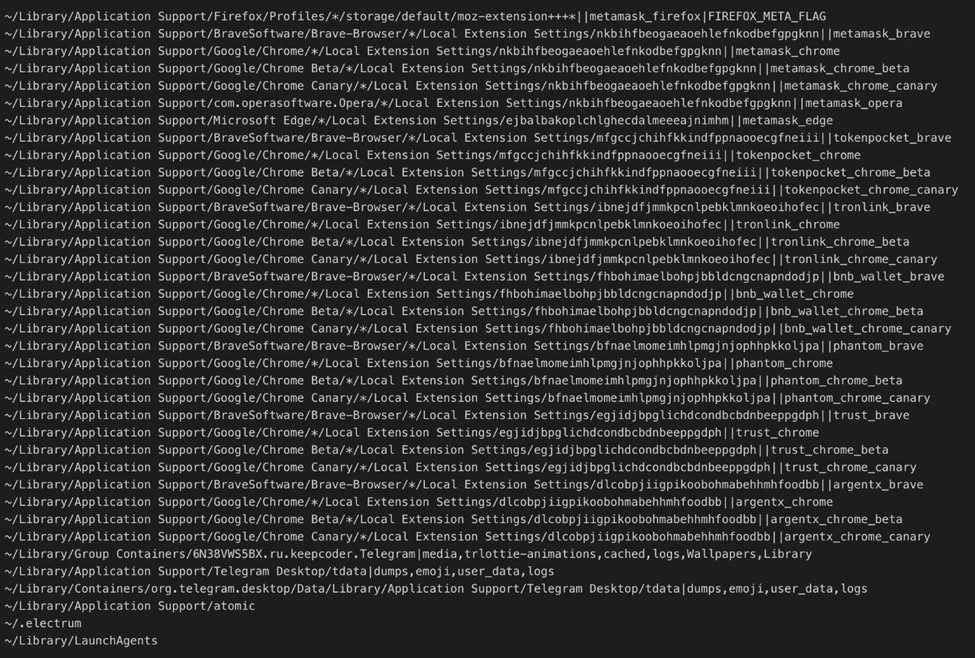
Path list received from C2 server | Image: Microsoft
Microsoft Threat Intelligence has discovered a new variant of the XCSSET malware, a sophisticated threat targeting macOS developers. This new variant, the first observed since 2022, exhibits enhanced obfuscation, persistence mechanisms, and infection strategies, posing a significant risk to Xcode projects and macOS users.
XCSSET is known for infecting Xcode projects, the development environment for Apple and macOS applications. The malware typically spreads through shared project files, leveraging the collaborative nature of software development.
This new variant is characterized by its modular approach, encoded payloads, and improved error handling. It heavily utilizes scripting languages, UNIX commands, and legitimate binaries to maintain a low profile and evade detection.
“At the code level, the new XCSSET variant obfuscated its module names, making it difficult to determine the modules’ intent during static analysis,” the report states. The malware also employs randomized payload generation and encoding, incorporating both hexdump and Base64 encoding techniques.
The new XCSSET variant follows a four-stage infection chain:
-
Xcode Shell Payload: The infection begins when a user builds an infected Xcode project. The obfuscated payload downloads and executes the next stage from the command-and-control (C2) server.
-
Obfuscated Shell Command: This stage collects device information and sends it to the C2 server, which then delivers an additional payload for execution.
-
Downloaded Shell Payload: This stage checks the XProtect version, terminates specific processes, and establishes persistence by creating a hidden file and a fake Launchpad application.
-
AppleScript Payload: The final stage involves the execution of the fake Launchpad application, which runs a series of sub-modules to steal data, establish persistence, and download additional modules.
The new XCSSET variant employs three distinct persistence techniques:
-
zshrc: The malware modifies the
.zshrcfile to execute its payload whenever a new shell session is created. -
Dock: The malware creates a fake Launchpad application that launches its payload whenever the user clicks the Launchpad icon in the Dock.
-
Git: The malware infects the pre-commit hooks within the
.gitdirectory of projects, executing its payload upon each commit action.
The new XCSSET variant includes various sub-modules designed to perform malicious activities, such as:
-
Stealing system information: The malware collects and exfiltrates system information, including macOS version, Safari version, user locale, firewall status, and CPU information.
-
Listing browser extensions: The malware identifies and lists all installed browser extensions.
-
Stealing digital wallet data: The malware targets cryptocurrency wallet extensions, stealing sensitive data such as login credentials and financial information.
-
Stealing notes: The malware exfiltrates notes from the Notes application.
-
Infecting Xcode projects: The malware infects Xcode projects by injecting malicious payloads into project files.
Microsoft has shared its findings with Apple, and developers and users are advised to take precautions to protect themselves from this threat. Some recommendations include:
-
Keeping Xcode and macOS updated to the latest versions.
-
Being cautious when opening Xcode projects from unknown or untrusted sources.
-
Using a reliable security solution to detect and prevent malware infections.
-
Regularly backing up Xcode projects and other important data.