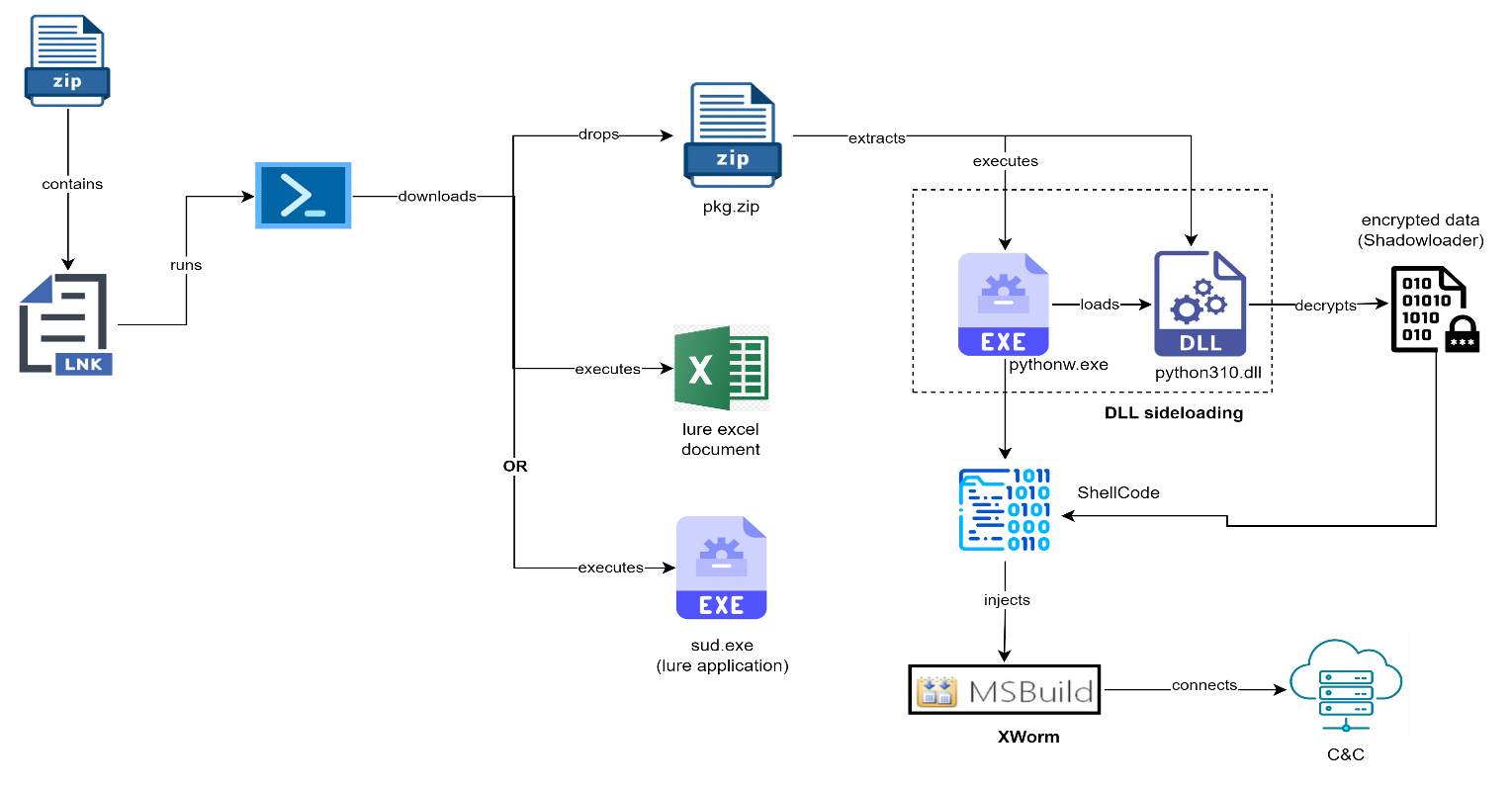
Infection chain
The Cyble Research and Intelligence Labs (CRIL) has uncovered a persistent malware campaign specifically targeting Ukrainian individuals and organizations. This campaign, attributed to the threat actor group UAC-0184, leverages sophisticated techniques like DLL sideloading and the use of Python-related files to deliver the notorious XWorm Remote Access Trojan (RAT).
