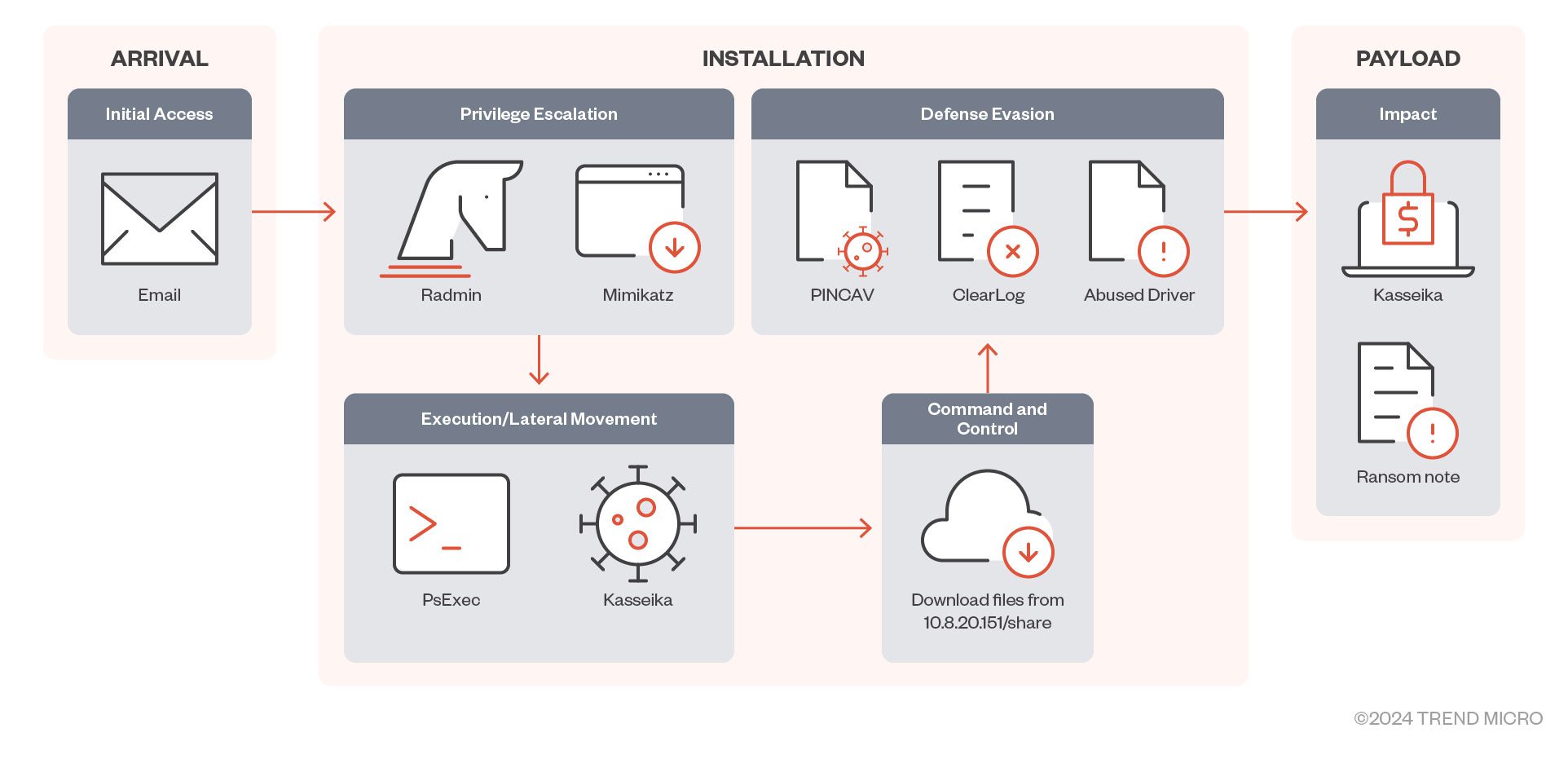
The Kasseika ransomware infection chain
As the digital landscape evolves, so too does the sophistication of threats that lurk within it. The Kasseika ransomware, identified amidst a surge in bring-your-own-vulnerable-driver (BYOVD) attacks in 2023, emerges as a formidable adversary. This malware, leveraging the Martini driver’s vulnerabilities, marks a concerning trend alongside other malicious entities like Akira, BlackByte, and AvosLocker.
Trend Micro’s meticulous analysis unveils Kasseika’s modus operandi, where it employs the Martini driver to neutralize antivirus defenses. This strategy isn’t just about infiltration; it’s about ensuring uninterrupted dominion over the compromised system. The ransomware then unfolds its malicious intent by deploying a concoction of pseudo-ransom extensions and the ominous .README.txt, signaling the commencement of a digital hostage situation.
Kasseika isn’t a lone wolf but rather a continuation of a malignant legacy. With substantial portions of its source code mirroring that of BlackMatter, Kasseika’s operations hint at a lineage of cyber malfeasance that can be traced back to DarkSide and even further to ALPHV, also known as BlackCat. This shared source code suggests not just a maturity among threat actors but a selective fraternity with access to highly guarded malicious arsenals.
The initial breach, as investigated by Trend Micro, follows a classic yet effective ploy: targeted phishing. The ransomware meticulously crafts its entry point, ensnaring credentials through seemingly benign emails, only to unleash a cascade of remote administration tools (RATs) and lateral movements within the target network. Kasseika’s utilization of PsExec, a legitimate Windows tool, for the execution of its malevolent scripts underlines the insidious nature of this campaign.

Kasseika’s attack doesn’t halt at deployment. By leveraging the Martini.sys driver, originally a component of the VirIT Agent System by TG Soft, the ransomware adeptly bypasses security measures. This evasion tactic, termed KILLAV, showcases Kasseika’s ability to disguise its presence, ensuring its malicious operations proceed undetected, all while preparing for its ultimate objective: data encryption and ransom demand.
Once the stage is set, Kasseika embarks on its final act—the encryption of the target system. Utilizing a Themida-packed 32-bit Windows PE file, the ransomware employs formidable code obfuscation and anti-debugging techniques, rendering reverse engineering a Herculean task. Following a thorough termination of processes accessing Windows Restart Manager, Kasseika deploys its encryption routine, renaming files with a cryptic extension that doubles as the ransom note’s identifier, completing its cycle of intrusion and extortion.
Researchers list measures that organizations can employ as best practices to minimize the chances of falling victim to ransomware attacks such as those launched by the Kasseika ransomware:
- Only grant employees administrative rights and access when necessary.
- Ensure that security products are updated regularly and perform period scans.
- Secure regular backups of critical data in case of any loss.
- Exercise good email and website safety practices — download attachments, select URLs, and execute programs only from trusted sources.
- Encourage users to alert the security team of potentially suspicious emails and files and use tools to block malicious emails.
- Conduct regular user education around the dangers and signals of social engineering.