Image: Perception Point X-Ray
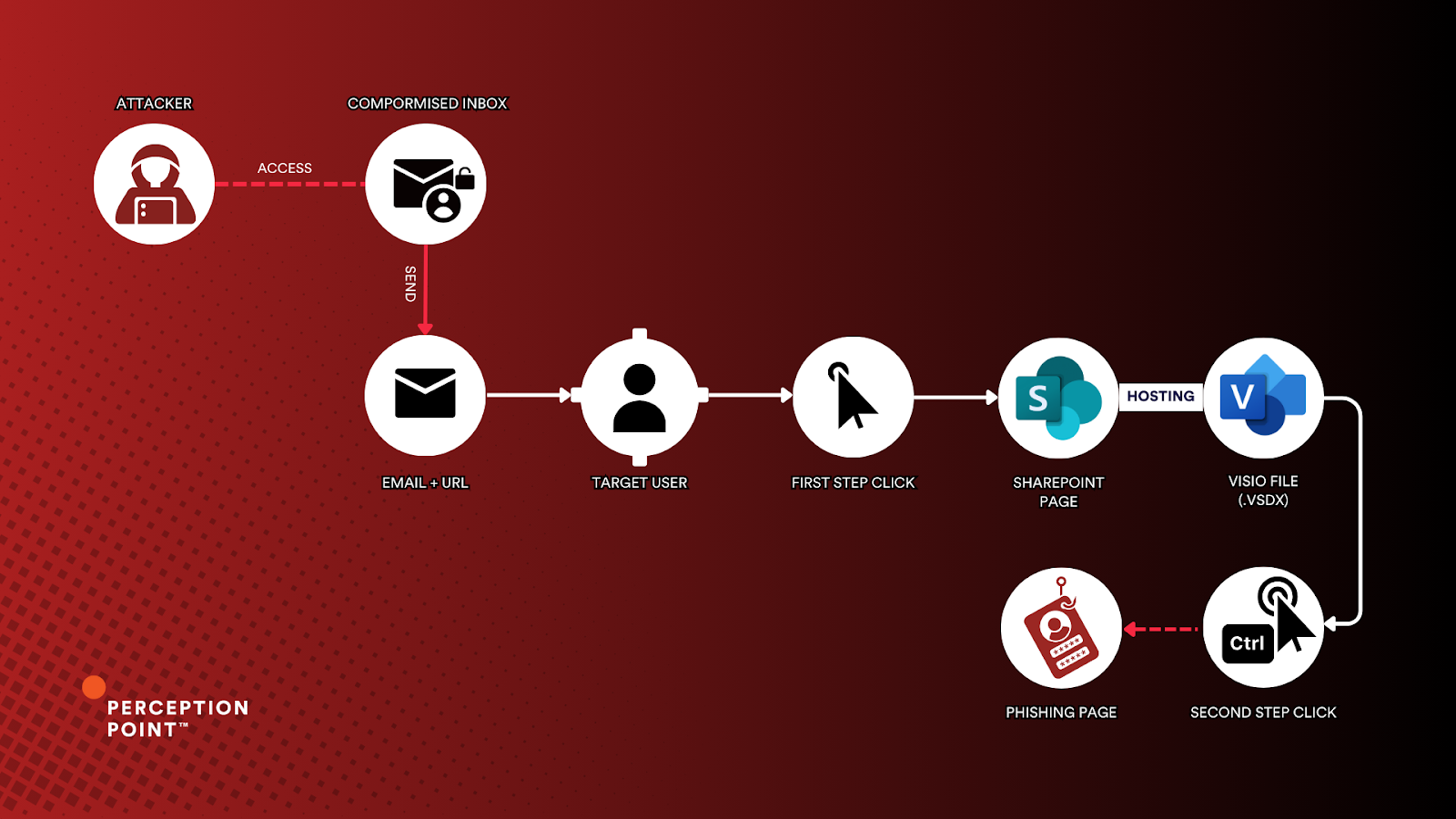
Perception Point’s latest findings have uncovered an advanced two-step phishing technique exploiting Microsoft Visio files (.vsdx) and SharePoint to launch highly deceptive credential theft campaigns.