The exact initial attack method remains unclear, though it likely involves phishing or spam emails with ZIP attachments. CRIL’s analysis began with an LNK file within the ZIP archive, which, upon execution, triggers a PowerShell script. This script downloads an additional ZIP file and a lure document, setting the stage for the malware payload.
Upon extracting the ZIP file contents, users encounter an LNK shortcut named “NewCopy.xlsx.lnk.” Misleadingly designed to appear as an Excel worksheet, this file, when executed, launches a PowerShell command from %appdata%, which downloads two files: “pkg.zip” and “NewCopy.xlsx” from a malicious URL.
The PowerShell script extracts “pkg.zip” into a folder named “SecurityCheck” in %appdata%, executing “pythonw.exe” from this directory. It then downloads and opens the “NewCopy.xlsx” lure document, maintaining the illusion of legitimacy. This technique effectively masks the malicious activities occurring in the background.
Central to this campaign is the DLL sideloading method. The genuine “pythonw.exe” executable is used to load a malicious DLL, “python310.dll.” This DLL creates a cmd.exe process that initiates a suspended MSBuild process. The loader then decrypts a file named “daikon.tif” (Shadowladder) and injects shellcode into the MSBuild process using Process Hollowing. This chain of actions results in the deployment of the XWorm RAT.
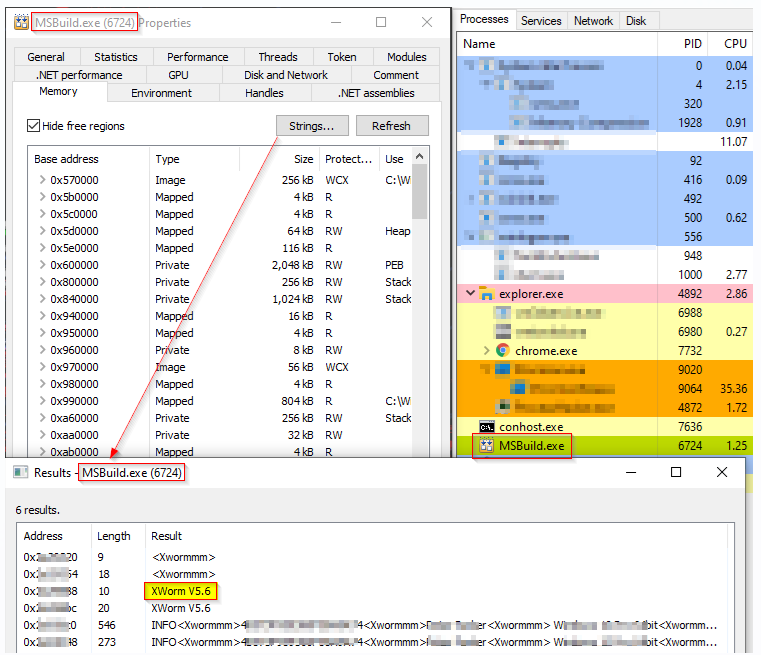
XWorm RAT is commodity malware, easily accessible to cybercriminals. It offers a wide range of capabilities, including data theft, DDoS attacks, cryptocurrency address manipulation, ransomware deployment, and downloading additional malware. After its execution, XWorm drops a VB Script file into the %temp% folder, which connects to a Command-and-Control (C&C) server, enabling the threat actors to maintain control over the infected systems.
In mid-June, CRIL identified additional files linked to the same threat actor, indicating a persistent focus on Ukrainian targets. A notable variation in this phase of the campaign involved an LNK file disguised as a document viewer application with the name “Відомості про кредитора.dvs.” Executing this file displays a deceptive GUI mimicking the State Executive Service’s document management system.
In this iteration, the TA used IObit Driver Booster files instead of Python-related files. The process involved RttHlp.exe (IObit Driver Booster executable) loading a malicious DLL named vcl120.bpl via DLL sideloading, spawning a cmd.exe process, and subsequently initiating a suspended MSBuild process. The loader then decrypted “bacteriostat.flac” and injected shellcode into the running MSBuild process using Process Hollowing.
UAC-0184 continues to refine its malware campaigns against Ukraine, employing increasingly sophisticated evasion techniques. This recent campaign’s use of Python-related files for DLL sideloading underscores their commitment to circumventing detection measures. The deployment of XWorm RAT demonstrates the group’s primary objective of establishing remote access to compromised systems, reflecting a sustained effort to infiltrate Ukrainian targets for strategic purposes.