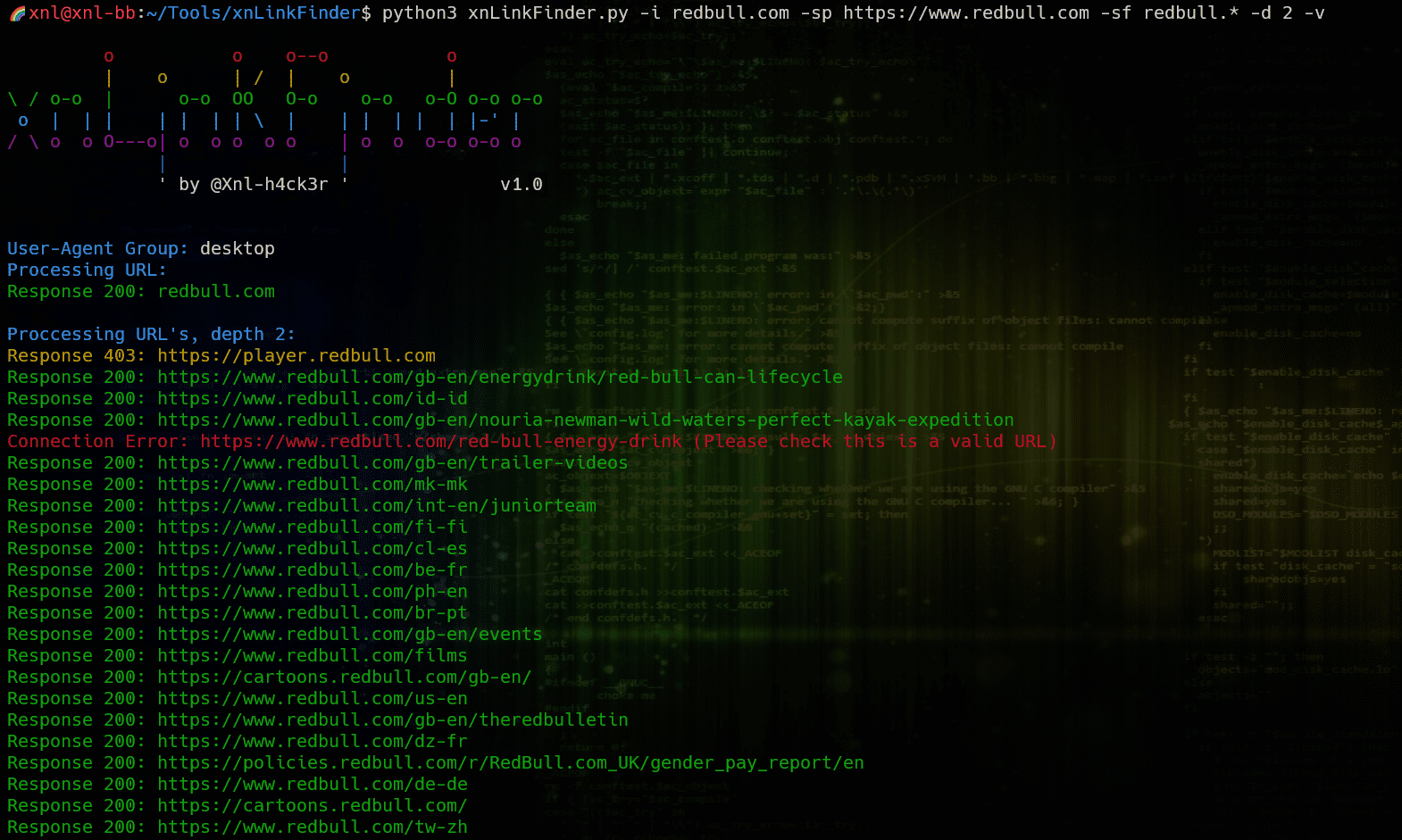
xnLinkFinder
This is a tool used to discover endpoints for a given target. It can find them by:
- crawling a target (pass a domain/URL)
- crawling multiple targets (pass a file of domains/URLs)
- searching files in a given directory (pass a directory name)
- get them from a Burp project (pass the location of a Burp XML file)
- get them from an OWASP ZAP project (pass location of a ZAP ASCII message file)

The python script is based on the link-finding capabilities of my Burp extension GAP. As a starting point, I took the amazing tool LinkFinder by Gerben Javado, and used the Regex for finding links, but with additional improvements to find even more.
Install
$ git clone https://github.com/xnl-h4ck3r/xnLinkFinder.git
$ cd xnLinkFinder
$ python setup.py install
Use
config.yml
The config.yml file has the keys which can be updated to suit your needs:
- linkExclude – A comma-separated list of strings (e.g..css,.jpg,.jpeg etc.) that all links are checked against. If a link includes any of the strings then it will be excluded from the output. If the input is a directory, then file names are checked against this list.
