wazuh v4.7 releases: Host and endpoint security
Wazuh
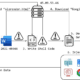
Wazuh helps you to gain deeper security visibility into your infrastructure by monitoring hosts at an operating system and application level. This solution, based on lightweight multi-platform agents, provides the following capabilities:
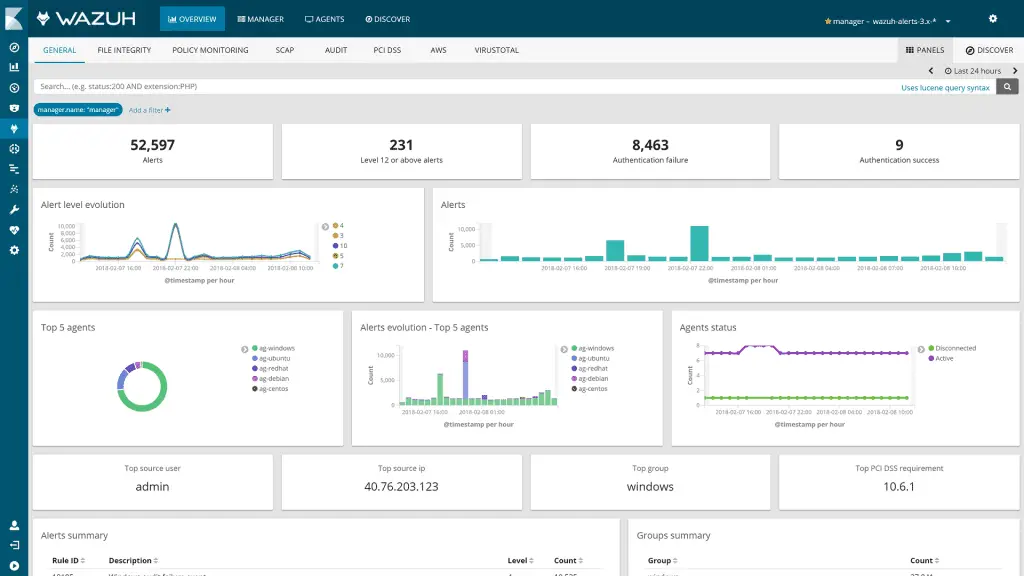
- Log management and analysis: Wazuh agents read the operating system and application logs, and securely forward them to a central manager for rule-based analysis and storage.
- File integrity monitoring: Wazuh monitors the file system, identifying changes in content, permissions, ownership, and attributes of files that you need to keep an eye on.
- Intrusion and anomaly detection: Agents scan the system looking for malware, rootkits or suspicious anomalies. They can detect hidden files, cloaked processes or unregistered network listeners, as well as inconsistencies in system call responses.
- Policy and compliance monitoring: Wazuh monitors configuration files to ensure they are compliant with your security policies, standards or hardening guides. Agents perform periodic scans to detect applications that are known to be vulnerable, unpatched, or insecurely configured.
This diverse set of capabilities is provided by integrating OSSEC, OpenSCAP and Elastic Stack, making them work together as a unified solution, and simplifying their configuration and management.
It provides an updated log analysis ruleset and a RESTful API that allows you to monitor the status and configuration of all Wazuh agents.
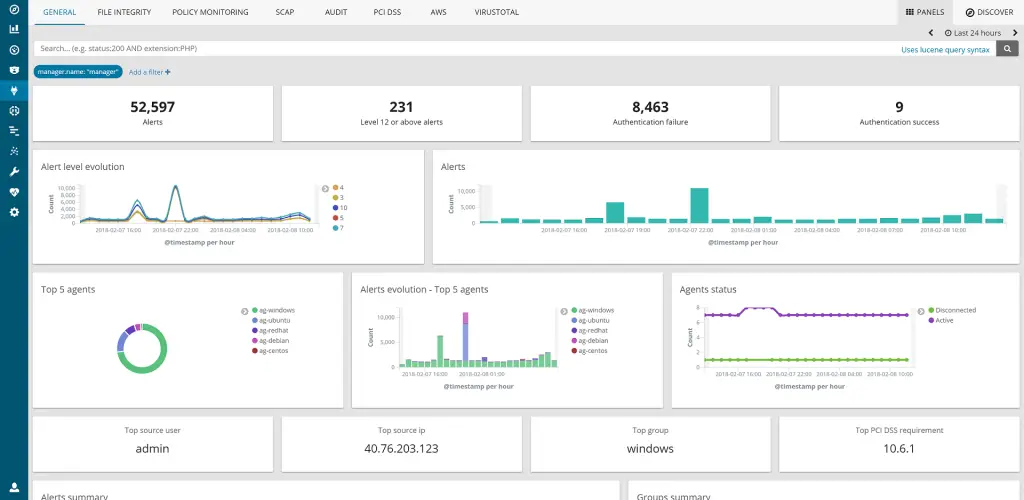
It also includes a rich web application (fully integrated as a Kibana app), for mining log analysis alerts and for monitoring and managing your Wazuh infrastructure.
