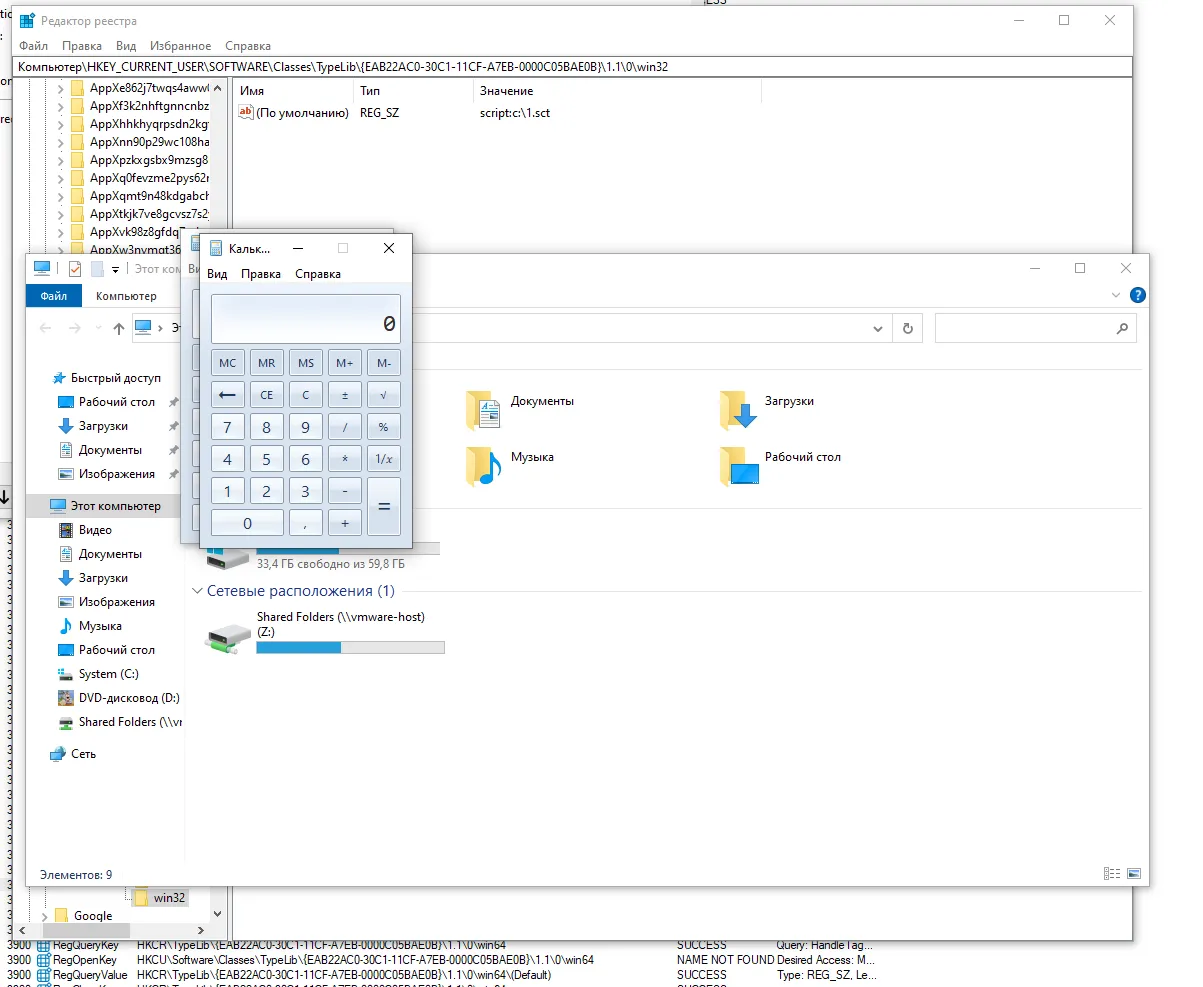
Persistence works | Image: Michael Zhmailo
A new persistence method has been found by Michael Zhmailo from MTS Innovation Center’s CICADA8 team. This method involves hijacking TypeLib libraries within the Windows Component Object Model (COM) system, specifically targeting processes like explorer.exe to achieve stealthy, persistent code execution.
Traditional persistence techniques like registry keys, scheduled tasks, and AutoRun folders are well-known and closely monitored. However, as Zhmailo explains, “these methods are well known to defenders, which makes them easy to detect”. Motivated by the need for a more elusive approach, he turned his attention to the COM system—a longstanding and often misunderstood component of Windows.
The crux of this technique lies in the use of TypeLibs, which contain essential information about COM classes and interfaces. The magic happens with the LoadTypeLib() function, which typically loads TypeLib libraries from a specified path in the registry. However, as Zhmailo discovered, “if explorer.exe calls the LoadTypeLib() function and we hijacked the necessary registry keys for the moniker, the moniker will be instantiated inside explorer.exe and its code will be executed”. This discovery enables code execution within explorer.exe, a process that automatically starts with the operating system, providing an unbroken line of persistence.
