TripleCross: Linux eBPF rootkit
TripleCross
TripleCross is a Linux eBPF rootkit that demonstrates the offensive capabilities of the eBPF technology.
TripleCross is inspired by previous implant designs in this area, notably the works of Jeff Dileo at DEFCON 271, Pat Hogan at DEFCON 292, Guillaume Fournier and Sylvain Afchain also at DEFCON 293, and Kris Nóva’s Boopkit4. We reuse and extend some of the techniques pioneered by these previous explorations of the offensive capabilities of eBPF technology.
This rootkit was created for my Bachelor’s Thesis at UC3M. More details about its design are provided in the thesis document.
Features
- A library injection module to execute malicious code by writing at a process’ virtual memory.
- An execution hijacking module that modifies data passed to the kernel to execute malicious programs.
- A local privilege escalation module that allows for running malicious programs with root privileges.
- A backdoor with C2 capabilities that can monitor the network and execute commands sent from a remote rootkit client. It incorporates multiple activation triggers so that these actions are transmitted stealthily.
- A rootkit client that allows an attacker to establish 3 different types of shell-like connections to send commands and actions that control the rootkit state remotely.
- A persistence module that ensures the rootkit remains installed maintaining full privileges even after a reboot event.
- A stealth module that hides rootkit-related files and directories from the user.
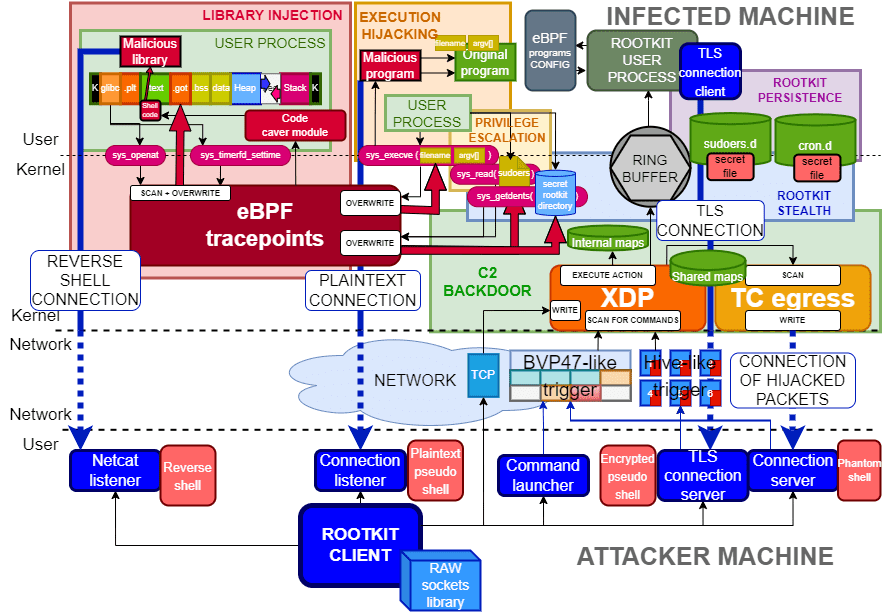
TripleCross overview
The following figure shows the architecture of TripleCross and its modules.

The raw sockets library RawTCP_Lib used for rootkit transmissions is of my authorship and has its own repository.
Install & Use
Copyright (C) 2022 h3xduck





