WordPress Phishing Scam Exploits Fake CVE-2023-45124 Vulnerability
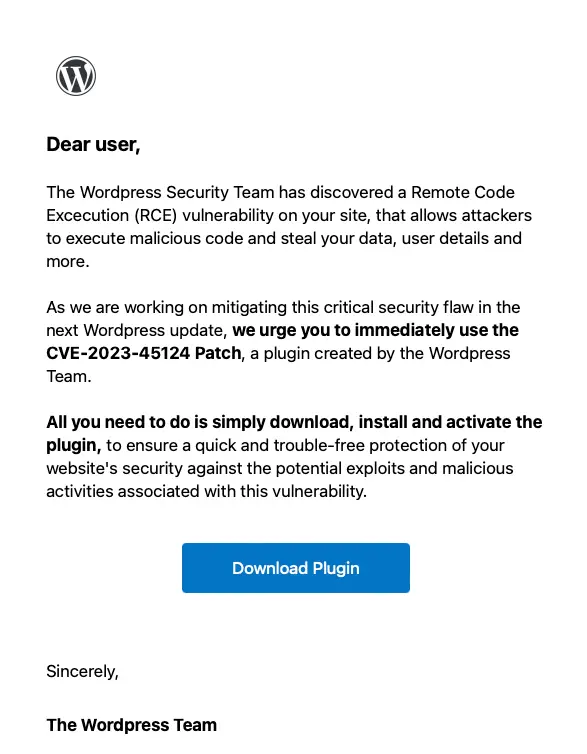
In the ever-evolving world of cybersecurity, vigilance is paramount. Recently, a cunning phishing scam has emerged, targeting unsuspecting WordPress users with a fabricated security flaw, CVE-2023-45124. This sophisticated ruse, uncovered by the Wordfence Threat Intelligence Team.
At first glance, the phishing email appears legitimate, purporting to be from the WordPress team itself. It warns of a remote code execution vulnerability on the user’s site, citing the non-existent CVE-2023-45124. The real hook, however, is the solution offered – a “patch” plugin that promises to secure the site.

Image: Wordfence
The download link in the email redirects victims to an impressively authentic-looking fake landing page, masquerading under the domain en-gb-wordpress[.]org. Here, the trap is sprung. Users are coaxed into downloading and installing the plugin, believing they are fortifying their website’s defenses.
The installed plugin, however, harbors a sinister secret. Under the guise of ‘wpress-security-wordpress’, it covertly adds a malicious administrator user named ‘wpsecuritypatch’ to the WordPress site. This rogue user, remaining hidden from view, sends its URL and a generated password back to a command-and-control domain, establishing a foothold for the attackers.
The insidious nature of this scam doesn’t stop there. The plugin also fetches a separate backdoor file, ‘wp-autoload.php’, from the same evil domain, placing it in the site’s webroot. This file has nefarious capabilities, including a file manager, SQL client, PHP console, command line terminal, and detailed environment information.
These tools grant attackers sweeping control over the WordPress site and the web user account on the server. More alarmingly, they maintain this control stealthily, ensuring persistent, undetected access.
The Wordfence team has identified several indicators of compromise. These include the presence of the ‘wp-autoload.php’ file in the webroot, the wpress-security-wordpress plugin, the hidden admin user, and interactions with the malicious domains.
Wordfence has responded promptly, updating its systems to recognize and counter this threat. They urge all WordPress users to be wary of phishing emails and refrain from downloading or installing suspicious plugins.





