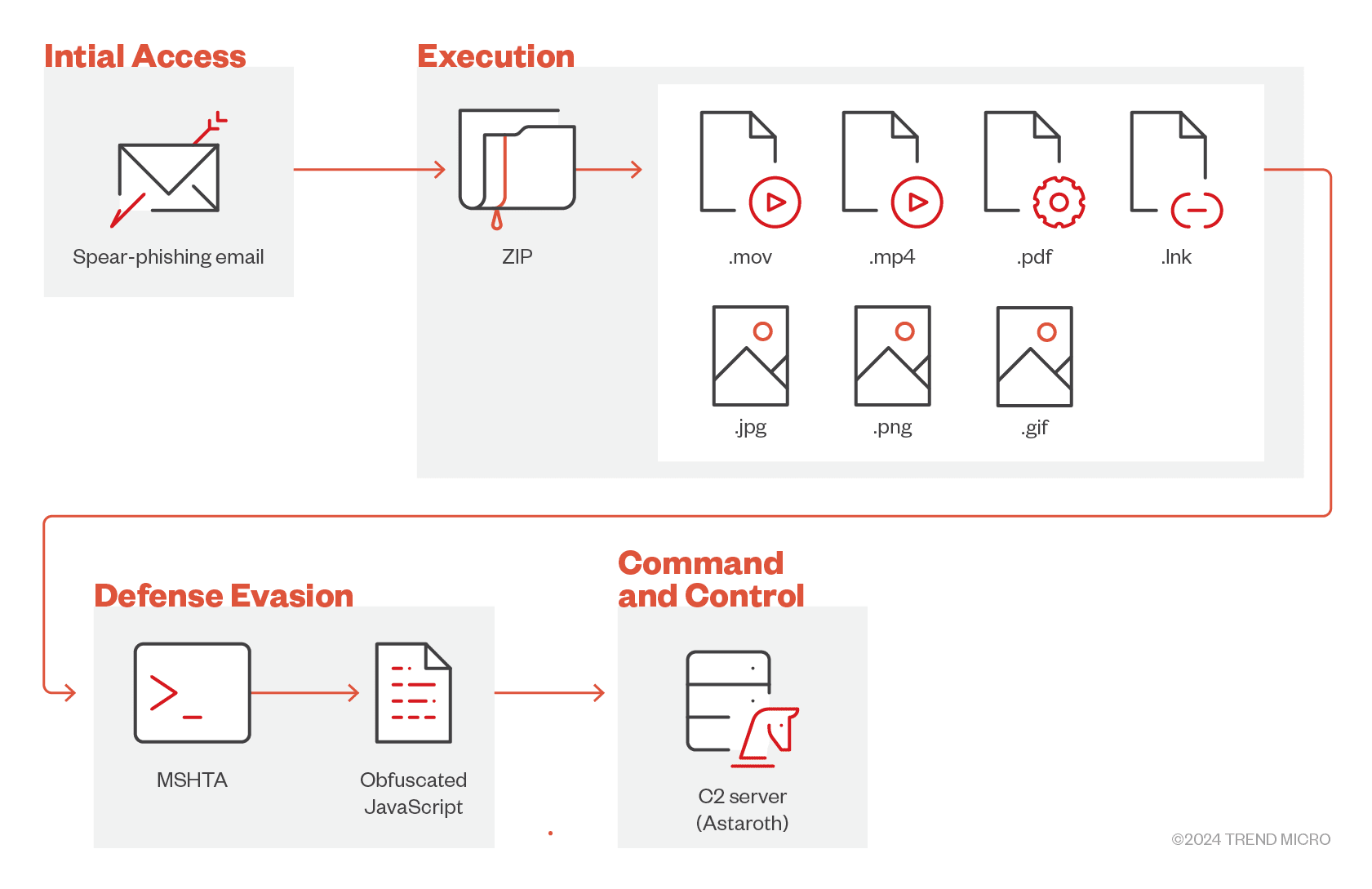
The infection chain of the malware | Image: Trend Micro
In a new report by Trend Micro Research, a spear-phishing campaign has emerged in Brazil, using a combination of obfuscated JavaScript and Astaroth malware to target companies across various industries. The threat actors behind this campaign, tracked as “Water Makara,” have adopted sophisticated techniques to evade detection, posing a serious threat to manufacturing firms, retail businesses, and government agencies in the region.
The campaign begins with phishing emails disguised as official tax notifications or compliance documents, a tactic designed to lure unsuspecting users. According to the report, “these emails come with attachments often masquerading as personal income tax documents,” and inside these attachments are harmful ZIP files. The phishing email, with the subject line “Aviso de Irregularidade” (Notice of Irregularity), tricks recipients into opening ZIP files containing malicious LNK files. These LNK files, when executed, run embedded JavaScript commands through the mshta.exe utility, a legitimate program normally used to execute HTML applications.
