webstor v0.1.15 releases: Fast Identification of Vulnerable Web Technologies in your Organization
WebStor
Fast Identification of Vulnerable Web Technologies in your Organization
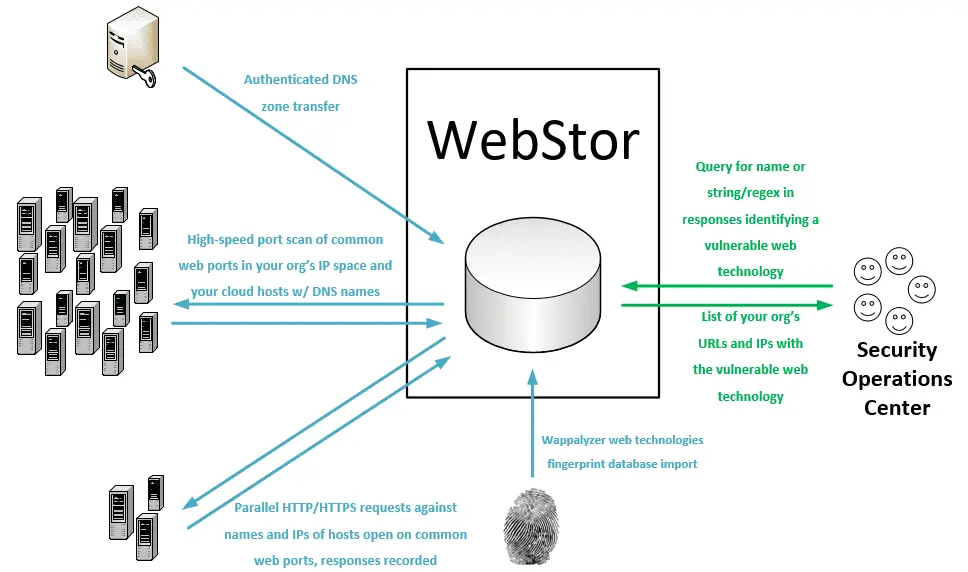
WebStor is a tool implemented in Python under the MIT license for quickly enumerating all websites across all of your organization’s networks, storing their responses, and querying for known web technologies and versions, such as those with zero-day vulnerabilities. It is intended, in particular, to solve the unique problem presented in mid to large sized organizations with decentralized administration, wherein it can be almost impossible to track all of the web technologies deployed by various administrators distributed across different units and networks.

WebStor achieves its goal by performing the following actions:
- Performs DNS zone transfers to collect an organization’s A and CNAME records.
- Uses Masscan to scan for open HTTP/HTTPS ports on an organization’s net ranges, as well as any IP addresses outside those ranges that were present in the organization’s A and CNAME records.
- Uses the Python requests library to collect all responses and store them in a MariaDB database. All DNS names corresponding to an IP with open HTTP/HTTPS ports will be included in requests in addition to the IP address so that sites using different headers will not cause a website to be missed.
- Downloads Wappalyzer web technologies database and stores in MariaDB database, enabling users to query the location(s) of common web technology by name.
- Allows users to query the location(s) where custom regexes are contained within stored responses.
Changelog v0.1.15
Improvements to adding Wappalyzer Technologies, making tsig key more independent of file type, and fixing key assignment by afreudenreich
Install & Use
Copyright (c) 2020-2021 The University of Michigan Board of Regents.





