GENERAL INFECTION FLOW
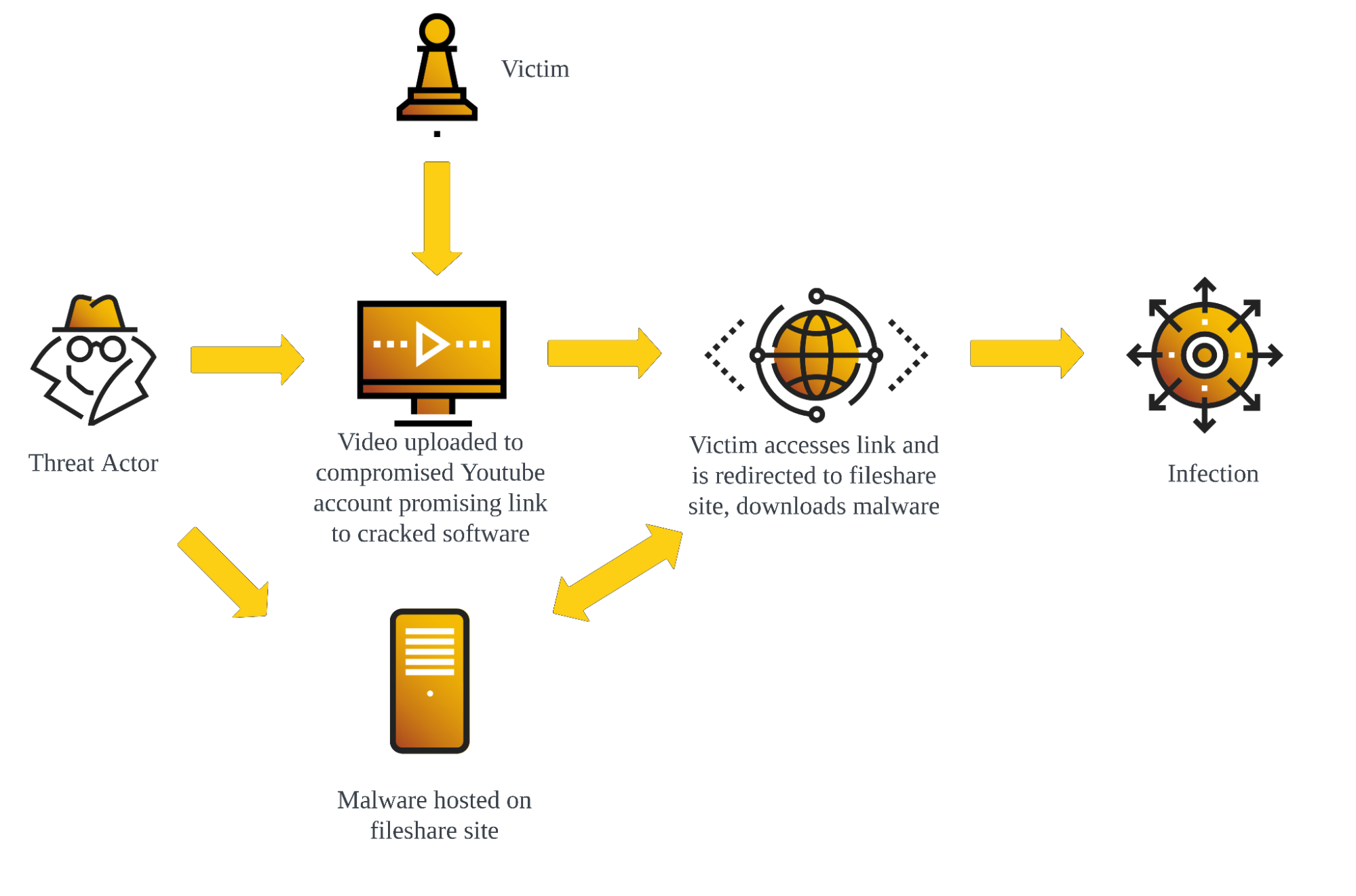
Recently, the Cybereason Security Services Team unveiled a startling report titled “From Cracked to Hacked: Malware Spread via YouTube Videos,” revealing a sophisticated cyber threat landscape. This investigation uncovers how threat actors ingeniously exploit YouTube’s vast audience by hijacking dormant accounts to distribute malware-laden videos. These videos, often promising cracked versions of popular software, are a digital Trojan horse, luring unsuspecting viewers with the allure of free access, only to compromise their systems.

The method is deceptively simple: attackers take control of YouTube channels, leveraging old credentials possibly leaked in data breaches, to upload content drastically different from the channel’s history. These uploads, uniform across compromised accounts, promise illicit access to coveted software but deliver nothing more than malware. The report highlights how these cybercriminals utilize AI-generated content and search engine optimization (SEO) poisoning to enhance their videos’ reach and credibility, casting a wide net over potential victims.
Among the arsenal of malware observed, infostealers reign supreme, with Redline and RaccoonStealer emerging as primary threats. These insidious programs not only pilfer sensitive data but also serve as backdoors for further infiltration, posing a grave risk to compromised systems.
The report delves into a specific threat actor, dubbed TropiCracked, whose nefarious exploits have targeted over 800 YouTube accounts in South America. Employing a sophisticated infrastructure, TropiCracked orchestrates a seamless blend of deception and obfuscation, consistently evading detection by swapping out payloads and exploiting loopholes in online platforms.
In light of these alarming revelations, proactive measures are imperative to combat cyber threats. Cybereason advocates for a multi-faceted approach, combining user education with robust detection mechanisms to fortify defenses against evolving threats.