A critical use-after-free vulnerability, identified as CVE-2024-38193, has been discovered in the afd.sys Windows driver. This vulnerability, with a CVSS score of 7.8, poses a significant threat to Windows systems, potentially allowing attackers to escalate privileges and execute arbitrary code. Security researcher Luca Ginex at Exodus Intelligence has conducted an in-depth analysis of this vulnerability, providing valuable insights into its exploitation process.
Gen Digital, the security research company that discovered and reported the vulnerability to Microsoft, stated that this flaw allows attackers to bypass normal security restrictions and access sensitive system areas that are typically inaccessible to most users and administrators. This attack is both complex and cunning, potentially worth hundreds of thousands of dollars on the black market.
The researchers disclosed their tracing and attribution results, revealing that the Lazarus Group has been using this vulnerability to install malware known as FudModule. This malware is highly sophisticated and was initially detected by researchers from AhnLab and ESET in 2022.
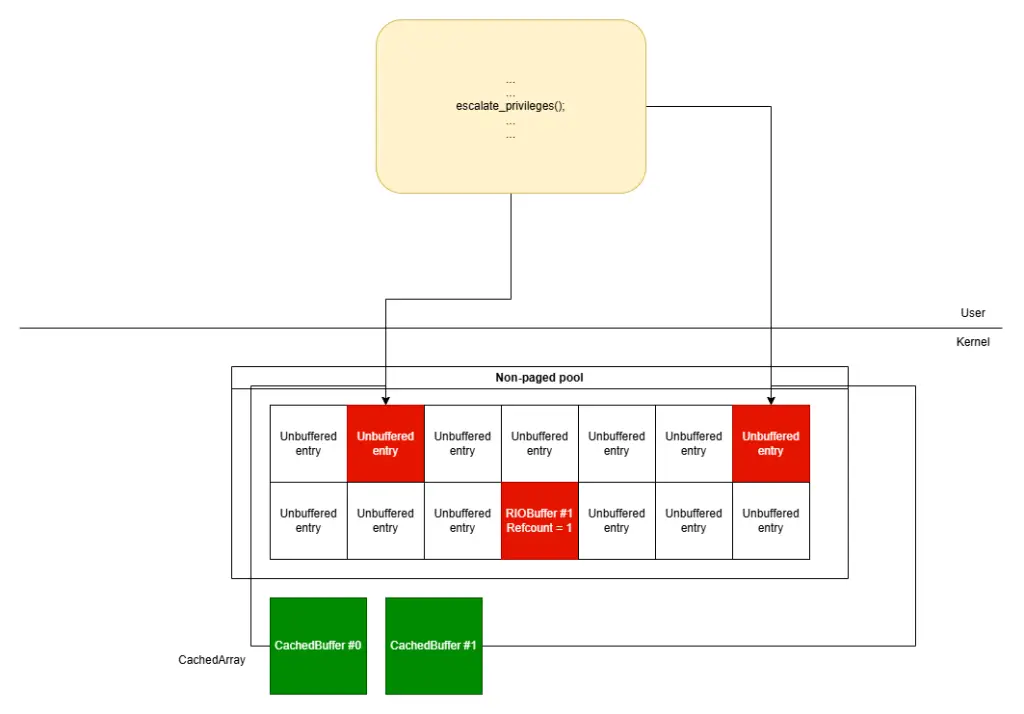
CVE-2024-38193 resides in the Registered I/O (RIO) extension for Windows sockets, a feature designed to optimize socket programming by reducing system calls. The vulnerability stems from a race condition between the AfdRioGetAndCacheBuffer() and AfdRioDereferenceBuffer() functions within the afd.sys driver. As Ginex explains, “The race condition between these functions allows a malicious user to force the AfdRioGetAndCacheBuffer() function to act on a registered buffer structure that has been freed by the AfdRioDereferenceBuffer() function.”
The exploitation of CVE-2024-38193 involves a multi-stage process, as outlined by Ginex:
- Heap Spraying: The attacker sprays the non-paged pool with fake RIOBuffer structures and creates holes, paving the way for the vulnerability to be triggered.
- Triggering the Vulnerability: By creating two concurrent threads, the attacker deregisters buffers while they are still in use, leading to a use-after-free scenario.
- Privilege Escalation: The attacker leverages the freed RIOBuffer structures to gain control over the contents of the cache and escalate privileges.
The exploit uses this arbitrary write capability to overwrite the _SEP_TOKEN_PRIVILEGES structure, granting NT AUTHORITY\SYSTEM privileges.
Nephster, an independent security researcher, has published proof-of-concept (PoC) code for the CVE-2024-38193 vulnerability on GitHub, further escalating its potential threat. The PoC demonstrates how attackers can reliably achieve privilege escalation on unpatched systems.
This vulnerability has been patched in the August 2024 Patch Tuesday. Users are strongly advised to apply the patch to mitigate the risk of potential attacks. The exploitation of CVE-2024-38193 could lead to privilege escalation, allowing attackers to gain unauthorized access to sensitive data and potentially take full control of the system.
Related Posts:
- Lazarus Group Exploits Microsoft Zero-Days CVE-2024-38193, Patch Urgently
- Mozilla releases emergency update to fix two exploited zero-day vulnerabilities in Firefox
- VmWare release the patch to fix use-after-free and integer-overflow vulnerabilities
- QR Codes Coming to Linux Kernel Panics with 6.12 Release