The ESET security team found that a state-funded Russian cyber espionage organization, Turla has added a new “weapon” to its network of armaments aimed at targeting embassies and consulates in Eastern European countries. According to the researchers, Turla bundled its backdoor with a valid Flash Player installer in an attempt to trick the target user into installing malware in order to steal sensitive information.
Turla’s organization has long used social engineering to lure target audiences to download and install fake Adobe Flash Player. However, ESET recent research found that the organization is not limited to the past attack tools, but continue to develop new types of cyber attack weapons.
According to ESET, Turla now bundles its backdoors not just with the legitimate Flash Player installer, but with more workarounds to ensure that the URLs and IP addresses used correspond to Adobe’s legitimate infrastructure. In this way, attackers can basically use Adobe to convince users to download malware and to convince users that the software they download comes from Adobe’s official website (adobe.com).
There have been several Turla organization-related features in the attack on the new tool since July 2016, including Mosquito, a backdoor created by the organization, and the IP addresses previously associated with the organization. In addition to the relevant features described above, the new tools share similarities with other malware families spread by Turla.
Attack vector
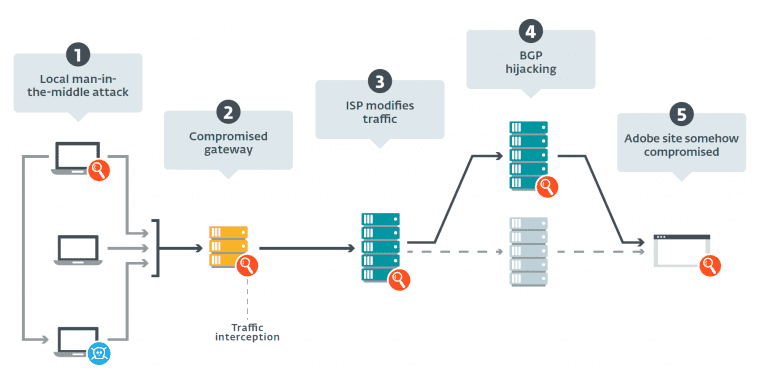
ESET researchers made several assumptions, as shown in the following figure, about how Turla’s malware can be applied to users’ computers. The following figure in accordance with the icon followed by the ① local man-in-the-middle attack, ② compromised the gateway, ③ ISP modifies, ④ BGP hijacking, ⑤ Adobe site somehow compromised
After hypotheses and validations, the probable attack vectors ESET researchers consider are:
– A machine within the victim’s organization’s network may be hijacked so that it acts as a springboard for MitM attacks, which will effectively redirect traffic from the target machine to the infected machine on the local network.
– Attackers may also compromise the organization’s gateways, enabling it to intercept all incoming and outgoing traffic between the organization’s intranet and the Internet.
Traffic blocking may also occur at the Internet service provider (ISP) level.
– Attackers may use Border Gateway Protocol (BGP) hijacking to reroute traffic to Turla-controlled servers, although such a policy may start alerts for Adobe or BGP monitoring services fairly quickly.
Once the fake Flash program has been successfully installed and started, several of the previous backdoors used may be dropped, such as the backdoor Mosquito, which is a Win32 malware that communicates with web applications hosted on Google Apps scripts through malicious JavaScript files, or Unknown files downloaded from fake and non-existent Adobe URLs.
This phase will then be set as the primary goal of the task – filtering of sensitive data, including the unique ID of the compromised computer, the username, and a list of security products installed on the device. The username and device name are filtered from MacOS by the back door Turla uses.
In the final part of this process, the forged installer discards subsequent attempts to run a valid Flash Player application to confuse the user. The latter installer is either embedded in its fake object or downloaded from the Google Drive website. In order to establish persistence on the system, malicious installers also tamper with the operating system’s registry and create an administrative account that allows remote access.
Currently, ESET researchers say it has discovered a new sample of the Turla back door Mosquito, although its code analysis is more difficult.
Read ESET’s latest findings about Turla here in: Diplomats in Eastern Europe bitten by a Turla mosquito
Source: welivesecurity