WhiskeySAML and Friends: GoldenSAML Attack Libraries and Framework
WhiskeySAML and Friends
TicketsPlease
TicketsPlease: Python library to assist with the generation of Kerberos tickets, remote retrieval of ADFS configuration settings, generation of Golden SAML tokens, and retrieval of Azure Access Tokens.
- Modules
- ldap
This module will perform an LDAP query to retrieve one of the following:
- The DKM master key
- The UPN, GUID, and SID of a specified user
- dcsync
This module will perform a DCSync operation to retrieve the SID and password hash of a given user. This wraps the pypykatz library DCSync handling.
- ticket
This module will generate a Kerberos ticket. It will either build a default KRB_TGT or if the –ap-req flag is provided, a ticket with the following hierarchy:
- How It Works
Step Process 1a If the required data (both the target user SID and hash) are not provided, a DCSync operation is performed to retrieve it. 1b If only the target user hash has been provided, an LDAP query is made to retrieve the target user SID. 2 Using the SID and hash of the target user, a KRB_TGT object is created via Impacket’s ticketer.py. 3 The KRB_TGT object is then wrapped in a custom AP_REQ message. 4 The AP_REQ message is then wrapped in a final SPNEGO_NegTokenInit message.
- How It Works
- adfs
This module will remotely pull down the ADFS configuration settings. This is based on the AADInternals function: Export-ADFSConfiguration.
- How It Works
Step Process 1 The provided kerberos ticket is sent to the ADFS server in an RST (RequestSecurityToken) envelope. 2 The RST response is parsed and sent back to the ADFS server as a SCT (SecurityContextToken) envelope. 3 Finally, the token is parsed from the SCT response and sent to the ADFS server requesting the configuration settings.
- How It Works
- saml
This module will generate a Golden SAML token using the EncryptedPfx extracted from an ADFS configuration and the DKM key pulled from a domain.
- How It Works
Step Process 1 Using LDAP, query the Domain Controller for the target user’s (we are impersonating) UPN (userPrincipalName) and GUID (objectGuid) (if not provided). 2 Using LDAP, query the Domain Controller for the DKM (Distributed Key Manager) key (if not provided). 3 Decrypt the EncryptedPfx extracted from the ADFS configuration by deriving the keys from the DKM. 4 Generate and sign a Golden SAML ticket using the DecryptedPfx and the target user’s UPN and GUID.
- How It Works
- azure
This module will request Access Tokens from a specified Azure API endpoint using either a Kerberos ticket or a Golden SAML token.
- How It Works
Kerberos Ticket
Step Process 1 An RST (RequestSecurityToken) envelope with the provided Kerberos ticket as an auth bearer is sent to Microsoft. 2 The RST response is parsed for the security token. 3 The security token is sent in a request to the Azure API endpoint requesting an access token. Golden SAML
Step Process 1 The provided Golden SAML token is sent in a request to the Azure API endpoint requesting an access token.
- How It Works
- ldap
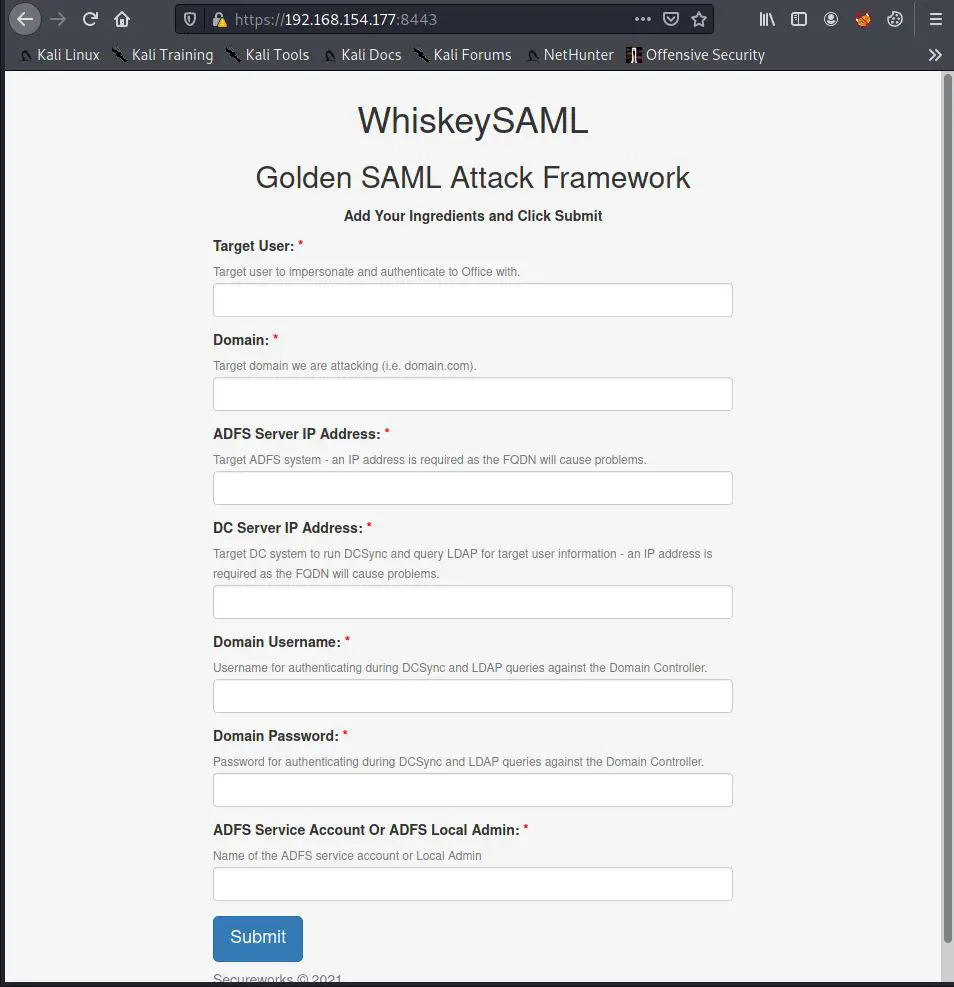
WhiskeySAML
WhiskeySAML: Proof of concept tool for a Golden SAML attack with Remote ADFS Configuration Extraction. This tool leverages the TicketsPlease library.

ShockNAwe
ShockNAwe: Proof of concept tool to generate a Golden SAML token that will be used to request an Access Token from Azure Core Management which will then be used to enumerate and attack the virtual machines within the Azure subscription.
Download & Use
Copyright (C) 2022 secureworks





