XSpear v1.4.1 releases: Powerfull XSS Scanning and Parameter Analysis tool
XSpear
XSpear is XSS Scanner on ruby gems
Key features
- Pattern matching based XSS scanning
- Detect
alertconfirmpromptevent on headless browser (with Selenium) - Testing request/response for XSS protection bypass and reflected(or all) params
- Reflected Params
- All params(for blind xss, anytings)
- Filtered test
event handlerHTML tagSpecial CharUseful code
- Testing Blind XSS (with XSS Hunter , ezXSS, HBXSS, Etc all url base blind test…)
- Dynamic/Static Analysis
- Find SQL Error pattern
- Analysis Security headers(
CSPHSTSX-frame-options,XSS-protectionetc.. ) - Analysis Other headers..(Server version, Content-Type, etc…)
- XSS Testing to URI Path
- Scanning from Raw file(Burp suite, ZAP Request)
- XSpear running on ruby code(with Gem library)
- Show
table base cli-reportandfiltered rule,testing raw query(url) - Testing at selected parameters
- Support output format
clijson- cli: summary, filtered rule(params), Raw Query
- Support Verbose level (0~3)
- 0: quite mode(only result)
- 1: show scanning status(default)
- 2: show scanning logs
- 3: show detail log(req/res)
- Support custom callback code to any test various attack vectors
- Support Config file
Changelog v1.4.1
- Patch CVE-2020-8130 (modify dependency version)
Installation
gem install XSpear
Use
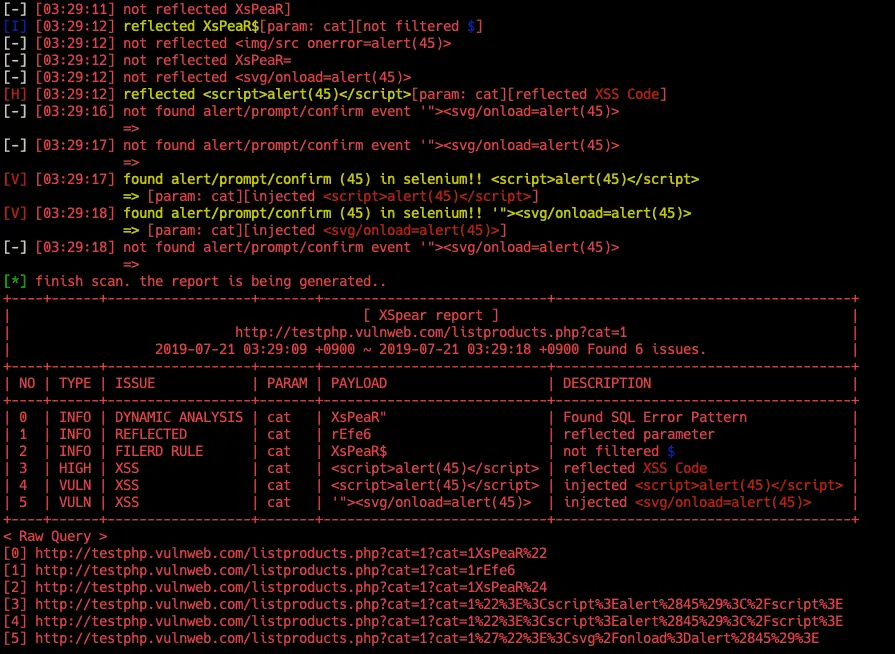
Result types
- (I)NFO: Get information ( e.g sql error, filtered rule, reflected params, etc..)
- (V)UNL: Vulnerable XSS, Checked alert/prompt/confirm with Selenium
- (L)OW: Low-level issue
- (M)EDIUM: medium level issue
- (H)IGH: high-level issue
Example
Scanning XSS
$ xspear -u "http://testphp.vulnweb.com/search.php?test=query" -d "searchFor=yy"
json output
$ xspear -u "http://testphp.vulnweb.com/search.php?test=query" -d "searchFor=yy" -o json -v 1
detail log
$ xspear -u "http://testphp.vulnweb.com/search.php?test=query" -d "searchFor=yy" -v 3
testing at selected parameters
$ xspear -u "http://testphp.vulnweb.com/search.php?test=query&cat=123&ppl=1fhhahwul" -p cat,test
Copyright (c) 2019 hahwul
Source: https://github.com/hahwul/





