XLL Phishing: specifically crafted for Microsoft Excel
XLL_Phishing
Introduction
With Microsoft’s recent announcement regarding the blocking of macros in documents originating from the internet (email AND web download), attackers have begun aggressively exploring other options to achieve user-driven access (UDA). There are several considerations to be weighed and balanced when looking for a viable phishing access method:
- Complexity – The more steps that are required on the user’s part, the less likely we are to be successful.
- Specificity – Are most victim machines susceptible to your attack? Is your attack architecture-specific? Does certain software need to be installed?
- Delivery – Are there network/policy mitigations in place on the target network that limit how you could deliver your maldoc?
- Defenses – Is application whitelisting enforced?
- Detection – What kind of AV/EDR is the client running?
These are the major questions, however, there are certainly more. Things get more complex as you realize that these factors compound each other; for example, if a client has a web proxy that prohibits the download of executables or DLL’s, you may need to stick your payload inside a container (ZIP, ISO, etc). Doing so can present further issues down the road when it comes to detection. More robust defenses require more complex combinations of techniques to defeat.
This article will be written with a fictional target organization in mind; this organization has employed several defensive measures including email filtering rules, blacklisting certain file types from being downloaded, application whitelisting on endpoints, and Microsoft Defender for Endpoint as an EDR solution.
Real organizations may employ none of these, some, or even more defenses which can simplify or complicate the techniques outlined in this research. As always, know your target.
What is XLL’s?
XLL’s are DLL’s, specifically crafted for Microsoft Excel. To the untrained eye, they look a lot like normal excel documents.

XLL’s provide a very attractive option for UDA given that they are executed by Microsoft Excel, a very commonly encountered software in client networks; as an additional bonus because they are executed by Excel, our payload will almost assuredly bypass Application Whitelisting rules because a trusted application (Excel) is executing it. XLL’s can be written in C, C++, or C# which provides a great deal more flexibility and power (and sanity) than VBA macros which further makes them a desirable choice.
The downside of course is that there are very few legitimate uses for XLL’s, so it SHOULD be a very easy box to check for organizations to block the download of that file extension through both email and web download. Sadly many organizations are years behind the curve and as such XLL’s stand to be a viable method of phishing for some time.
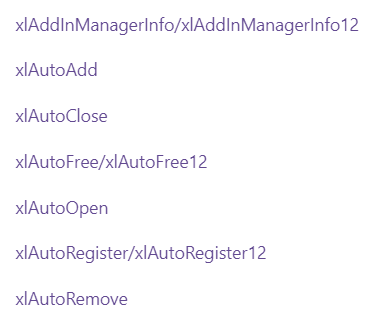
There are a series of different events that can be used to execute code within an XLL, the most notable of which is xlAutoOpen. The full list may be seen here:
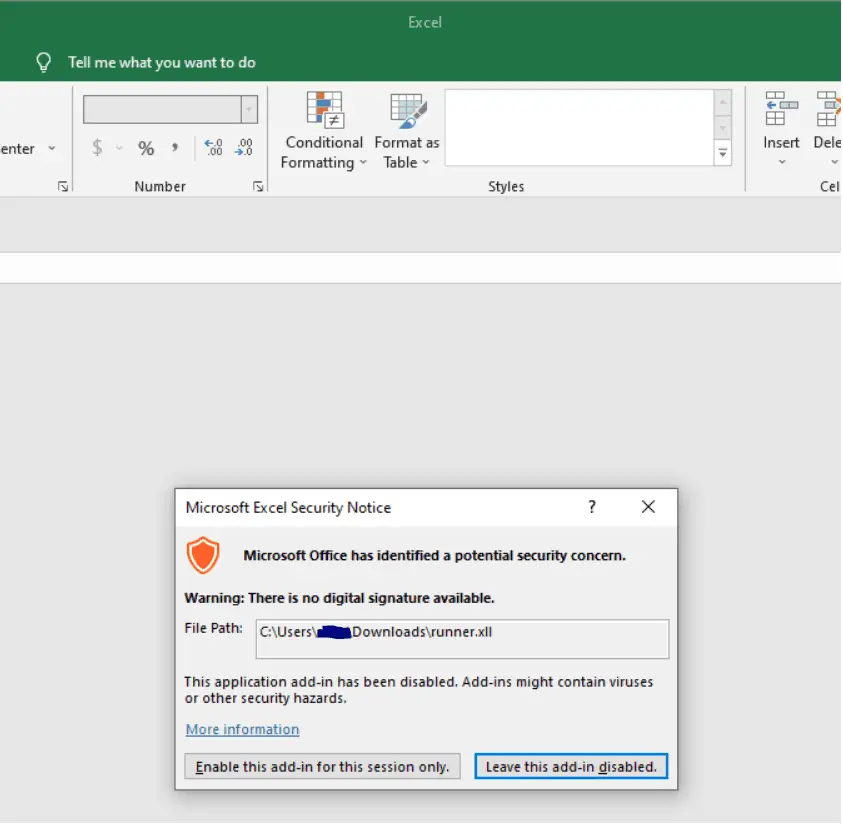
Upon double-clicking an XLL, the user is greeted by this screen:

This single dialog box is all that stands between the user and code execution; with fairly thin social engineering, code execution is all but assured.
Something that must be kept in mind is that XLL’s, being executables, are architecture specific. This means that you must know your target; the version of Microsoft Office/Excel that the target organization utilizes will (usually) dictate what architecture you need to build your payload for.
There is a pretty clean break in Office versions that can be used as a rule of thumb:
Office 2016 or earlier: x86
Office 2019 or later: x64
It should be noted that it is possible to install the other architecture for each product, however, these are the default architectures installed and in most cases, this should be a reliable way to make a decision about which architecture to roll your XLL for. Of course, depending on the delivery method and pretexting used as part of the phishing campaign, it is possible to provide both versions and rely on the victim to select the appropriate version for their system.
Install & Use
Copyright (c) 2022 Octoberfest7





