Source: Microsoft Threat Intelligence
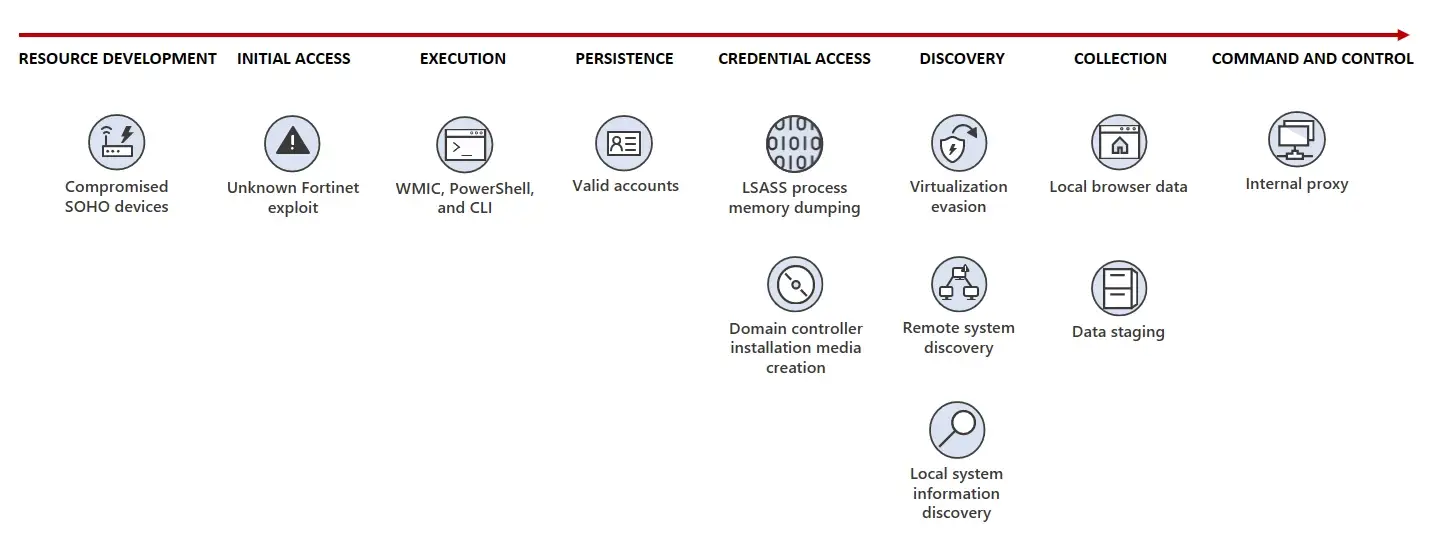
The Tenable Security Response Team has uncovered critical details about Volt Typhoon, a state-sponsored Advanced Persistent Threat (APT) group linked to the People’s Republic of China. The group has been actively targeting U.S. critical infrastructure sectors, including communications, energy, transportation, and water systems, with a focus on maintaining long-term access for potential future operations.
Volt Typhoon specializes in stealth and persistence, employing living-off-the-land (LOTL) tactics to blend in with legitimate system activity. As Tenable highlights: “Volt Typhoon uses native Windows tools like cmd.exe, netsh and PowerShell to execute commands and conduct lateral movement across compromised networks. By avoiding the use of external tools, the group minimizes their digital footprint, making detection through traditional signature-based antivirus systems more challenging.”
Instead of deploying malware, the group exploits legitimate tools to conduct reconnaissance, credential harvesting, and lateral movement. Their targets are carefully selected, and their operations are tailored to specific environments, especially Operational Technology (OT) systems.
Volt Typhoon gains entry by targeting vulnerabilities in publicly exposed systems, particularly firewalls, VPN appliances, and web servers. The group exploits unpatched systems and default or weak credentials, emphasizing the need for robust patch management. “Compromised small-office and home-office (SOHO) routers are often used as intermediary devices, making their traffic appear benign and bypassing geolocation-based firewall rules,” Tenable explains.
Key vulnerabilities exploited by Volt Typhoon include:
| CVE | Description | CVSSv3 Score | VPR |
|---|---|---|---|
| CVE-2021-27860 | FatPipe WARP, IPVPN, MPVPN Unrestricted Upload of File with Dangerous Type | 8.8 | 7.4 |
| CVE-2021-40539 | Zoho ManageEngine ADSelfService Plus Authentication Bypass Vulnerability | 9.8 | 9 |
| CVE-2022-42475 | Fortinet FortiOS and FortiProxy Heap-Based Buffer Overflow Vulnerability | 9.8 | 8.9 |
| CVE-2023-27997 | Fortinet FortiOS and FortiProxy Heap-Based Buffer Overflow Vulnerability | 9.8 | 9 |
| CVE-2024-39717 | Versa Director File Upload Vulnerability | 7.2 | 8.4 |
Volt Typhoon’s operational strategy revolves around avoiding detection by using native tools and legitimate processes. This includes:
- Credential Dumping: Using tools like Mimikatz to extract credentials from memory.
- Persistence Mechanisms: Leveraging Windows Task Scheduler “to establish scheduled tasks for regular access, ensuring long-term surveillance capabilities.”
The group also maintains a low profile by cleaning up logs or rotating them to erase evidence of their presence, further complicating detection efforts.
Volt Typhoon’s operations underscore the persistent and evolving threats posed by state-sponsored APT groups. Their use of stealthy techniques and focus on critical infrastructure highlights the importance of proactive cybersecurity measures.
Related Posts:
- Volt Typhoon APT Group Resurfaces: A Persistent Threat to Critical Infrastructure
- Flax Typhoon Botnet Exploits 66 Vulnerabilities: A Global Threat to Critical Infrastructure
- From Espionage to Theft: The Multi-Faceted APT Attacks on SMBs
- North Korean APT’s Stealth Attack on Open-Source Ecosystems
- VPNs and Clouds: New Tools in the APT Arsenal, ESET Warns