At least three routers made by Australian telecommunications equipment company NetComm Wireless are affected by two serious vulnerabilities that can be exploited remotely to take control of affected devices. The Netcomm NF20Mesh router is currently recommended by Aussie Broadband when signing up for a new service with the number of other Australian service providers and vendors starting to offer Netcomm routers.
Researcher Bscarvell, who has been found for finding the vulnerabilities, told that combine of the security holes allows an unauthenticated attacker to gain remote code execution in some NetComm routers.
According to an advisory published today by the researcher @bscarvell, NF20MESH routers running firmware versions prior to version R6B021 are impacted by two vulnerabilities. The list includes an authentication bypass and a stack-based buffer overflow vulnerability.
The authentication bypass issue is due to the improper implementation of the strstr() function and enables an adversary to bypass authentication controls and log in to the device.
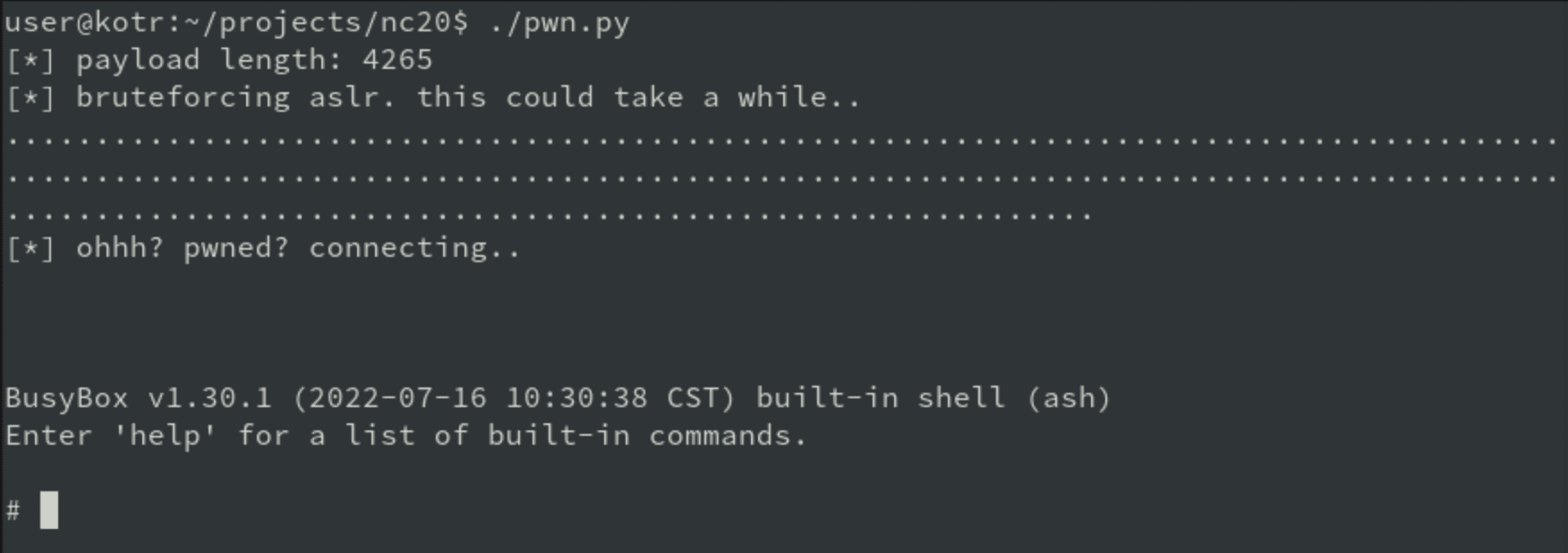
A buffer overflow flaw was found on the strcpy function. The researcher explained: “Given the number of strcpy references in the application, I wrote a small python script to starting fuzzing parameters to see if we could trigger any bugs while I performed a deeper analysis of the binary itself. After running the fuzzer, I quickly saw the following crash on my UART console:
“

NF20, NF20MESH, and NL1902 routers have been confirmed by Netcomm to be vulnerable to the remote code execution vulnerability. It’s possible that other devices may also be affected.
Due to the proof-of-concept exploit code being released, users are recommended to update to firmware version R6B021 to address the flaw.