Trend Micro posted a blog on Wednesday that their network monitoring system recently detected a large-scale scanning activity that appears to be coming from the Mirai botnet. Specifically, during the period from 1 pm on March 31 to 10 am on April 3, a total of 3,423 IP addresses located within China’s territory were found to have participated in the scan. The target is a networked device located in Brazil, which mainly includes optical modems, routers, and web cameras.
Trend Micro indicated that this scanning behavior is very similar to the scanning mechanism of the Mirai botnet. The chain of infection involves constantly searching the Internet for potentially insecure networking devices and then using default login credentials for hijacking attempts. In a slight difference, the attacker used some new username and password combinations during the scan.
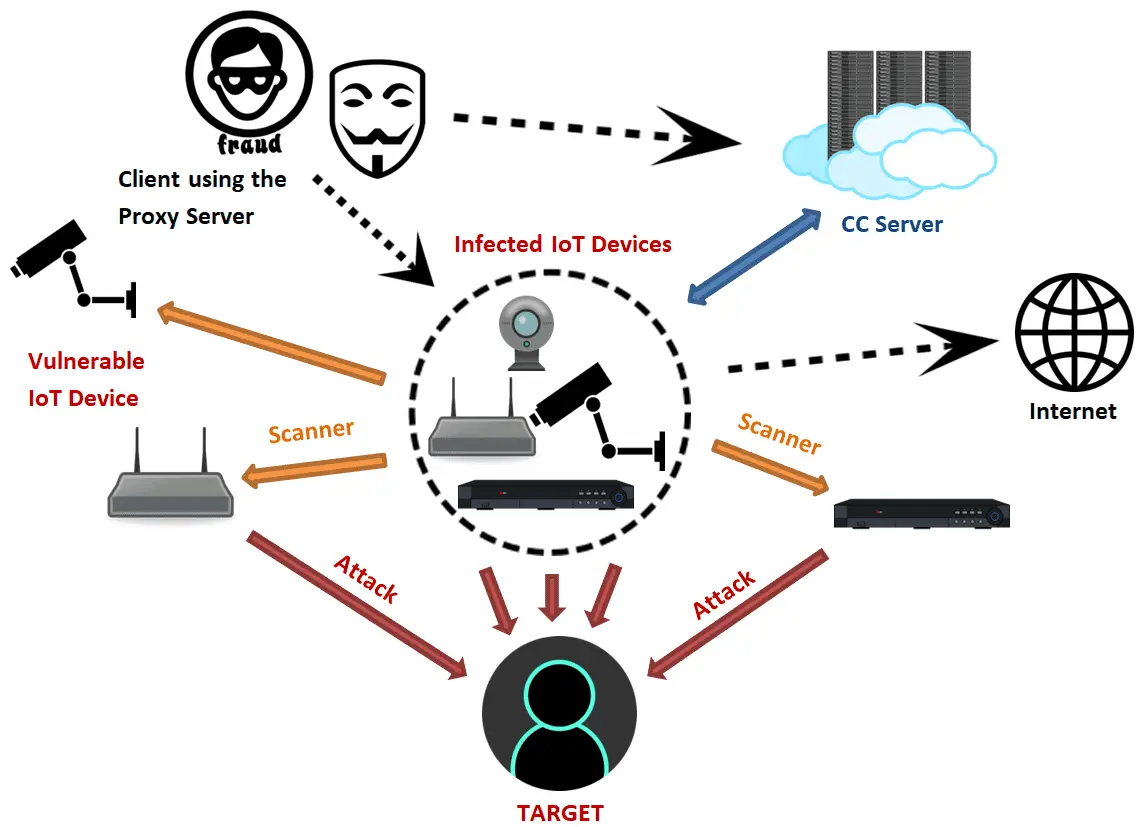
Generally speaking, once attackers start using new usernames and passwords, this means that they have already redirected their attacks to new devices. Trend Micro indicated that some of the username and password combinations they discovered came from the default settings used by China Telecom’s Optical Cat.
Some of the default usernames and password combinations include telnetadmin:telnetadmin used by E-140W-P, e8telnet:e8telnet used by HGU421v3, and e8ehome:e8ehome used by Huawei E8C. The purpose of the event seems to be to detect whether these devices are also being used in Brazil.
Trend Micro compared this participating IP address with the records in its historical database and found 167 routers, 16 webcams, and 4 digital video recorders (DVRs). This result proves more favorably that these devices are indeed part of the Mirai botnet, and that the owners of the botnet are using these devices to detect new targets.
In addition, Trend Micro also pointed out that most of the devices participating in this scanning activity are based on Broadcom chips and cats. From the IP address, they are mainly distributed in Fujian, Hunan, and Shandong.
The security risks associated with using default login credentials have been mentioned by many security experts and law enforcement agencies over the years, and there have been many reports of cyber attacks triggered by the use of default login credentials. However, it turns out that even this seems to have failed to get everyone’s attention.
Using a default login credential means that anyone who can discover your device can easily access it. For hackers, this will be a good breakthrough for launching cyber attacks, such as using it for building botnets. For this reason, whether it is for an individual or a business, changing the default username and password of a device before it is officially put into use is a necessary step to protect yourself from becoming a victim of cyber attacks.