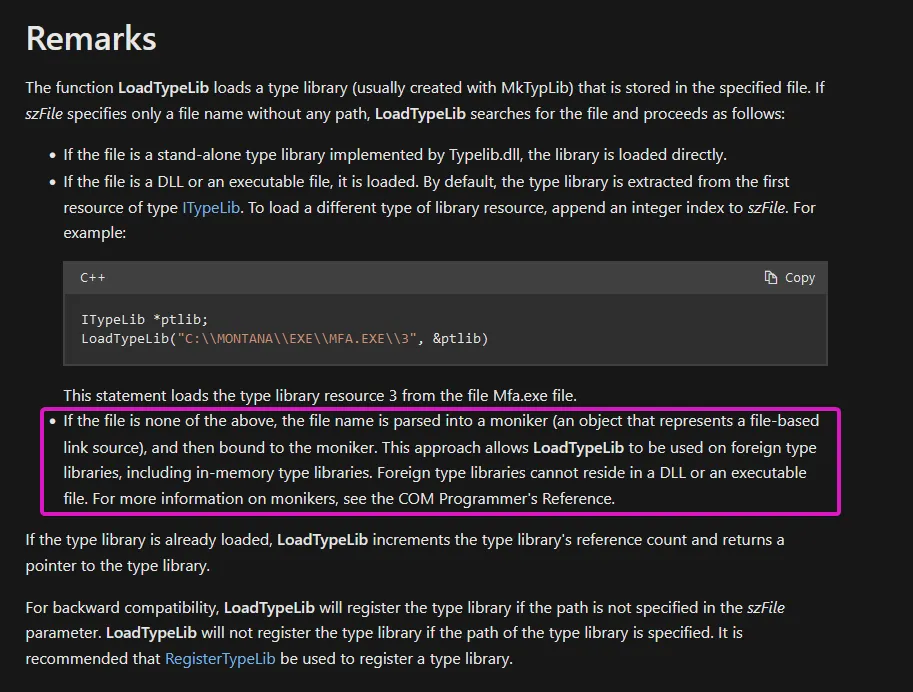
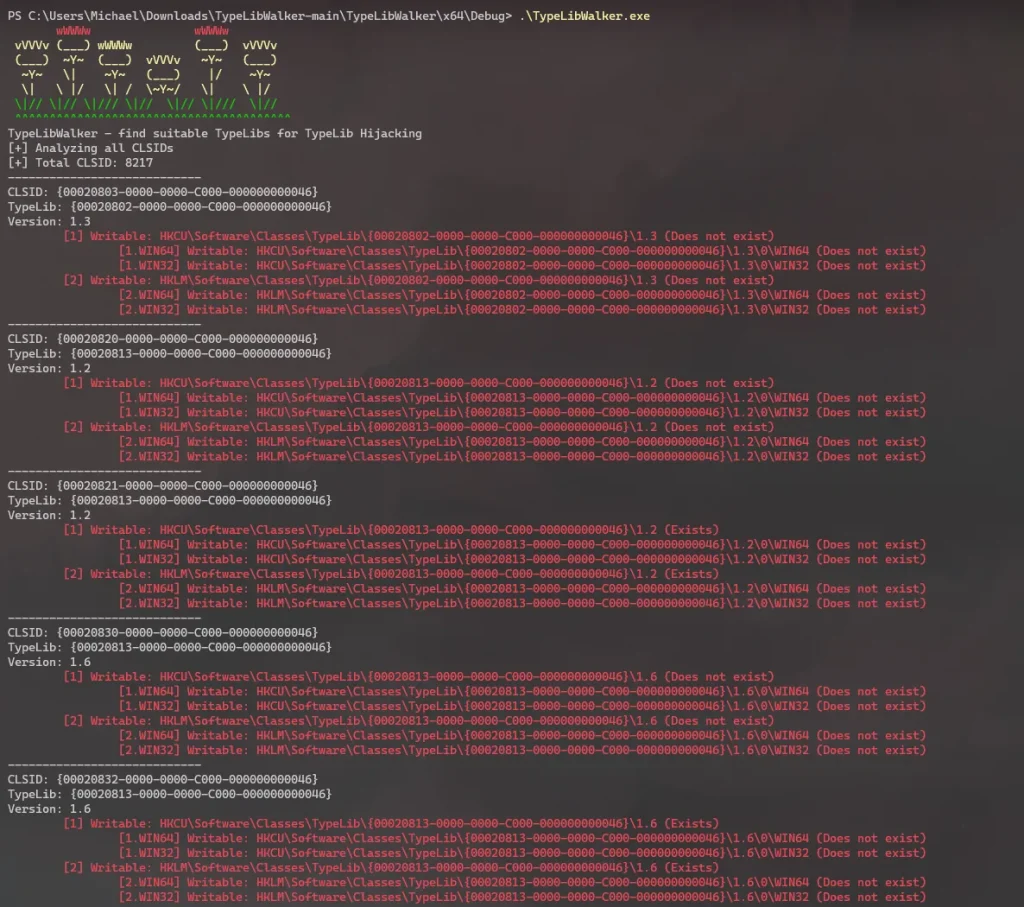
To aid in finding exploitable TypeLibs, Zhmailo’s team created a tool called TypeLibWalker, which automates the detection of vulnerable registry entries. This tool, as noted in the report, “allows you to automate the process of detecting potentially vulnerable registry entries that can be hijacked”. With it, attackers can identify TypeLib paths that can be overwritten, enabling stealthy persistence without needing to monitor registry changes manually.
Related Posts:
- Google Project Zero team found a Windows zero-day vulnerability
- “The Com” Phishing Attacks Escalate, Targeting Businesses with Fake Login Pages