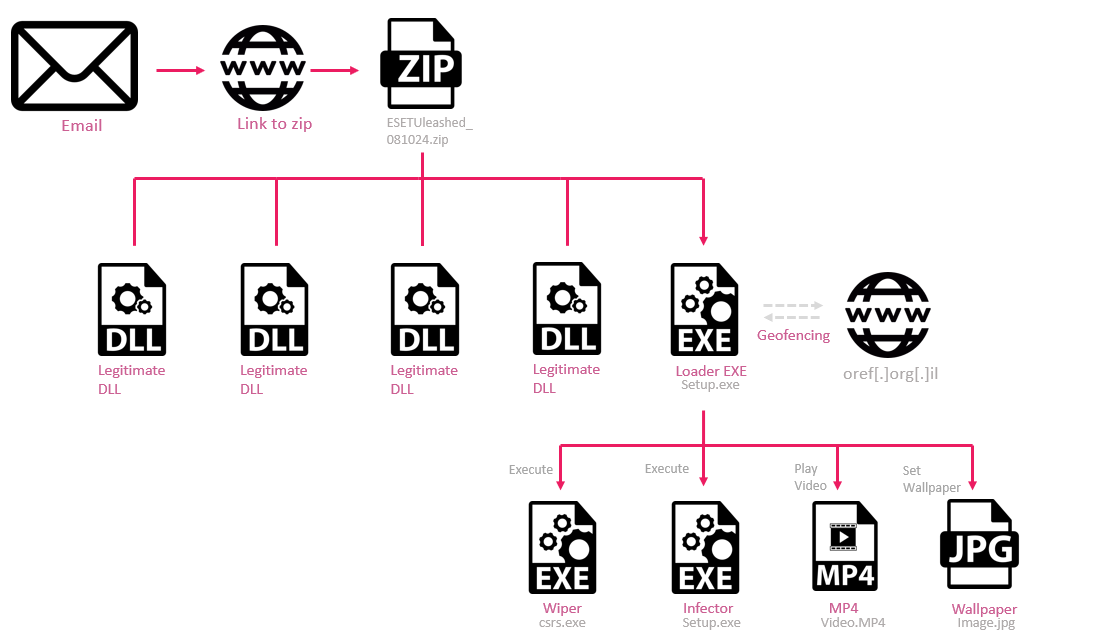
Wiper Infection Chains | Image: Check Point
Check Point Research recently exposed ongoing activity from WIRTE, a Hamas-affiliated cyber-espionage group, that continues despite the intensifying conflict in the Middle East. Historically focused on espionage, WIRTE has expanded its operations in 2024 to include disruptive attacks, particularly targeting Israel.
The report states, “The conflict has not disrupted the WIRTE’s activity, and they continue to leverage recent events in the region in their espionage operations, likely targeting entities in the Palestinian Authority, Jordan, Iraq, Egypt, and Saudi Arabia.”
WIRTE, first documented in 2019, has a history of targeting organizations across the Middle East for intelligence gathering. In 2024, however, Check Point observed WIRTE employing SameCoin, a custom wiper malware, to attack Israeli entities in February and October. This change signals a new dual-purpose approach for the group: espionage throughout the Middle East and targeted disruption in Israel. The group’s disruptive operations are bolstered by “clear links between the custom malware used by the group and SameCoin, a wiper malware targeting Israeli entities”.
WIRTE’s campaigns leverage carefully crafted lures tailored to regional issues, often presented through malicious PDF files and archives. A recent infection chain involved a PDF titled Developments of the War in Lebanon which led users to a RAR file containing DLL files used to deliver malicious payloads. Through these methods, WIRTE remains highly active in espionage campaigns, targeting the Palestinian Authority and several neighboring countries.
Additionally, the group has employed user-agent filtering and HTML-based payload embedding to avoid detection. WIRTE’s infrastructure includes domains like saudiarabianow[.]org and egyptican[.]com that resemble legitimate sites, adding a further layer of sophistication. Check Point notes, “WIRTE’s tools have evolved… key aspects of their operations remain consistent: domain naming conventions, communication via HTML tags, responses limited to specific user agents, and redirection to legitimate websites.”
The group’s use of SameCoin wiper malware in recent months indicates a shift toward more aggressive tactics, specifically aimed at Israel. In October 2024, emails mimicking an Israeli ESET reseller deployed a new variant of the wiper to Israeli hospitals and municipalities, with embedded propaganda content supporting Hamas. The malware, designed to activate only in Israeli environments, “uses the first bytes of the response as its XOR key” to verify Israeli targets.
WIRTE’s recent activities reflect a troubling expansion from traditional espionage to disruption, with new capabilities and a versatile toolkit. The group’s persistent presence and evolving methods underline the significant threat WIRTE poses in the Middle East, especially as geopolitical tensions continue. The report concludes, “Despite ongoing conflict in the Middle East, the group has persisted… showcasing a versatile toolkit that includes Wipers, Backdoors, and Phishing pages used for both espionage and sabotage.”
Related Posts:
- Israel suffers largest DDoS attack ever: Many government websites go offline
- Israeli cyber security is among the top five in the world
- 1 Hosting Hack, 40 Israeli Leaks: Cyber Toufan’s Shadowy Strike
- Iranian APT hacker organisation falsifies Israeli security companies official website to implement phishing activities
- CrowdStrike Bug Exploited: Handala Hacking Team Targets Israel