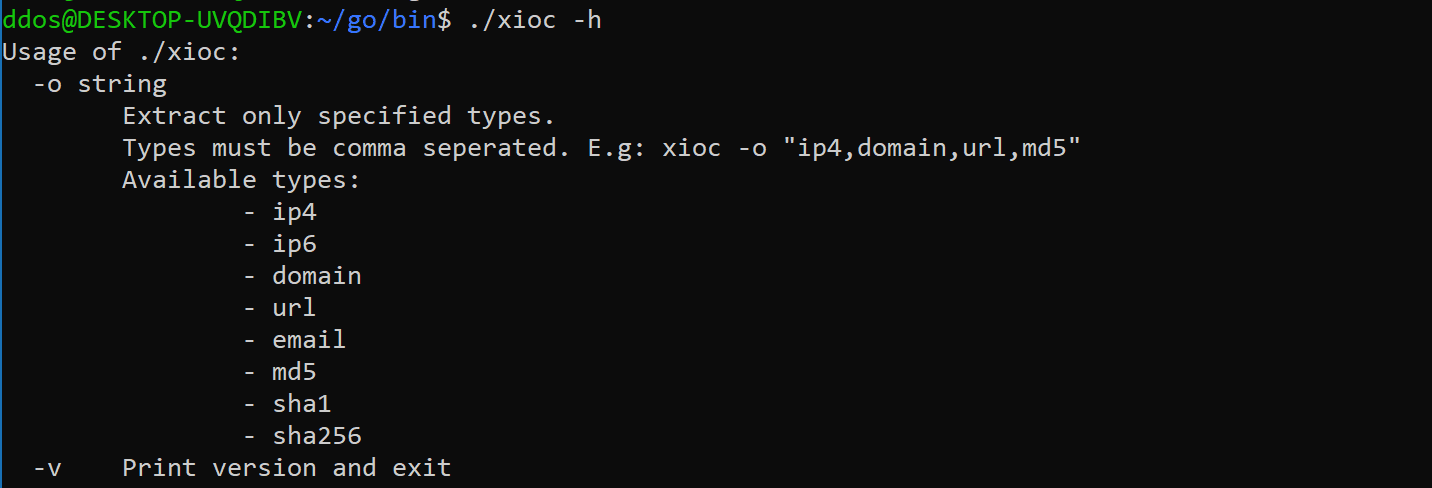
xioc
Extract indicators of compromise from the text, including “escaped” ones like hxxp://banana.com, 1.1.1[.]1, and phish at malicious dot com.
Features
- Extract IOCs (indicators of compromise) from an input text:
- IPv4
- IPv6
- Domain
- URL
- MD5
- SHA1
- SHA256
- Translate some kinds of “escaping”/”defanging” techniques:
- (dot), [dot], (.), [.], {.} to ..
- (at), [at], (@), [@], {@} to @.
- hxxp, hzzzp, hxxxp, hXXp, h__p, h**p to http.
- Command line interface
- Go library
Install
go get -u github.com/assafmo/xioc
Use
Copyright (c) 2019 Assaf Morami
Source: https://github.com/assafmo/