Event logs confirmed during Bisamware execution | Image: JPCERT/CC
Human-operated ransomware represents a particularly insidious challenge, combining sophisticated techniques with manual execution to evade traditional security measures. A new report from the Japan Computer Emergency Response Team Coordination Center (JPCERT/CC) illuminates the potential of Windows Event Logs as a potent tool in the fight against this evolving threat.
Unlike automated ransomware attacks, human-operated ransomware leverages the expertise of skilled threat actors who navigate victim networks, exfiltrating data and strategically deploying encryption. This hands-on approach allows attackers to bypass standard security defenses, necessitating advanced detection and response capabilities.
The JPCERT/CC report underscores the value of Windows Event Logs as a source of crucial forensic evidence. By examining event log patterns, security professionals can identify and attribute human-operated ransomware, aiding in timely containment and mitigation efforts.
- Conti Ransomware
First identified in 2020, Conti ransomware is notorious for exploiting Windows Restart Manager to facilitate file encryption. A large number of event logs (Event IDs: 10000, 10001) are generated in a short span when Conti is executed, providing a clear indication of its presence on a compromised machine. Interestingly, ransomware variants like Akira and Lockbit 3.0, which share similarities with Conti, also generate similar event logs.
- Phobos Ransomware
Phobos, a variant of the Dharma ransomware, leaves a trail of destruction by deleting system backup catalogs and volume shadow copies. Notably, it generates Event IDs such as 612 and 524 during execution, which can be used to track its activities. Other ransomware like 8base and Elbie exhibit similar behavior, potentially linked to the Phobos ransomware group.
- Midas Ransomware
Midas, identified in 2021, leaves event logs related to changes in network settings during its execution. For example, Event ID 7040 records modifications to network service configurations, such as SSDP Discovery and UPnP Device Host, which are essential for spreading the ransomware across a network. Axxes ransomware, suspected to be a variant of Midas, shows similar traits.
- BadRabbit Ransomware
First confirmed in 2017, BadRabbit ransomware’s execution is marked by Event ID 7045, which logs the installation of the encryption component cscc.dat. This log can be a telling sign of a BadRabbit infection, helping investigators trace the attack’s origin.
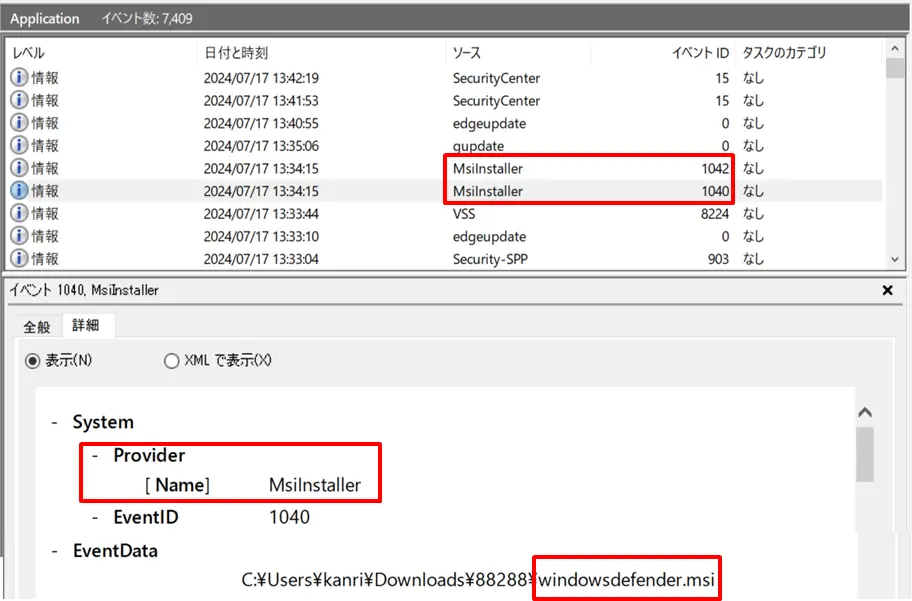
- Bisamware Ransomware
Discovered in 2022, Bisamware takes advantage of vulnerabilities in Microsoft tools to infect Windows users. When this ransomware is executed, Event IDs 1040 and 1042 log the start and end of the Windows Installer transaction, providing concrete evidence of Bisamware activity.
JPCERT/CC also discovered event log traces common across multiple ransomware strains. For instance, ransomware like GandCrab, AKO, and BLACKBASTA often leave behind Event IDs 13 and 10016 when they fail to access COM server applications tied to the Volume Shadow Copy Service.
This recurring pattern suggests that even when ransomware doesn’t function as intended, the event logs can still reveal critical insights, making them an essential asset in damage investigations and ransomware attribution.
The report emphasizes that Windows Event Logs should not be overlooked in ransomware investigations. While event logs alone may not provide a complete picture, they can offer valuable clues when traditional identification methods, like ransom notes or encrypted file extensions, fall short.
By analyzing these logs, security teams can detect ransomware traces early, potentially reducing downtime and financial impact. Moreover, with the rise of new ransomware variants, these logs can help professionals keep pace with attackers’ evolving tactics.
Related Posts:
- Conti ransomware source code leaks
- ZeroLogon to NoPac Vulnerability: Black Basta Group’s Exploit Arsenal Revealed
- Google ban fake ID apps on Play Store