ValleyRAT Campaign Leverages Shellcode and Social Engineering to Target Chinese Speakers
In a recent discovery by FortiGuard Labs, an ongoing cyber campaign has been identified, aggressively deploying the ValleyRAT malware to target Chinese-speaking users. The campaign has a particular focus on the e-commerce, finance, sales, and management sectors.
ValleyRAT is a multi-stage malware designed to infiltrate systems and maintain a low profile while executing a range of malicious activities. What sets ValleyRAT apart from other malware is its reliance on advanced techniques, including the heavy usage of shellcode to execute its components directly in memory. This approach not only reduces the malware’s footprint on the infected system but also makes detection significantly more challenging.
The first stage of the ValleyRAT attack begins with a deceptive tactic: masquerading as legitimate software. The malware uses icons of well-known applications like Microsoft Office, with filenames mimicking financial documents. Examples include filenames such as “工商年报大师.exe” (Industrial and Commercial Annual Report Master.exe) and “3月份涉税财会人员征信拉黑名单如下.exe” (The blacklist of tax-related accounting personnel in March is as follows.exe). This tactic is designed to lure unsuspecting users into executing the malicious files.
Upon execution, the malware ensures it is the only instance running by creating a mutex named “TEST.” It then proceeds to delete specific registry entries potentially left by previous infections and stores critical information, such as the IP and port of its Command and Control (C2) server, in the Windows registry.
ValleyRAT incorporates several advanced evasion techniques to avoid detection by security software and analysis environments. For instance, it checks for virtual machine environments by searching for specific VM-related services. If it detects that it is running in a virtual environment, the malware immediately terminates, avoiding sandbox detection.
Another notable evasion technique is the use of sleep obfuscation. This method involves manipulating memory permissions during the execution of shellcode, making it difficult for memory scanners to detect the malicious code. The malware encodes its shellcode using a simple XOR operation, further complicating detection efforts.
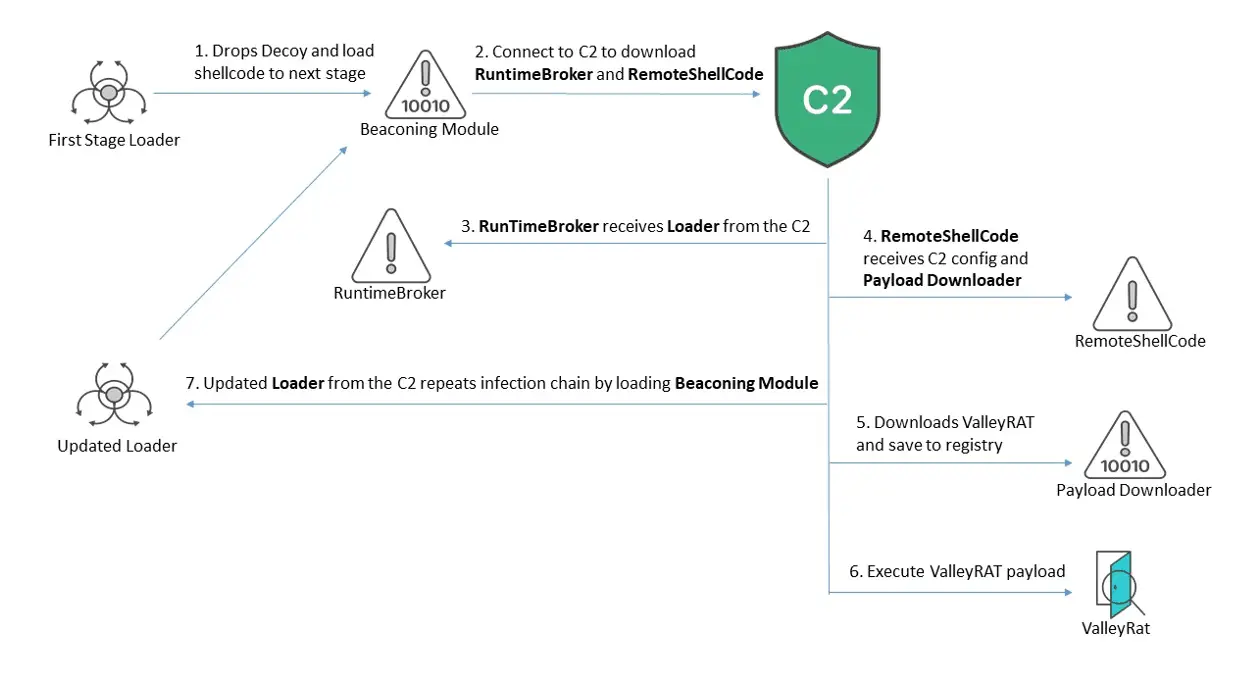
The heart of ValleyRAT’s persistence and impact lies in its use of shellcode for in-memory execution. After initializing, the malware decrypts its shellcode using AES-256, followed by an XOR operation to reveal the final payload. The shellcode then reflectively loads an embedded DLL, typically a beaconing module, which communicates with the C2 server to download additional components, such as the RuntimeBroker and RemoteShellCode.
The beaconing module plays a crucial role in establishing communication with the C2 server and ensuring the malware’s persistence on the victim’s system. It executes commands to gain administrator privileges, disable security software, and set up scheduled tasks for automatic execution upon user login. Additionally, it employs a known technique that abuses the auto-elevate properties of legitimate Windows applications, such as eventvwr.msc, to run its components with elevated privileges without triggering User Account Control (UAC) prompts.
This ValleyRAT campaign serves as a reminder of the constantly evolving tactics, techniques, and procedures (TTPs) employed by cybercriminals to target specific communities. The utilization of shellcode, social engineering, and evasion techniques underscores the importance of maintaining robust security measures and user awareness.





