
CYFIRMA’s Research and Advisory Team has uncovered a new ransomware strain, “VanHelsing”. This discovery was made during routine monitoring of underground forums, a hotbed for cybercriminal activity. The report highlights that VanHelsing is specifically designed to target Windows systems, employing sophisticated encryption techniques to lock user data.
Once executed, VanHelsing ransomware doesn’t just encrypt files; it leverages double extortion tactics. This means that in addition to holding data hostage, it threatens to leak stolen information, adding immense pressure on victims to pay the ransom. The ransomware also modifies the desktop wallpaper and drops a ransom note named “README.txt” on the compromised system. Encrypted files are easily identifiable by the unique “.vanhelsing” extension appended to them.
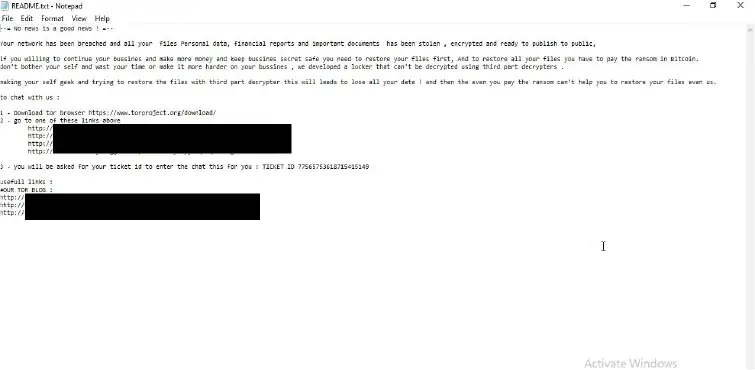
The ransom note itself delivers a chilling message to victims. “Your network has been compromised,” it states, further detailing that sensitive data, including personal details, financial reports, and important documents, have been exfiltrated. The attackers demand an unspecified ransom in Bitcoin for the decryption key. The note also explicitly warns against attempts at self-recovery, stating that such actions could lead to permanent data loss.
CYFIRMA’s investigation reveals that VanHelsing has specific targets. Geographically, the ransomware has been observed targeting France and the USA. Industries in the crosshairs include government, manufacturing, and pharmaceuticals.
The emergence of VanHelsing underscores the critical importance of proactive cybersecurity measures. The report emphasizes the need for robust incident response strategies to protect data integrity and mitigate the risks of breaches. “Its stealthy evasion tactics and persistence mechanisms make detection and removal challenging,” the report states.
Related Posts:
- Hackers use social engineering technique to extortion of bitcoin
- Cybercriminals have been earned over $16 million by distributing ransomware for 2 years
- Lynx Ransomware: The Evolution of INC Ransomware into a Potent Cyber Threat
- Qilin Ransomware Group’s Latest Victims: From Schools to Municipalities