Infection chain | Image Credit:
Detected by eSentire’s Threat Response Unit (TRU) in November 2023, WorkersDevBackdoor malware has been impacting the business services industry with its cunning distribution and destructive capabilities.
The WorkersDevBackdoor spreads through malicious online advertisements, tricking users into downloading it by masquerading as legitimate software. Once installed, it operates covertly, collecting sensitive information and providing backdoor access to the infected system.
The initial infection occurs via a drive-by download from a deceptive website. The malware employs the Nullsoft Scriptable Install System (NSIS) for installation, with the installation script checking system parameters before executing malicious actions.

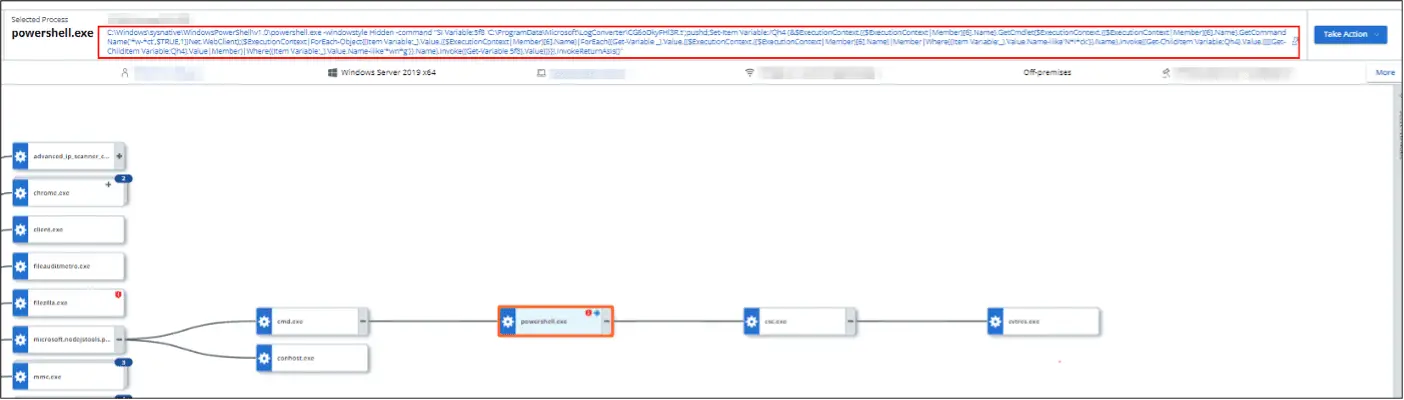
The malware sets up persistence through registry modifications and utilizes encrypted files and sophisticated scripts. This includes a PowerShell command, which plays a crucial role in the infection process.
“The backdoor also has keylogger functionality and retrieves the title of the currently active window (Figure 11). The captured input is then base64-encoded and appended with the GUID parameter of the infected host along with the string “userinput”,” the researcher wrote.
With its deceptive distribution method and stealthy operation, WorkersDevBackdoor represents a significant threat to organizations globally. Its ability to bypass conventional security measures makes it a formidable challenge for cybersecurity professionals.
The emergence of the WorkersDevBackdoor malware is a reminder of the importance of constant vigilance in the digital space. Organizations must adopt proactive security strategies to identify and neutralize such threats before they inflict damage.