Unpatched Kubernetes Flaw Leaves Clusters Open to Exploitation: Researcher Unveils Command Injection Vulnerability

Akamai researcher Tomer Peled has uncovered a concerning design flaw within Kubernetes’ git-sync project. This flaw could potentially enable attackers to execute commands or exfiltrate sensitive data, including service account tokens, within a Kubernetes pod. This vulnerability, which was presented at DEF CON 2024, has sparked concern within the security community, as it affects default Kubernetes installations across major cloud platforms, including Amazon EKS, Azure AKS, Google GKE, and Linode.
The git-sync project is designed to automate the synchronization of a pod with a remote Git repository, streamlining the process of updating content within a Kubernetes environment. However, Peled’s research revealed that the flexibility of git-sync’s configuration parameters, particularly GITSYNC_GIT and GITSYNC_PASSWORD_FILE, opens the door to potentially severe security risks.
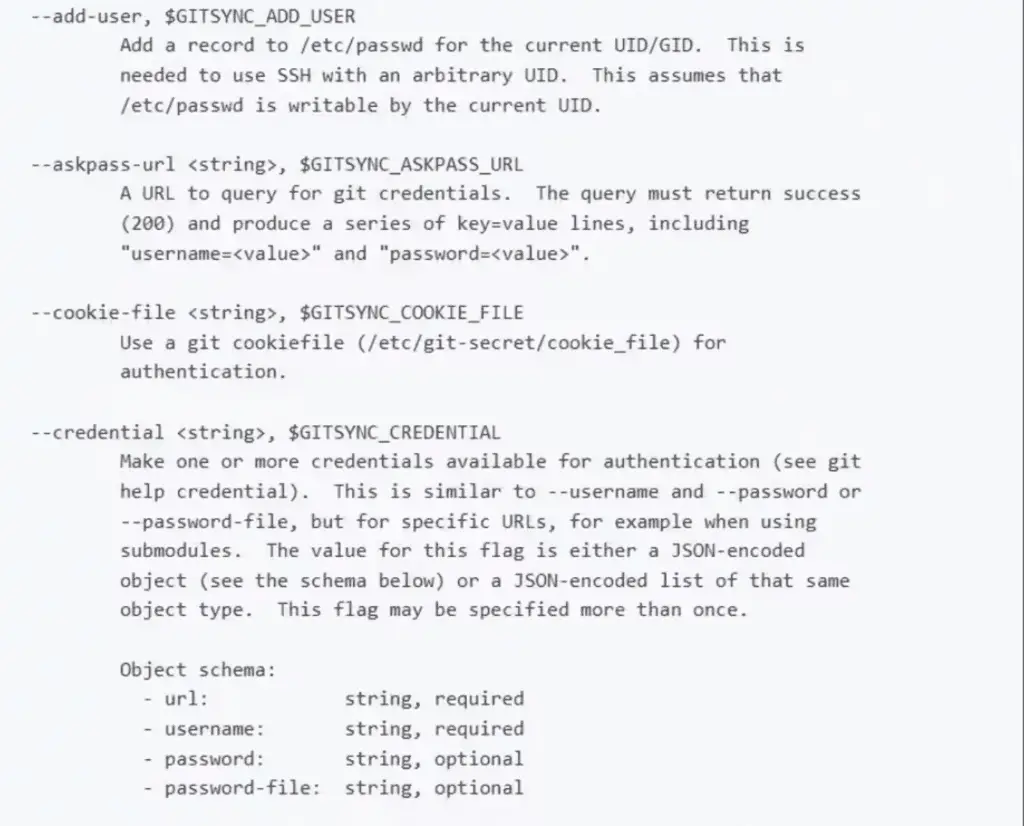
Some of git-sync’s parameters | Image: Akamai
At the heart of this vulnerability lies the GITSYNC_GIT parameter, which determines the Git command to be executed by the git-sync sidecar. In its default state, this parameter simply calls the Git binary. However, Peled’s findings show that by modifying this parameter, an attacker can replace the Git command with a malicious binary. This binary, once deployed within a pod, can be executed under the guise of git-sync, allowing the attacker to carry out command injection attacks with minimal privileges. This level of subversion is particularly dangerous in environments where git-sync communication is pre-authorized, as it can easily evade detection by security teams.

PoC of potential XMRig cryptominer | Image: Akamai
The second critical aspect of the vulnerability involves the GITSYNC_PASSWORD_FILE parameter. This parameter is intended to store the path to a file containing the Git authentication credentials. However, Peled demonstrated that an attacker with Edit privileges could manipulate this parameter to point to any file within the pod. By redirecting the git-sync process to a pseudo Git repository controlled by the attacker, sensitive files, including service account tokens, can be exfiltrated during the authentication process.

PoC of potential GITSYNC_PASSWORD_FILE attack | Image: Akamai
The potential impact of this design flaw is significant, as it can be exploited in default Kubernetes installations across a wide range of platforms. The ease with which an attacker can apply a malicious YAML file to exploit this flaw further amplifies the risk. While Kubernetes acknowledged the findings, the development team has not classified them as vulnerabilities warranting a patch, primarily because exploiting them requires certain privileges. Nonetheless, the research highlights an essential gap in Kubernetes’ security model, particularly in environments where lateral movement and privilege escalation are viable attack strategies.
In the absence of a patch, organizations are strongly advised to implement the following mitigation strategies:
- Enhanced Monitoring: Increase monitoring of outbound communication from Kubernetes pods, with a focus on identifying suspicious activity, particularly from git-sync pods.
- Audit Git-Sync Pods: Regularly audit git-sync pods using the
kubectl describe pod <git-sync-pod>command to inspect the commands being executed. Any deviations from expected behavior, such as a non-standard--gitargument, should be treated as a potential red flag. - Open Policy Agent (OPA) Rules: Implement OPA rules to detect and prevent the execution of unauthorized binaries within Kubernetes pods.
Given the potentially severe implications of this vulnerability, organizations utilizing Kubernetes are urged to take immediate steps to assess their exposure and implement the recommended mitigations.
Related Posts:
- CVE-2023-32191 (CVSS 10) in Rancher Kubernetes Engine Exposes Sensitive Credentials
- CVE-2024-31989: Critical Argo CD Flaw Exposes Kubernetes Clusters to Takeover
- Attackers Exploit Critical OpenMetadata Flaws for Cryptomining on Kubernetes
- Google Kubernetes Engine Double Flaws: Exploiting FluentBit & ASM for Cluster Takeover





