Top 7 Nmap NSE Scripts for Recon
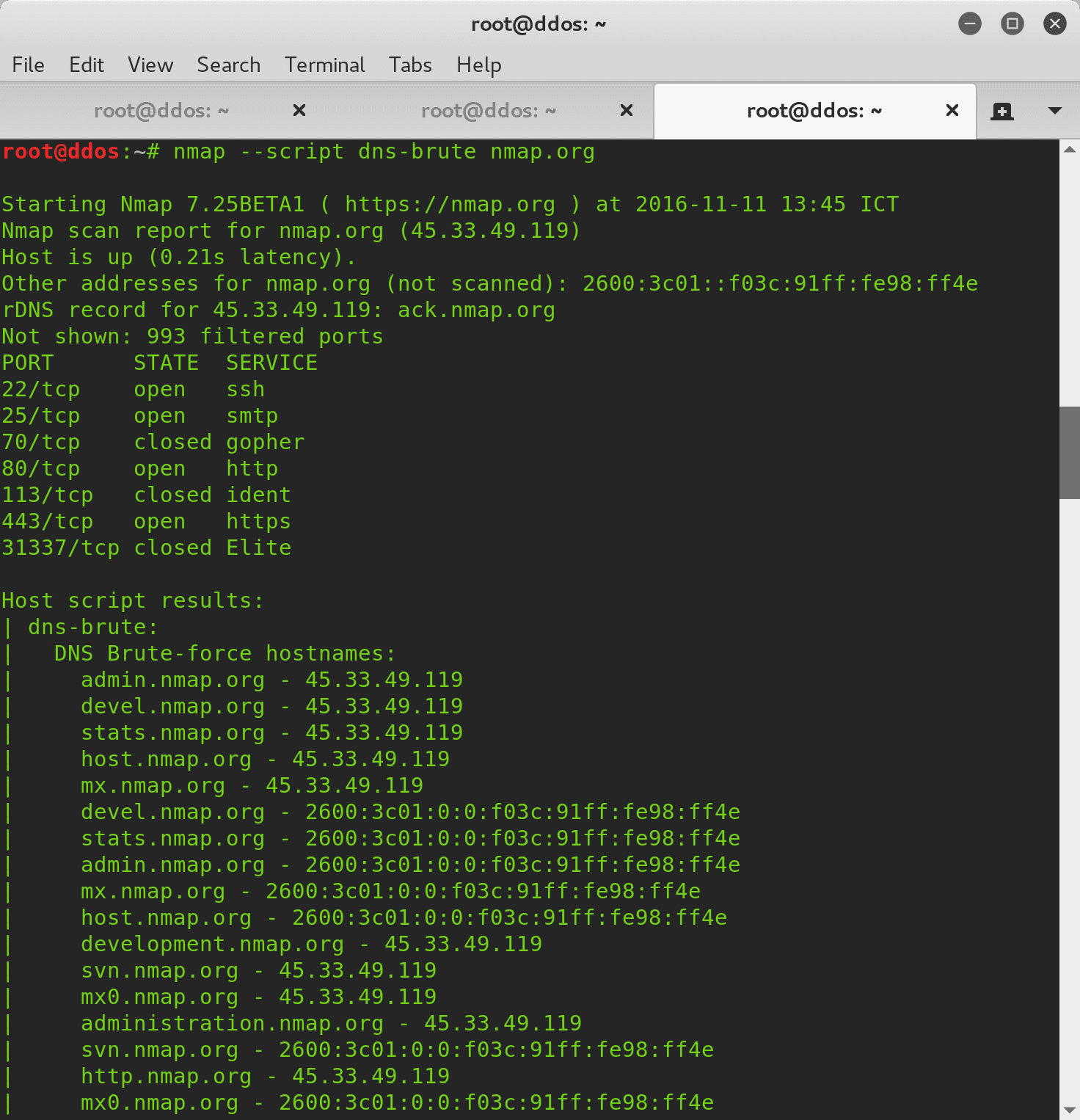
- dns-brute.nse
Attempts to enumerate DNS hostnames by brute force guessing of common subdomains. With the dns-brute.srv argument, dns-brute will also try to enumerate common DNS SRV records. - traceroute-geolocation.nse
Lists the geographic locations of each hop in a traceroute and optionally saves the results to a KML file, plottable on Google earth and maps. - firewalk.nse
Tries to discover firewall rules using an IP TTL expiration technique known as firewalking. To determine a rule on a given gateway, the scanner sends a probe to a metric located behind the gateway, with a TTL one higher than the gateway. If the probe is forwarded by the gateway, then we can expect to receive an ICMP_TIME_EXCEEDED reply from the gateway next hop router, or eventually the metric itself if it is directly connected to the gateway. Otherwise, the probe will timeout.It starts with a TTL equals to the distance to the target. If the probe timeout, then it is resent with a TTL decreased by one. If we get an ICMP_TIME_EXCEEDED, then the scan is over for this probe.Every “no-reply” filtered TCP and UDP ports are probed. As for UDP scans, this process can be quite slow if lots of ports are blocked by a gateway close to the scanner.Scan parameters can be controlled using the <code>firewalk.*</code> optional arguments. From an original idea of M. Schiffman and D. Goldsmith, authors of the firewalk tool. - http-sitemap-generator.nseSpiders a web server and displays its directory structure along with number and types of files in each folder. Note that files listed as
having an ‘Other’ extension are ones that have no extension or that are a root document. - http-methods.nse
Finds out what options are supported by an HTTP server by sending an OPTIONS request. Lists potentially risky methods. It tests those methods not mentioned in the OPTIONS headers individually and sees if they are implemented. Any output other than 501/405 suggests that the method is if not in the range 400 to 600. If the response falls under that range then it is compared to the response from a randomly generated method.In this script, “potentially risky” methods are anything except GET, HEAD, POST, and OPTIONS. If the script reports potentially risky methods, they may not all be security risks, but you should check to make sure. This page lists the dangers of some common methods: http://www.owasp.org/index.php/Testing_for_HTTP_Methods_and_XST_%28OWASP-CM-008%29The list of supported methods comes from the contents of the Allow and Public header fields. In verbose mode, a list of all methods is printed, followed by the list of potentially risky methods. Without verbose mode, only the potentially risky methods are shown. - whois-domain.nse
This script starts by querying the whois.iana.org (which is the root of the whois servers). Using some patterns the script can determine if the response represents a referral to a record hosted elsewhere. If that’s the case it will query that referral. The script keeps repeating this until the response don’t match with any of the patterns, meaning that there are no other referrals and prints the output.
- shodan-api.nse
Queries Shodan API for given targets and produces similar output to a -sV nmap scan. The ShodanAPI key can be set with the ‘apikey’ script argument, or hardcoded in the .nse file itself. You can get a free key from https://developer.shodan.ioN.B if you want this script to run completely passively make sure to include the -sn -Pn -n flags.
Tutorial
https://www.youtube.com/watch?v=WaLrqyNCC8o





