Upload_Bypass
Upload_Bypass is a powerful tool designed to assist Pentesters and Bug Hunters in testing file upload mechanisms. It leverages various bug bounty techniques to simplify the process of identifying and exploiting vulnerabilities, ensuring thorough assessments of web applications.

- The code almost written from scratch, utilizes better file parsing and eliminates most of the bugs.
- Modular code! Now you can contribute to the code and add your own modules.
- Introducing 3 different modes, detection, exploitation and anti_malware check, choose your weapon!
- New state feature, you can now pause the code and resume from where you left off!
- New UI for an easy view.
- Docker file for an easy deployment.
- Various test files provided for internal testing.
- Debug mode. If you encounter a bug, you can save the stack trace and share it with me for further analysis.
Features
Detection Mode:
Suitable for real-world penetration tests. This mode will upload harmless files and will not attempt to exploit the target.
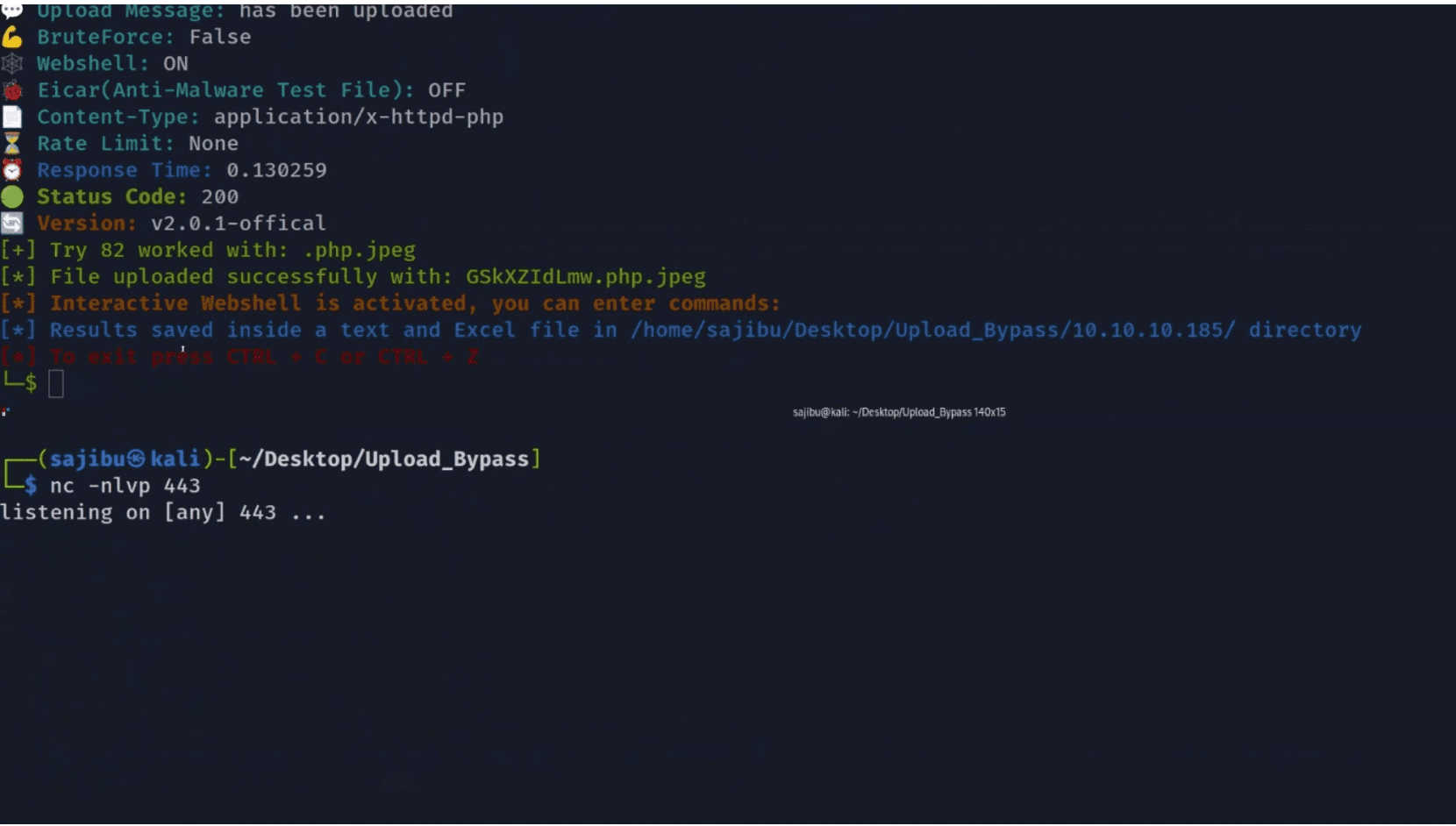
New – If a destination folder for the uploaded files is provided, the program will determine if the uploaded sample file is rendered. For example, if you choose PHP, the program will try to determine if an echo command is executed and rendered successfully, if it does, it’ll suggest to enter an interactive shell.
Exploitation Mode:
Suitable when you want to exploit the target and upload an interactive Web-shell (If a destination upload directory is provided), it will upload the file with a random UUID, so it will be harder for fuzzers to guess.
Anti-Malware mode:
Suitable for an Anti-Malware presence test. Upload an Eicar(Anti-Malware test file) to the system, and if the user specifies the location of the uploaded file, the program will check if the file uploaded successfully and exists in the system in order to determine if an Anti-Malware is present on the system.
Limitations:
The tool will not function properly with the following:
- CAPTCHA implementation is in place.
- A requirement for a CSRF token for each request.
- A destination folder is provided for the uploaded files, but, the uploaded files are saved with a GUID (Globally Unique Identifier) instead of their actual filenames, the program won’t be able to work with it.
Changelog v3.0.2-dev
Updates of version 3.0.1:
- Added 2 new modules:
- Stripping Extension:
Severs might strip forbidden extensions, for example, .php will be stripped from the filename. Therefore, the program will try to upload filename.p.phphp which results in filename.php - Discrepancy:
URL encoding (or double URL encoding) for dots. If the value isn’t decoded when validating the file extension but is later decoded server-side, this can allow to upload of malicious files that would otherwise be blocked. Ex: exploit%2Ephp (Front-end) = exploit.php (Back-end)
- The code is fixed and optimized.
Install & Use
Copyright (C) 2024 sAjibuu