- contentExclude – A comma-separated list of strings (e.g. text/css,image/jpeg,image/jpg etc.) that all responses Content-Type headers are checked against. Any responses with these content types will be excluded and not checked for links.
- regexFiles – A list of file types separated by a pipe character (e.g. php|php3|php5 etc.). These are used in the Link Finding Regex when there are findings that aren’t obvious links but are interesting file types that you want to pick out. If you add to this list, ensure you escape any dots to ensure the correct regex, e.g. js\.map
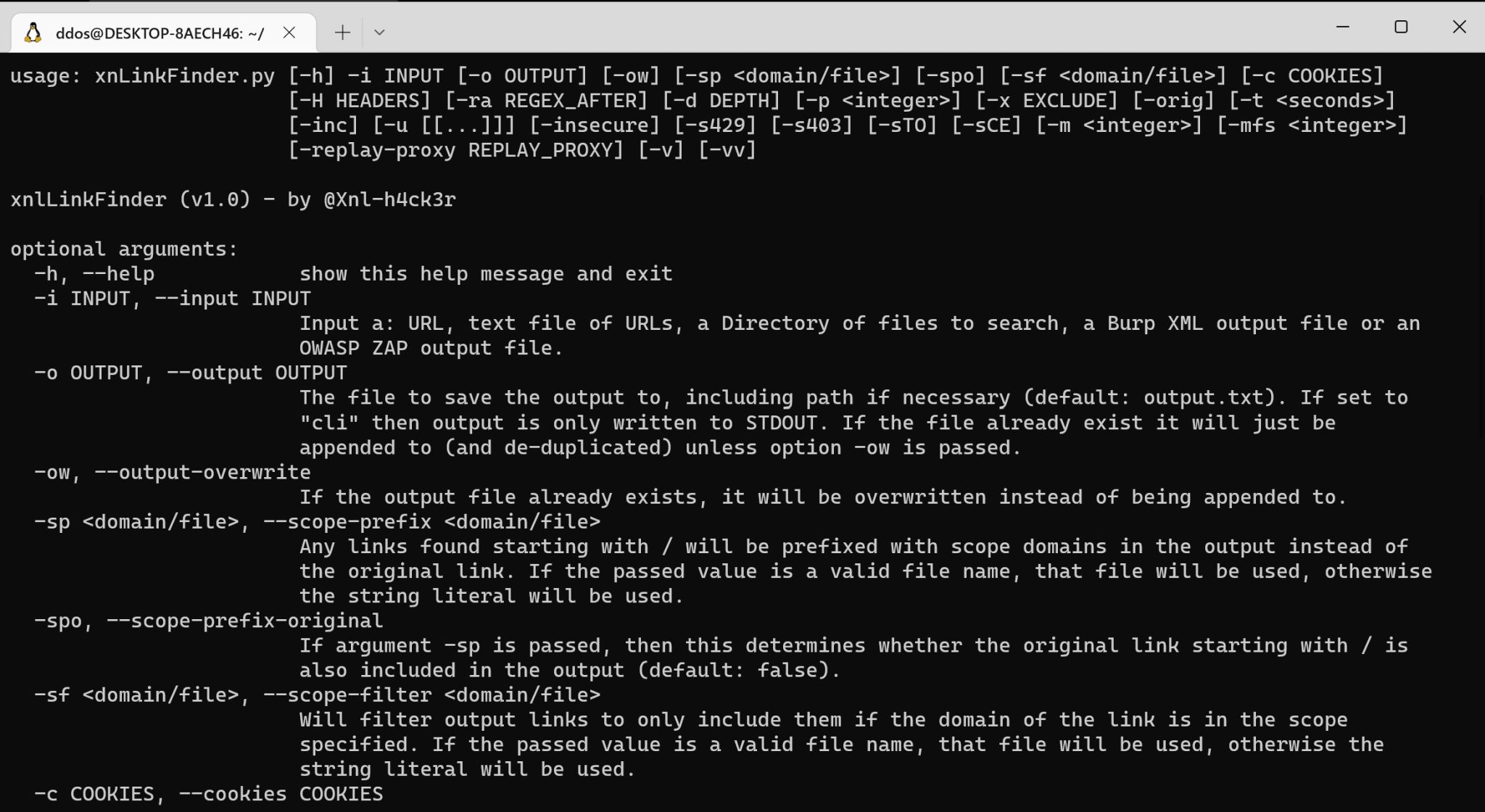
Tutorial
Copyright (c) 2022 /XNL-h4ck3r