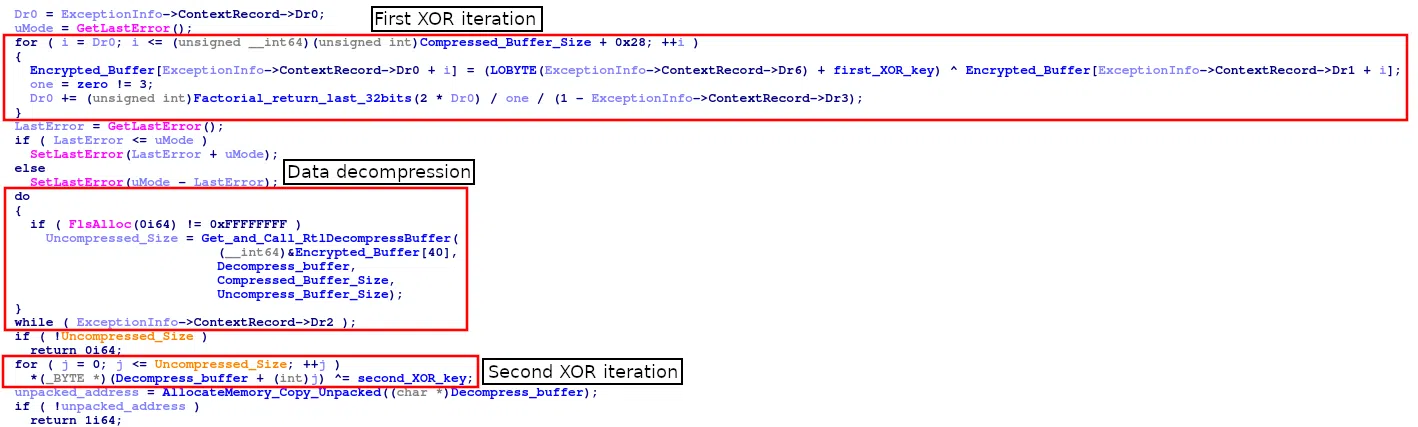
Unpacking code
HarfangLab published an in-depth analysis of a newly identified private packer dubbed “PackXOR,” a tool used by threat actors, including the notorious FIN7 group. Initially observed as part of the AvNeutralizer (also known as AuKill) payload, this packer has drawn attention for its ability to evade detection and obscure a variety of malicious activities.
FIN7, a well-known cybercrime syndicate, is historically linked to high-profile attacks targeting financial institutions. Their latest tool, AvNeutralizer, is used to disable endpoint detection and response (EDR) systems by exploiting vulnerable drivers to kill security processes. FIN7 has been distributing AvNeutralizer since 2022, primarily through underground forums such as xss[.]is, exploit[.]in, and RAMP.
However, HarfangLab’s investigation of PackXOR shows that this packer isn’t exclusively tied to FIN7. Other threat actors have been found using PackXOR to deploy different payloads, such as the XMRig cryptominer and the R77 rootkit, often in combination with the open-source SilentCryptoMiner obfuscator. This expanded usage hints that PackXOR has become a valuable commodity in the cybercrime market.
PackXOR is designed to compress, encrypt, and obfuscate malicious code, complicating the efforts of malware analysts and security tools. It employs a two-phase XOR encryption process alongside LZNT1 compression, effectively concealing payloads. Here’s how it works:
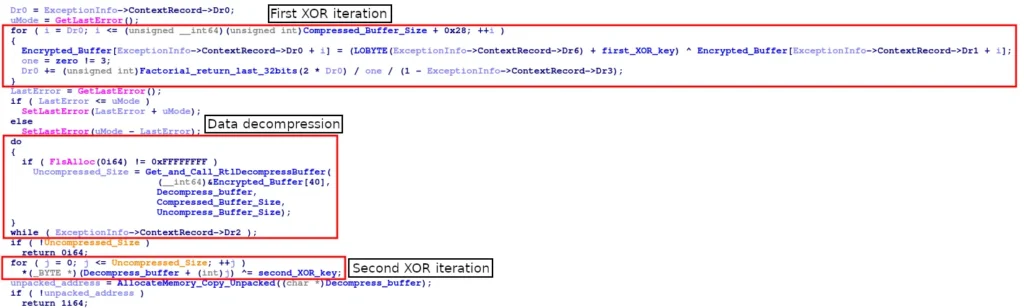
- First XOR iteration: XOR key 1 is applied to the compressed payload.
- LZNT1 Decompression: The compressed data is decompressed into its original form.
- Second XOR iteration: XOR key 2 is used to further encrypt the decompressed data.
By hiding malicious code behind multiple layers of encryption and compression, PackXOR increases the difficulty for security professionals to detect and analyze the payloads on time.
While PackXOR was initially tied to FIN7’s AvNeutralizer, HarfangLab’s analysis has identified its use in a wide range of other malicious activities, extending beyond FIN7’s known tactics. Specifically:
- XMRig Cryptominer: Used to mine cryptocurrency by hijacking victims’ processing power.
- R77 Rootkit: A stealthy malware tool used to maintain long-term access to compromised systems.
- SilentCryptoMiner: An additional obfuscator used to further conceal the malicious payloads.
The variety of payloads found packed with PackXOR demonstrates that this tool is not confined to a single threat actor. Rather, it’s being used across different cybercrime campaigns, with obfuscation layers applied to ensure these operations remain undetected.
One of the standout features of PackXOR is its ability to hide strings within the binary, making it harder for security tools to flag suspicious activity. By employing XOR encryption and subtraction operations, PackXOR dynamically decrypts essential strings, such as API calls and DLL names, only when needed. This approach significantly reduces the chances of static detection by security software.
In some cases, PackXOR was found to wrap its payloads with additional layers of obfuscation, creating a multilayered defense against analysis. HarfangLab discovered payloads packed not only with PackXOR but also with other commercial tools like Hidden Malware Builder and SilentCryptoMiner. This combination of packers makes reverse-engineering efforts considerably more challenging, giving threat actors more time to operate undetected.
In response to the growing threat posed by PackXOR, HarfangLab has released an unpacker tool, empowering security researchers and analysts to dissect and analyze packed malware samples. This tool, available on HarfangLab’s Github repository, provides a crucial weapon in the fight against FIN7 and other cybercriminal groups leveraging PackXOR.
Related Posts:
- Cybersecurity Alert: FIN7 Expands Arsenal with New AvNeutralizer Variant
- FIN7 Hackers Using Signed Malware and Fake Google Ads to Evade Defenses
- Inside DiceLoader: How FIN7’s Malware Masters Evasion
- Malware Masquerade: HubSpot, Veeam, Xero – Carbanak Lures Victims with Trust