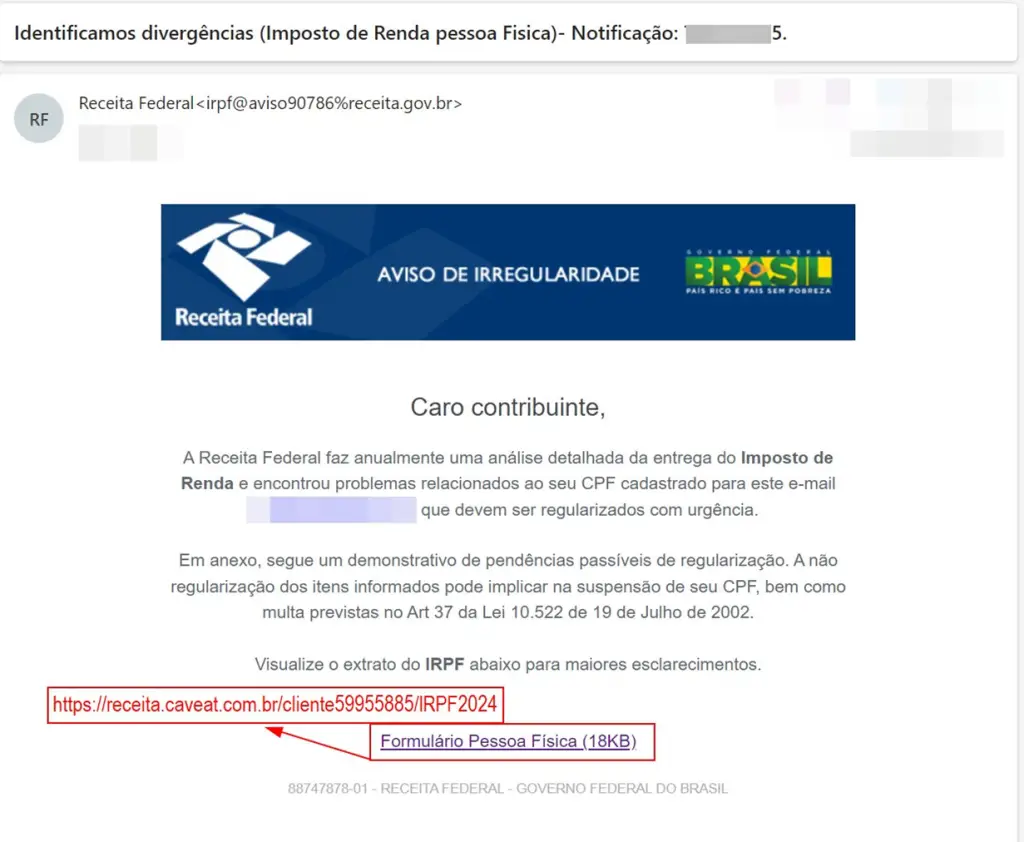
Trend Micro researchers explained, “Aside from the LNK file, the ZIP file also contains another file that has similar obfuscated JavaScript commands,” which are decoded during execution, connecting to a command-and-control (C&C) server to retrieve further instructions.
At the core of this campaign is Astaroth, a notorious banking trojan that steals sensitive information, including credentials and financial data. Once the malware establishes a foothold, it can cause long-term damage, extending beyond data theft to include regulatory fines, business disruption, and loss of consumer trust. “While Astaroth might seem like an old banking trojan, its reemergence and continued evolution make it a persistent threat,” warns the report.
Water Makara employs advanced obfuscation techniques, making detection difficult. The researchers found encoded JavaScript commands that lead to malicious URLs, such as patrimoniosoberano[.]world. These URLs follow a domain generation algorithm (DGA), a tactic used by cybercriminals to create vast numbers of domains, thus avoiding detection.
Manufacturing, retail, and government sectors in Brazil are the primary targets of this campaign. “The spear phishing campaigns mostly target companies in Brazil,” the report states, “with manufacturing companies, retail firms, and government agencies being the most affected.”
“Water Makara’s spear phishing campaign relies on unwitting users clicking on the malicious files, which underscores the critical role of human awareness,” the report concludes.
As Brazil continues to face increasing threats from sophisticated cyber actors, defending against these highly targeted spear phishing campaigns will require a multi-layered approach, blending technical defenses with robust user education.
Related Posts:
- Brazil’s Cybersecurity Landscape: A Fusion of Global and Local Threats
- Urgent: Water Hydra Exploits Zero-Day to Target Traders
- Attack demonstration took kits for Industry 4.0 using AI and cloud
- Trendmicro: Mirai-like Scanning from China targets Brazil
- Morphisec discovered a new watering hole attack based Flash flaw on Leading Hong Kong Telecom Site
- From Spear-Phishing to Zero-Day: Lazarus Group’s Latest Cyber Strategies