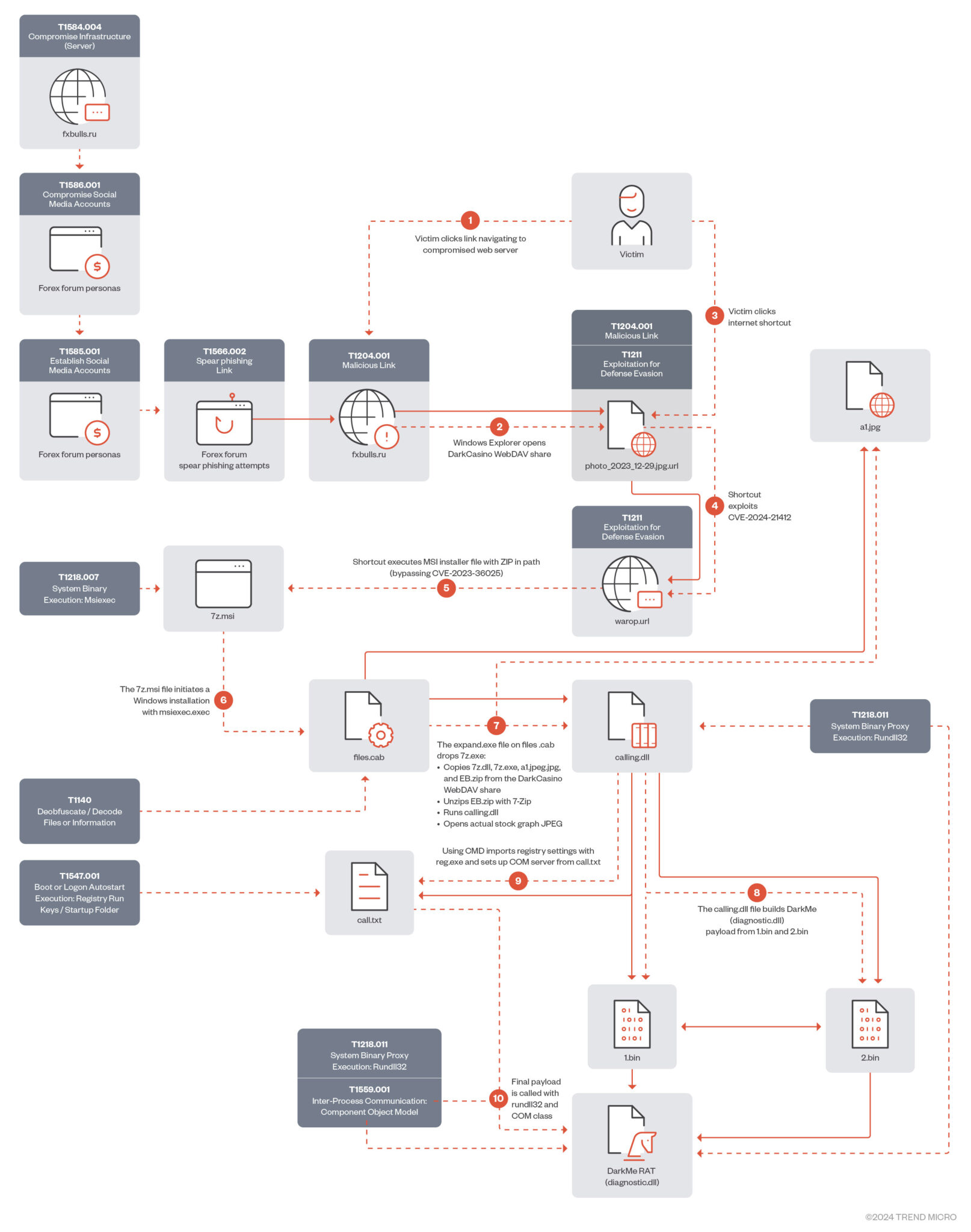
January-February 2024 attack chain
In the ever-evolving landscape of cybersecurity, the emergence of advanced persistent threat (APT) groups represents a formidable challenge to organizations worldwide. Among these, one group has recently surged to prominence, leaving a trail of sophisticated attacks in its wake. Water Hydra, a cyber adversary shrouded in mystery and technical prowess, whose exploits have garnered attention from security researchers and industry experts alike.
The saga begins with a revelation by the Trend Micro Zero Day Initiative (ZDI), uncovering a critical vulnerability tracked as CVE-2024-21412. This vulnerability, exploited by Water Hydra, served as a linchpin in a complex zero-day attack chain, leading to a bypass of Microsoft Defender SmartScreen. This maneuver, executed with surgical precision, targeted financial market traders, signaling the group’s strategic focus and sophistication.
Water Hydra’s origins trace back to 2021, marked by incursions into the financial sector, including banks, cryptocurrency platforms, and stock trading exchanges. Initially mistaken for the Evilnum APT group, Water Hydra’s distinct tactics emerged with the discovery of the DarkCasino campaign in September 2022. By November 2023, the group’s autonomy became evident, solidifying its reputation as a formidable APT entity.

In a December 2023 campaign, the group exploited CVE-2024-21412, leveraging internet shortcuts and WebDAV components to propagate the DarkMe malware. Spearphishing tactics, targeting forex forums and stock trading channels, served as the initial vector, enticing unsuspecting traders with tantalizing offers and fake stock charts.
Central to Water Hydra’s strategy is deception. Compromised websites masquerading as legitimate trading platforms lured victims into a web of deceit, redirecting them to malicious URLs and crafted landing pages. Leveraging obscure protocols like the search: application protocol, the group manipulated Windows Explorer views to cloak malicious activities, evading detection with alarming precision.
The group’s proficiency in exploiting zero-day vulnerabilities is unparalleled. From CVE-2023-38831 to the recent CVE-2024-21412, Water Hydra demonstrates a relentless pursuit of technical innovation, outpacing traditional defense mechanisms. Moreover, the group’s agility in adapting to patched vulnerabilities underscores the perpetual arms race between threat actors and cybersecurity defenders.
“In late December 2023, we began tracking a campaign by the Water Hydra group that contained similar tools, tactics, and procedures (TTPs) that involved abusing internet shortcuts (.URL) and Web-based Distributed Authoring and Versioning (WebDAV) components,” Trend Micro explained.
“We concluded that calling a shortcut within another shortcut was sufficient to evade SmartScreen, which failed to properly apply Mark-of-the-Web (MotW), a critical Windows component that alerts users when opening or running files from an untrusted source.”
The implications of Water Hydra’s actions extend far beyond individual breaches. Zero-day exploits, once unleashed, have the potential to cascade into widespread cyber upheaval, emboldening other APT groups and cyber criminals. The interconnectedness of the cyber threat landscape amplifies the urgency for proactive defense measures and collaboration among stakeholders.