unc0ver
An HTTP Recon tool

unc0ver is a lightweight tool for performing HTTP reconnaissance. It is designed with the Unix principle of doing one thing and does it well. It is constantly being updated so check back often for new features and bug fixes. Although I have included a wordlist, I highly recommend using unc0ver in combination with something like Daniel Miessler’s excellent SecLists project in order to get the full benefit.
Download
git clone https://github.com/Surfrdan/unc0ver.git
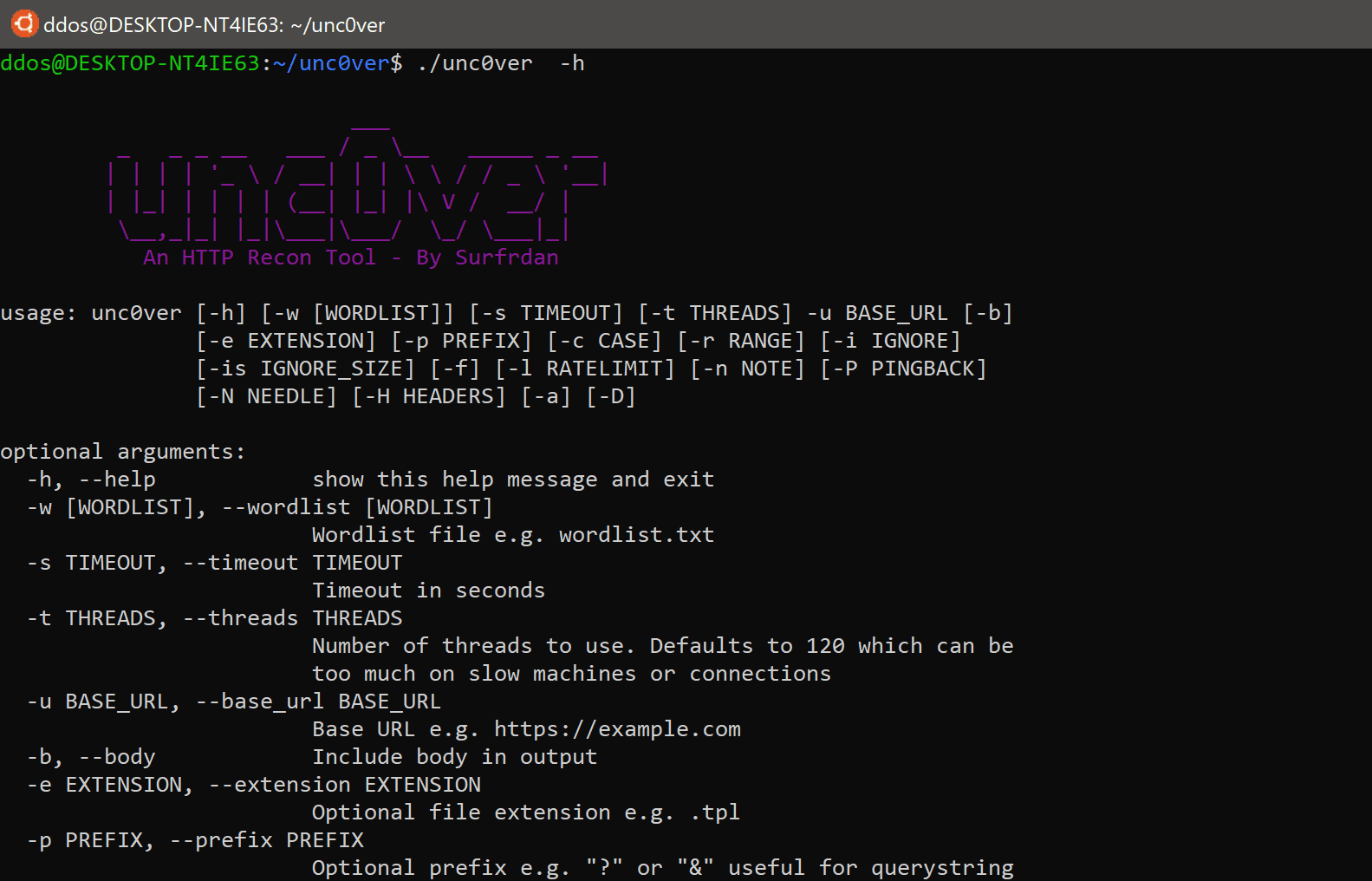
Usage
| Arg | Description |
|---|---|
| -u | Base URL for requests to be made to |
| -a | Randomise User-Agent header from some common browser IDs |
| -w | Wordlist file e.g. wordlist.txt |
| -b | Include Body in output |
| -e | File Extension or other string to appear in URL after the dynamic string e.g. ‘.php’ or ‘=9999’ or ‘/further/directories’ |
| -p | Prefix to dynamic string e.g. ‘?’ or ‘&’ Useful for querystrings |
| -c | Case to convert a dynamic string to. Supports ‘upper’, ‘lower’ and ‘first’ |
| -r | range of integers for fuzzing numeric files or IDs e.g. 1:300 will create numbers from 1 to 300 in place of the dynamic string |
| -i | list of HTTP error codes to ignore. By default this is set to “404,502,503,504” |
| -is | list of returned body sizes in bytes to ignore. e.g. “0,2,2067”, also supports range syntax e.g. 100:130 to ignore anything between 100 and 130 bytes |
| -f | Follow re-directs, off by default |
| -l | Simple rate limiting. Value is the number of milliseconds between requests |
| -n | Note field in results. Defaults to Server header but can be overridden with title or h1 to display the pages <title> or <h1> content |
| -H | Specify comma-separated header values e.g. “Host: example.com, Content-type: application/json” |
| -D | Debug mode |
Examples
Here we use the supplied wordlist and convert all strings to lower case and add a .php file extension. We’re also asking for the page title instead of the Server header to be printed in the results
Here we utilise ignore arguments with 2 supplied HTTP error codes and also asking to ignore all zero byte responses
Source: https://github.com/Surfrdan/