vuls v0.24.3 releases: Vulnerability scanner for Linux/FreeBSD
For a system administrator, having to perform security vulnerability analysis and software updates on a daily basis can be a burden. To avoid downtime in a production environment, it is common for a system administrator to choose not to use the automatic update option provided by the package manager and to perform the update manually. This leads to the following problems.
- A system administrator will have to constantly watch out for any new vulnerabilities in NVD(National Vulnerability Database) or similar databases.
- It might be impossible for the system administrator to monitor all the software if there are a large number of software installed on the server.
- It is expensive to perform analysis to determine the servers affected by new vulnerabilities. The possibility of overlooking a server or two during analysis is there.
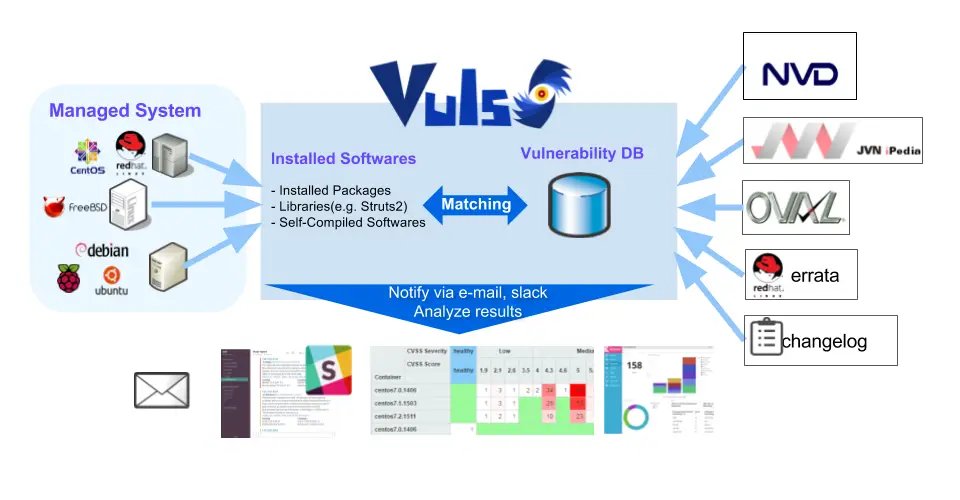
Vuls is a tool created to solve the problems listed above. It has the following characteristics.
- Informs users of the vulnerabilities that are related to the system.
- Informs users of the servers that are affected.
- Vulnerability detection is done automatically to prevent any oversight.
- The report is generated on a regular basis using CRON or other methods. to manage vulnerability.

Main Features
- Scan for any vulnerabilities in Linux/FreeBSD Server
- Supports Ubuntu, Debian, CentOS, Amazon Linux, RHEL, Oracle Linux, FreeBSD and Raspbian
- Cloud, on-premise, Docker
- Scan middleware that are not included in OS package management
- Scan middleware, programming language libraries and framework for vulnerability
- Support software registered in CPE
- Agentless architecture
- User is required to only setup one machine that is connected to other target servers via SSH
- Nondestructive testing
- Pre-authorization is not necessary before scanning on AWS
- Auto-generation of configuration file template
- Auto-detection of servers set using CIDR, generate configuration file template
- Email and Slack notification is possible (supports the Japanese language)
- Scan result is viewable on accessory software, TUI Viewer on the terminal or Web UI (VulsRepo).
Changelog v0.24.3
- 57264e1 fix(scan): fix nil poiter in needs-restarting (#1767)
- 48ff519 chore(deps): bump github.com/gosnmp/gosnmp from 1.35.0 to 1.36.1 (#1763)
DEMO
Download and Tutorial
Copyright (C) 2016 Future Corporation, Japan