Xlab-Qianxin Unveils Mirai.TBOT: A Dangerous Evolution of Mirai Botnet
The Mirai botnet first emerged in 2016, a formidable threat in the digital landscape. It infiltrated the Internet of Things (IoT) by exploiting weak passwords and vulnerabilities in devices. Once a device succumbed to this malware, it became a part of a vast network controlled by attackers, primarily used for large-scale Distributed Denial of Service (DDoS) attacks.
Recently, security researchers from xlab-qianxin detected Mirai.TBOT, a variant of the original Mirai, operates with distinct characteristics. It organizes infected bots into over 100 groups based on the method of infection or device type. This organization allows attackers to manage and control their network more effectively. The botnet is notable for its:
- 0day Capability: Ability to exploit previously unknown vulnerabilities.
- Custom Domain Usage: Utilizing OpenNIC custom domains for Command and Control (C2) servers.
- Massive Scale: As of November 2023, Mirai.TBOT has an active daily count of over 30,000 bot IPs.
Mirai.TBOT retained much of the original Mirai’s code, with identical operational logic and network protocols. Notably, it conducts Telnet scans and executes commands like ‘/bin/busybox hostname TBOT’, marking its territory. Attack commands are cleverly embedded and diversified, targeting a range of IoT devices.
The botnet uses a range of vulnerabilities for infection, including two confirmed 0 days and several undisclosed exploits. Its method of infection is sophisticated, involving SSH/Telnet weak password exploitation and leveraging known vulnerabilities in routers, gateways, DVRs, and more. The specific vulnerability list is as follows:
| VULNERABILITY | AFFECTED |
|---|---|
| SSH_Weak_Password | |
| Telnet_Weak_Password | |
| CNVD-2022-91376 | BLINK Router |
| CVE-2014-8361 | Realtek SDK Miniigd SOAP |
| CVE-2014-9118 | Zhone Technologies Znid GPON |
| CVE-2015-2051 | D-Link DIR-645 |
| CVE-2016-10372 | Eir D1000 |
| CVE-2016-20016 | MV POWER CCTV DVR |
| CVE-2017-17215 | Huawei HG532 Router |
| CVE-2017-5259 | Cambium Networks cnPilot |
