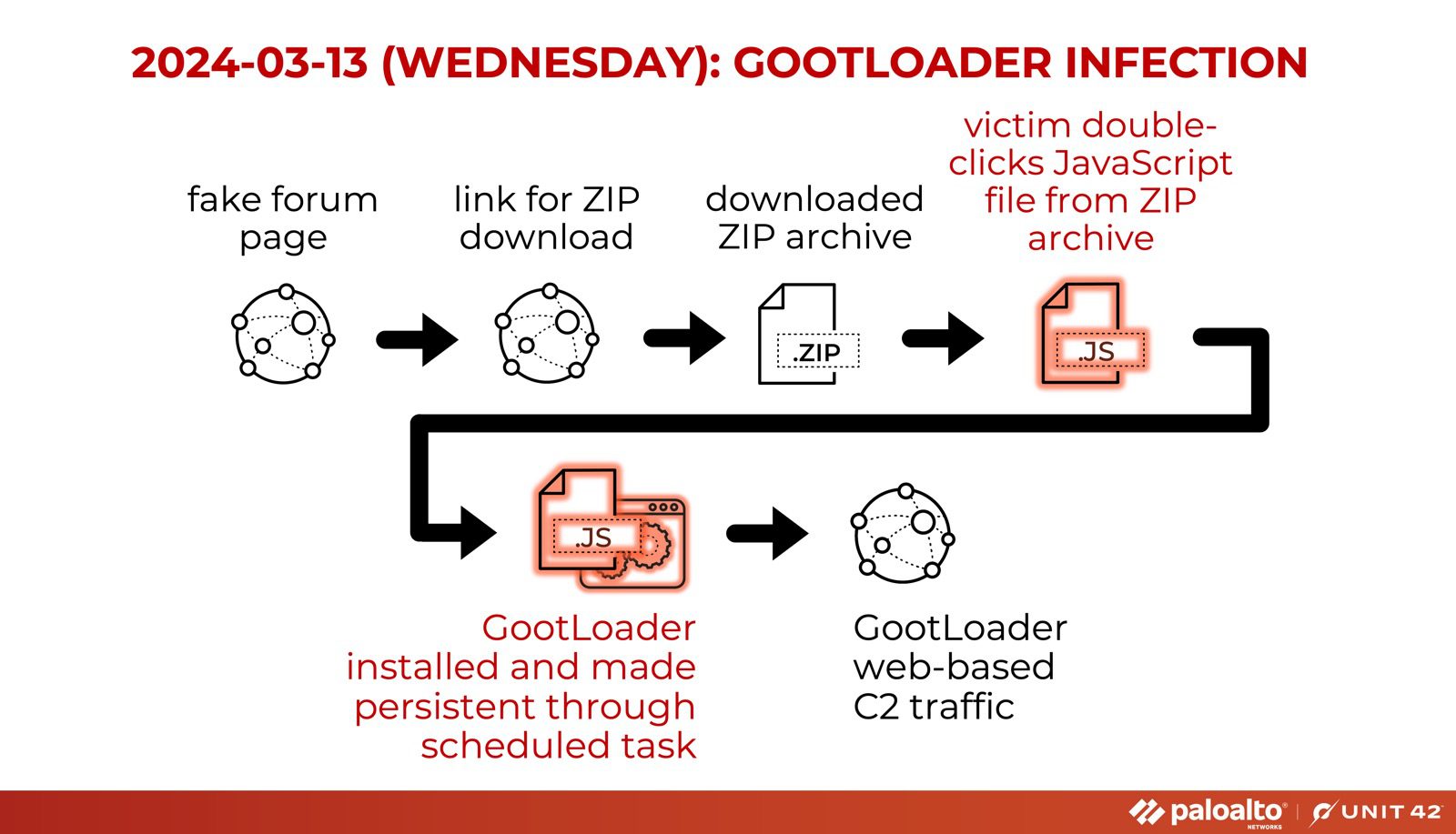
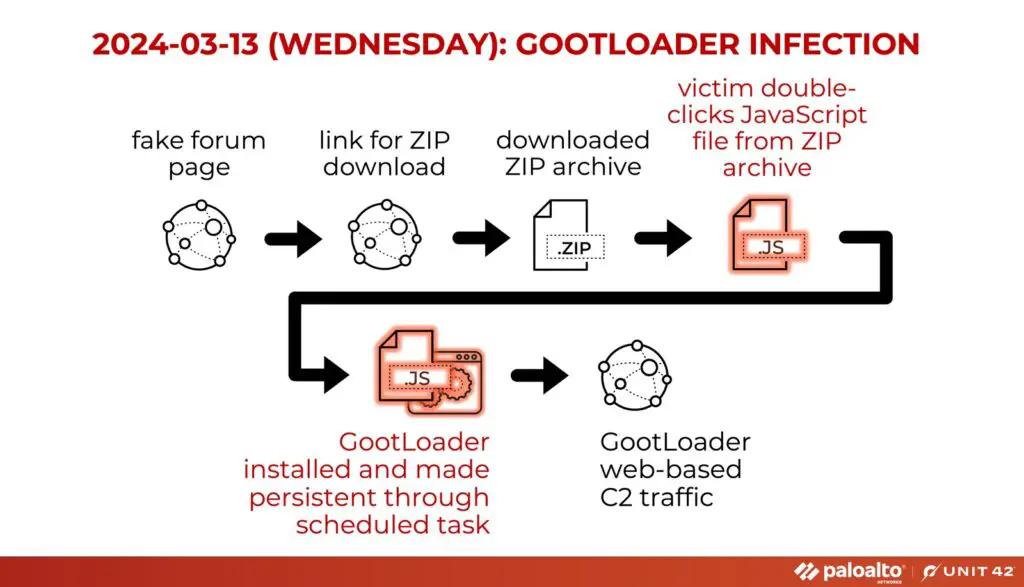
Flowchart for a GootLoader infection
Palo Alto Networks’ Unit 42 threat intelligence team has published a comprehensive analysis detailing the advanced evasion techniques employed by GootLoader, a pervasive malware known for its role in delivering ransomware and other malicious payloads.
The GootLoader malware, a JavaScript-based loader and backdoor, has been actively distributed through deceptive forum posts by its operators. This analysis reveals how GootLoader evades detection by sandboxes, which often struggle to analyze a high volume of binaries due to limited computing resources. By delaying its malicious actions, commonly referred to as “sleeping,” GootLoader manages to obscure its true intent.
To overcome the challenges posed by GootLoader’s obfuscation techniques, Unit 42 researchers employed Node.js debugging within Visual Studio Code. This approach enabled them to meticulously analyze the malware’s JavaScript code, setting breakpoints and tracing the execution flow to uncover the underlying evasion mechanisms.
The research identified GootLoader’s use of nested loops and function arrays as a key component of its evasion strategy. By introducing significant delays in code execution, these constructs effectively prevent the malware from revealing its malicious behavior within the limited time frame of a typical sandbox analysis.
Through meticulous analysis, the Unit 42 team traced the execution path to the “course83” function, which serves as the trigger for GootLoader’s malicious activities. This function initiates the download and execution of additional payloads, effectively weaponizing the compromised system.
The findings underscore the importance of advanced debugging tools and techniques in combating sophisticated malware. By understanding and countering these evasion tactics, cybersecurity professionals can enhance their detection and response strategies, safeguarding digital systems and networks.
For more detailed information and technical documentation, visit the Unit 42 website.