Deception’s Potential
- Australia’s Defence Department ban WeChat app due to worry about Chinese espionage activities
- PANDA Banker Malware Attacks Bank Institutions, Cryptocurrency Trading Platforms, and Social Media