Wish Stealer: New Malware Targets Discord, Browsers, and Cryptocurrency Wallets
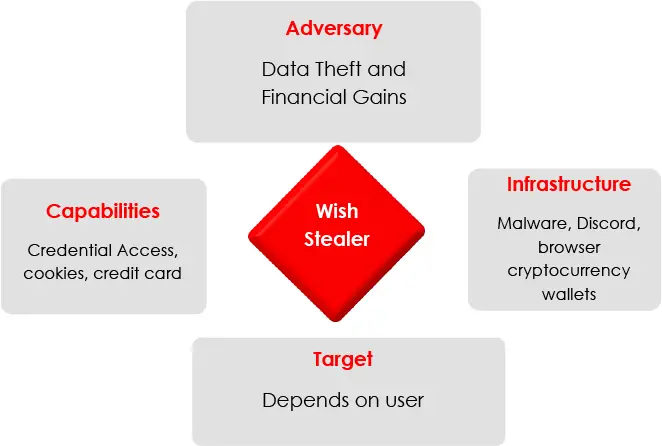
CYFIRMA recently identified “Wish Stealer,” a new Node.js-based malware that targets Windows users by stealing sensitive information from Discord, web browsers, cryptocurrency wallets, and social media accounts. This advanced malware exploits session hijacking, clipboard manipulation, and privilege escalation, making it a potent threat for individuals and organizations alike. According to CYFIRMA, “Wish Stealer can access user sessions and extract a wealth of personal data”, emphasizing the malware’s ability to infiltrate multiple applications.
Wish Stealer operates stealthily, starting with a console-hiding function to avoid detection on infected systems. The malware’s main functions are organized in modular folders, each dedicated to a specific task. CYFIRMA reports that “the stealer operates efficiently and silently on the victim’s system, beginning with the hideConsole function to run the program without detection.” It is especially dangerous for cryptocurrency users, as it continuously monitors the clipboard and replaces any copied cryptocurrency addresses with the hacker’s address. This can lead to significant financial loss, as unsuspecting users send funds directly to malicious accounts.
In addition to targeting cryptocurrency, the malware extracts browser-stored credentials and cookies from popular Chromium-based browsers like Chrome and Edge. CYFIRMA notes that “the stealer will further decrypt and send to the attacker’s Discord Webhook”, allowing attackers to gain easy access to sensitive user accounts without needing passwords or bypassing two-factor authentication.
Once Wish Stealer has gathered its data, it bundles the stolen information into a ZIP file, “wish.zip,” and uploads it to a remote server via the gofile.io API. CYFIRMA explains, “Once the upload is complete, it sends the download link for the files to the hacker’s Discord server”, making it nearly impossible for victims to track or recover their stolen data. The malware also ensures persistence by copying itself to a hidden system folder and registering in the Windows Registry.
CYFIRMA’s research found that a threat actor group on Discord has been actively promoting Wish Stealer, with activity on their channel starting in September 2024. The malware’s promotion by groups like “Aurita Stealer” suggests a growing interest in selling advanced tools that exploit user trust and platform vulnerabilities. CYFIRMA emphasizes that “it is crucial for organizations to enhance security protocols and for users to stay vigilant” against emerging malware like Wish Stealer.