Security researcher Siddharth Dushantha has uncovered a vulnerability in WinRAR, the popular file compression software, that could be exploited to deceive users or even cause system crashes. The vulnerability, which affects the console versions of RAR and UnRAR, is tracked as CVE-2024-33899 for Linux and Unix systems and CVE-2024-36052 for Windows systems. This vulnerability, which allows attackers to inject ANSI escape sequences, has been patched in version 7.00. The GUI version of WinRAR and the UnRAR library were not impacted.
ANSI escape sequences are special codes used to control text formatting, colors, and cursor positioning in terminals. While commonly used to create visually appealing command-line interfaces, they can also be weaponized. Dushantha demonstrated how attackers could leverage this vulnerability to:
- Spoof File Listings: By injecting malicious ANSI codes into archive comments, attackers could create fake file listings, potentially tricking users into opening harmful files disguised as harmless ones.
- Denial of Service (Linux/Unix): Specific ANSI sequences can trigger a local denial-of-service condition on Linux and Unix systems, rendering the terminal unusable.
The vulnerability (CVE-2024-33899 for Linux/Unix, CVE-2024-36052 for Windows) poses a greater threat on Linux and Unix due to the potential for denial-of-service attacks. While Windows users are still vulnerable to the spoofing aspect, the impact is less severe.
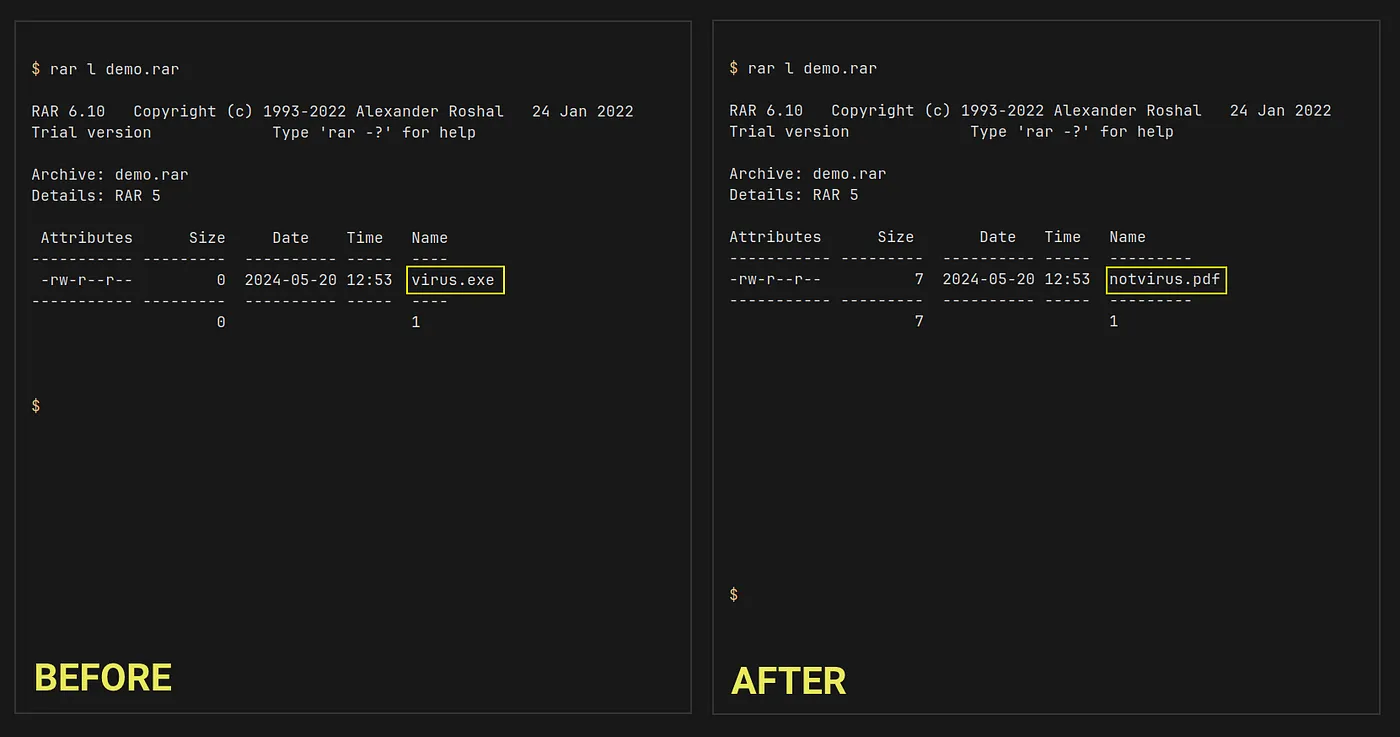
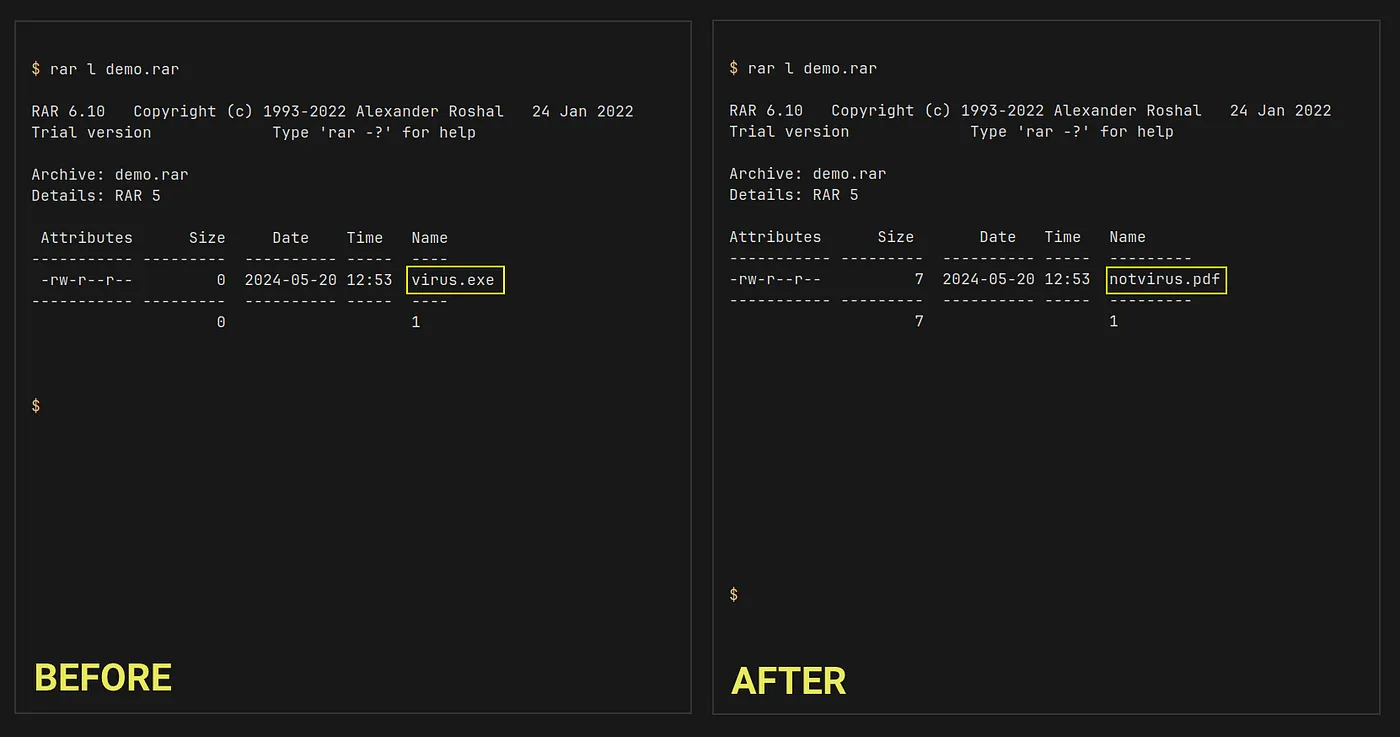
Dushantha provided a proof-of-concept exploit showcasing how an attacker could hide a malicious file (e.g., virus.exe) within an archive and replace its name in the file listing with a seemingly harmless one (e.g., notvirus.pdf). This deceptive tactic could easily mislead unsuspecting users.
RARLAB, the developer of WinRAR, has addressed this vulnerability in version 7.00. Users are strongly advised to update their software immediately to protect themselves from potential attacks.