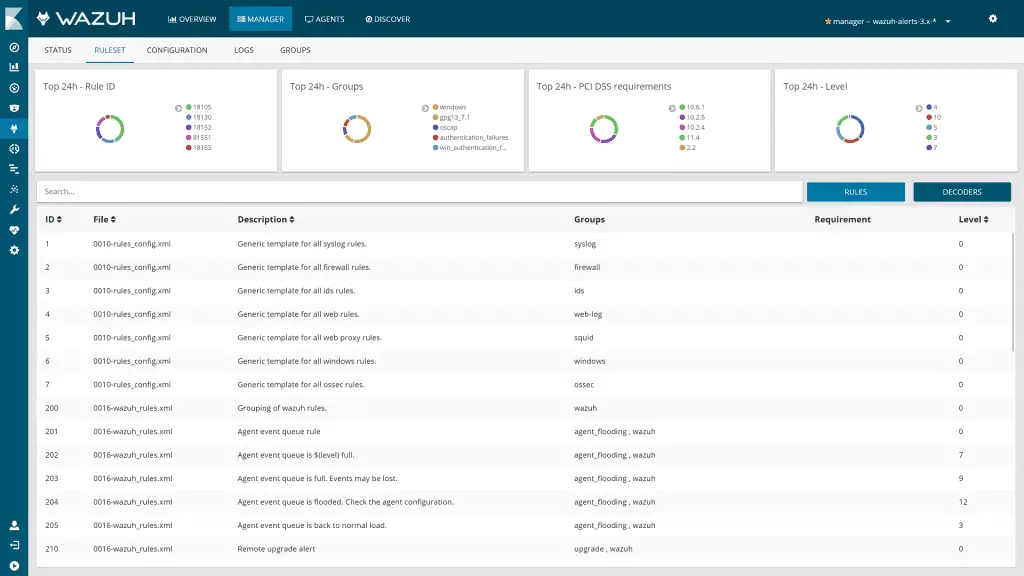
Changelog v4.7
Manager
Added
- Introduced native Maltiverse integration. Thanks to David Gil (@dgilm). (#18026)
- Added a file detailing the dependencies for the Wazuh RESTful API and wodles tests. (#16513)
- Added unit tests for the Syscollector legacy decoder. (#15985)
- Added unit tests for the manage_agents tool. (#15999)
- Added an option to customize the Slack integration. (#16090)
- Added support for Amazon Linux 2023 in Vulnerability Detector. (#17617)
Changed
- An unnecessary sanity check related to Syscollector has been removed from wazuh-db. (#16008)
- The manager now rejects agents with a higher version by default. (#20367)
Fixed
- Fixed an unexpected error by the Cluster when a worker gets restarted. (#16683)
- Fixed an issue that let the manager validate wrong XML configurations. (#16681)
- Fixed syscollector packages multiarch values (#19722)
- Fixed wazuh-agent crash randomly when RPCRT4.dll is loaded (#18591)
Deleted
- Delete unused framework RBAC migration folder. (#17225)
Agent
Added
- Added support for Custom Logs in Buckets via AWS SQS. (#17951)
- Added geolocation for
aws.data.client_ipfield. Thanks to @rh0dy. (#16198) - Added package inventory support for Alpine Linux in Syscollector. (#15699)
- Added package inventory support for MacPorts in Syscollector. (#15877)
- Added package inventory support for PYPI and node in Syscollector. (#17982)
- Added related process information to the open ports inventory in Syscollector. (#15000)
Changed
- The shared modules’ code has been sanitized according to the convention. (#17966)
- The package inventory internal messages have been modified to honor the schema compliance. (#18006)
- The agent connection log has been updated to clarify that the agent must connect to an agent with the same or higher version. (#20360)
Fixed
- Fixed detection of osquery 5.4.0+ running outside the integration. (#17006)
- Fixed vendor data in package inventory for Brew packages on macOS. (#16089)
- Fixed WPK rollback restarting host in Windows agent (#20081)
RESTful API
Added
- Added new
status_codefield toGET /agentsresponse. (#19726)
Fixed
- Addressed error handling for non-utf-8 encoded file readings. (#16489)
- Resolved an issue in the
WazuhExceptionclass that disrupted the API executor subprocess. (#16914) - Corrected an empty value problem in the API specification key. (#16918)
Deleted
- Deprecated
PUT /vulnerability,GET /vulnerability/{agent_id},GET /vulnerability/{agent_id}/last_scanandGET /vulnerability/{agent_id}/summary/{field}API endpoints. In future versions, the Wazuh indexer REST API can be used instead. (#20126)
Other
Fixed
- Fixed the signature of the internal function
OSHash_GetIndex(). (#17040)
Download && Use
Portions Copyright (C) 2017 Wazuh, Inc.
Based on work Copyright (C) 2003 – 2013 Trend Micro, Inc.