| CVE-2018-14558 | Tenda AC7、AC9、AC10 |
| CVE-2019-19356 | Netis WF2419 |
| CVE-2020-25499 | Totolink TOTOLINK A3002RU Router |
| CVE-2020-8515 | DrayTek Vigor2960、Vigor3900、Vigor300B Router |
| CVE-2020-8949 | Gocloud Router |
| CVE-2020-9054 | ZyXEL NAS |
| CVE-2021-22205 | GitLab |
| CVE-2013-3307 | Linksys X3000 Router |
| CVE-2021-28151 | Hongdian H8922 Router |
| CVE-2021-35394 | Realtek AP-Router SDK |
| CVE-2022-30525 | Zyxel Firewall |
| CVE-2023-26801 | LB-LINK BL-AC1900_2.0 v1.0.1、LB-LINK BL-WR9000 v2.4.9、LB-LINK BL-X26 v1.2.5、LB-LINK BL-LTE300 |
| CVE-2018-16752 | Linknet LW-N605R Router |
| CVE-2017-18368 | Zyxel P660HN-T1A Router |
| CVE-2018-10561 | Dasan GPON home routers |
| LILIN_DVR_RCE | LILIN DVR |
| Linksys_Router_unblock_RCE | Linksys E-series Router |
| OptiLink_ONT1GEW_GPON_Router_RCE | OptiLink ONT1GEW GPON |
| TVT_OEM_API_RCE | TVT DVR |
| YARN_API_RCE | Haddop Yarn API |
| 0day 1 | NVR |
| 0day 2 | Router |
| Unknown 3 | DVR |
| Unknown 4 | NVR |
| Unknown 5 | Router |

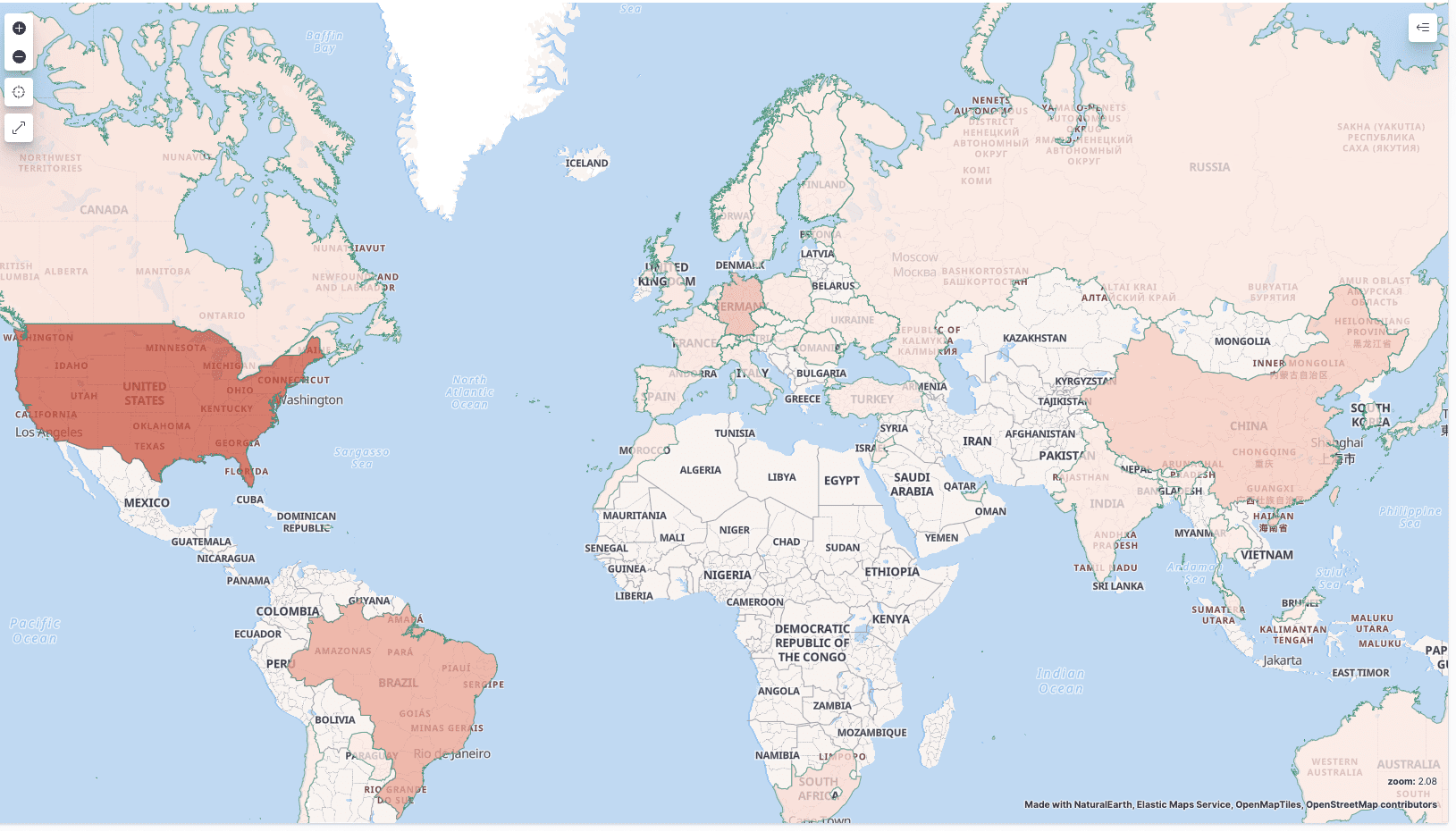
The geographical distribution of the victims of the attack
The global spread of Mirai.TBOT is alarmingly vast, with significant infections in China, Venezuela, India, Korea, Brazil, and Japan. Intriguingly, certain bot groups are exclusively found in specific regions, hinting at a targeted approach to its proliferation.
Mirai.TBOT’s evolution showcases the continuous threat posed by botnets in the ever-expanding IoT domain. Its ability to adapt and exploit emerging vulnerabilities makes it a persistent menace. Organizations and individuals alike must remain vigilant, updating security practices to fend off such advanced cyber threats.
The rise of Mirai.TBOT from its Mirai roots reflects the dynamic and hazardous nature of cybersecurity threats in the modern world. As we embrace more connected devices, the shadow of such botnets looms large, prompting a need for robust, proactive defense mechanisms in the digital realm. The story of Mirai.TBOT is not just a tale of a cyber threat; it’s a wake-up call to the vulnerabilities inherent in our interconnected world.