Traditionally used for professional diagrams such as flowcharts and network maps, Microsoft Visio files are now being weaponized. “In recent phishing campaigns, Visio files are being weaponized to deliver malicious URLs, creating a deceptive delivery point in a two-step attack path,” Perception Point’s report reveals.
This method capitalizes on the trust users place in familiar platforms like SharePoint and Microsoft Visio. By embedding malicious URLs within .vsdx files hosted on compromised SharePoint accounts, attackers bypass many standard security measures.
The attack unfolds in a two-step process designed to evade detection and exploit user behavior:
- Step One: The Lure
Attackers begin by using breached email accounts to send phishing emails to targets. These emails, appearing legitimate due to their origin, often include a convincing narrative such as an urgent business proposal or purchase order. “Because the messages are sent from real accounts, they pass standard authentication checks like SPF,” Perception Point notes.These emails may include a link or an .eml file attachment containing a URL leading to a SharePoint-hosted Visio file. - Step Two: The Trap
Clicking the link redirects victims to a compromised SharePoint page hosting a Visio file. The file contains an embedded Call-to-Action button, often labeled “View Document.” Victims are instructed to hold down the Ctrl key and click, a simple action that bypasses automated security systems.Once clicked, the embedded URL directs users to a fake Microsoft 365 login page designed to harvest credentials. “Interacting with the link redirects the victim to a phishing page impersonating Microsoft 365,” the report explains.
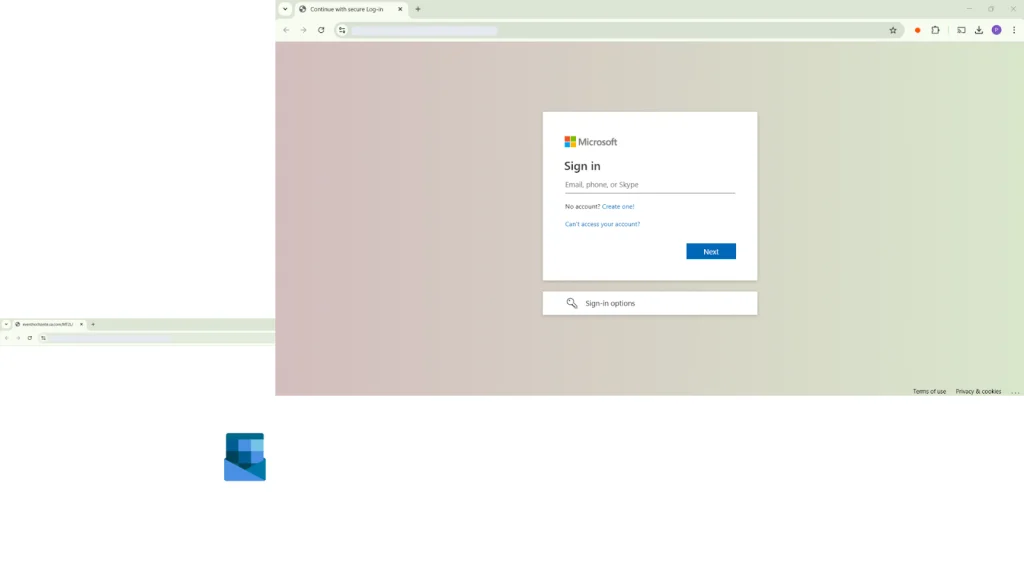
This phishing technique combines technical sophistication with psychological manipulation. By requiring users to perform manual actions, such as holding the Ctrl key, attackers evade automated email security scanners and detection tools. Additionally, the use of legitimate branding, including organizational logos, adds credibility to the malicious Visio files.
Perception Point’s researchers have observed a marked increase in attacks using this method, targeting hundreds of organizations globally. The report warns that these campaigns are “designed to evade detection and exploit user trust,” highlighting the importance of vigilance in corporate environments.
Related Posts:
- Exploitation of URL Rewriting: A New Phishing Paradigm Threatens Cybersecurity
- Microsoft’s September Patch Tuesday: A Patchwork of Urgency with 4 Zero-Days Under Attack
- Mozilla adds “two-step authentication” support for Firefox accounts