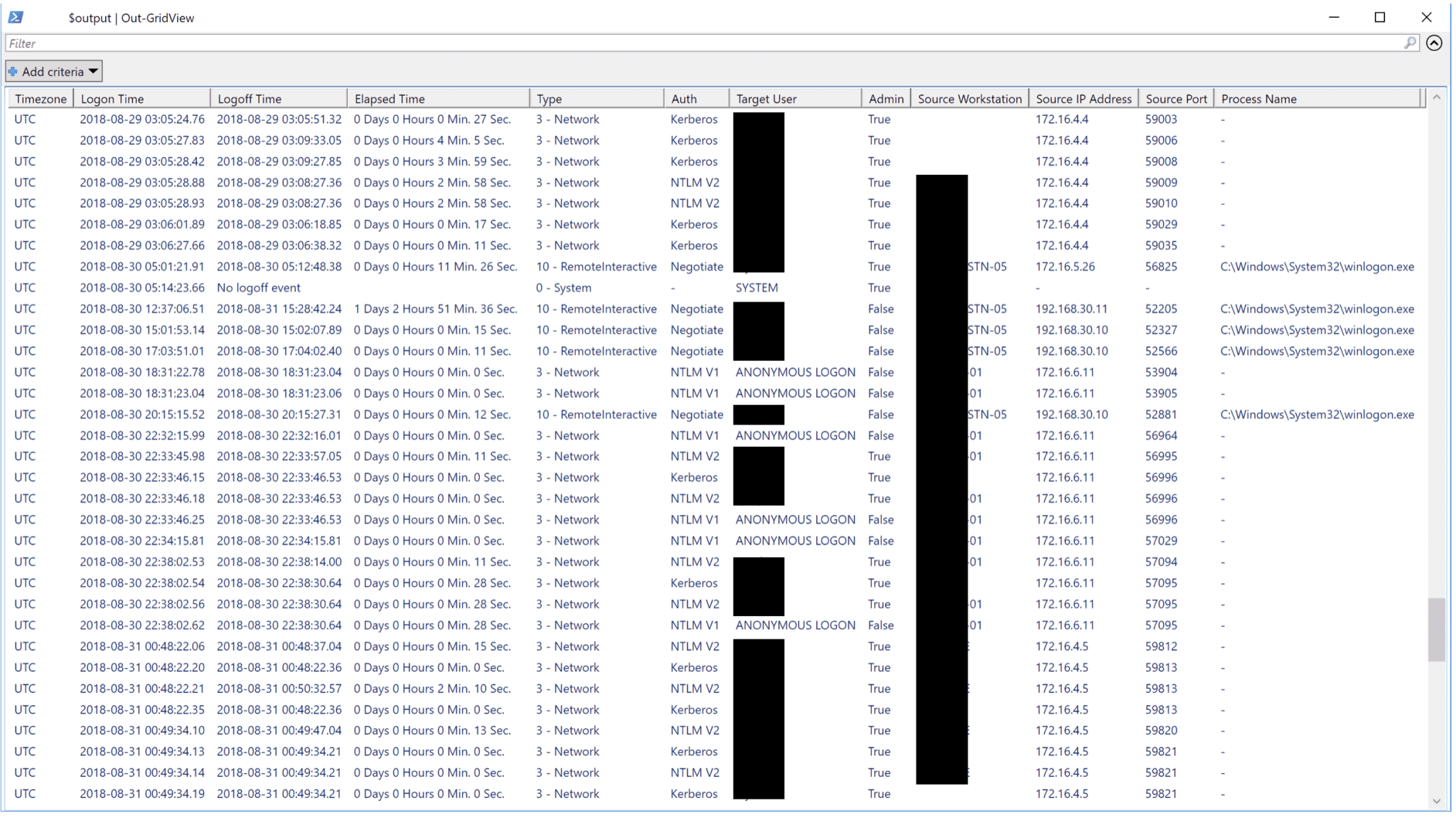
Logon Timeline GUI
WELA (Windows Event Log Analyzer)
Yamato Security’s WELA(Windows Event Log Analyzer) aims to be the Swiss Army knife for Windows event logs. Currently, WELA’s greatest functionality is creating an easy-to-analyze logon timeline in order to aid in fast forensics and incident response. WELA’s logon timeline generator will consolidate only the useful information in multiple logon log entries (4624, 4634, 4647, 4672, 4776) into single events, perform data reduction by ignoring around 90% of the noise, and will convert any hard to read data (such as hex status codes) into human-readable format.
Tested on Windows Powershell 5.1 but may work with previous versions. It will unfortunately NOT work with Powershell Core as there is no built-in functionality to read Windows event logs.

Features
- Written in PowerShell so is easy to read and customize.
- Fast Forensics Logon Timeline Generator
- Detect lateral movement, system usage, suspicious logons, vulnerable protocol usage, etc…
- 90%+ noise reduction for logon events
- Calculate Logon Elapsed Time
- GUI analysis
- Logon Type Summary
- Live Analysis and Offline Analysis
- Japanese support
- Event ID Statistics
- Output to CSV to analyze in Timeline Explorer, etc…
- Analyze NTLM usage before disabling NTLM
- Sigma rules
- Custom attack detection rules
- Remote analysis
- Logon Statistics
Download & Use
Copyright (C) 2021 Yamato-Security